The Rise of Passwordless Authentication

In the digital age, securing online identities has become a paramount concern for individuals and organizations alike. As cyber threats evolve, so too must our methods of defense. Enter passwordless authentication solutions, such as passkeys, which are rapidly gaining traction due to several compelling advantages: 1. Enhanced Security: Unlike traditional passwords, passkeys do not carry the risk of being intercepted or reused across different services, thereby reducing the overall threat surface. 2. User Convenience: These modern authentication methods eliminate the need for users to remember complex passwords, offering a more streamlined and user-friendly experience. 3. Compliance and Control: Passwordless authentication systems often come with better controls for compliance and user management, providing organizations with more robust oversight of security protocols. The adoption rates of passwordless authentication have witnessed a significant surge in recent years. Statistics indicate that by 2022, passwordless adoption was estimated at over 65% globally, suggesting a widespread shift towards more secure authentication practices. This trend is further bolstered by favorable user acceptance rates, as passwordless solutions offer a more convenient login process compared to traditional password-based systems. Despite the benefits, the uptake of passwordless authentication is slowed down by factors such as the incumbent inertia of existing password systems, the need for widespread user education, and the integration complexities with current IT infrastructures. Conclusion As we navigate the cybersecurity landscape of 2024, the rise of passwordless authentication presents a promising opportunity to enhance security and user experience simultaneously. Organizations that proactively embrace this trend and seamlessly integrate passwordless solutions into their authentication strategies will undoubtedly gain a competitive advantage in safeguarding their digital assets and fostering a more secure online environment. Embrace the future of cybersecurity and upgrade your defenses today. Contact us now for a free consultation.
What the Constant Evolution of E-payments Affect How You Do Cybersecurity & Compliance

City & Financial Global recently hosted its third annual Payments Regulation and Innovation Summit. They successfully brought together industry leaders to critically discuss the evolving payments landscape. The future of e-payments, fintech, and digital currencies emerged as one of the central themes at the summit, reflecting the constant evolution of our digital economy. TrustNet, a leading provider of cybersecurity and compliance services, strongly emphasizes the importance of robust security protocols and strict regulatory compliance in our rapidly digitizing world. As e-payment technologies continue to evolve at a breakneck pace, TrustNet underlines the need for businesses to prioritize cybersecurity measures and adhere rigorously to regulatory standards. The Pros and Cons of E-Payments for Companies and Businesses The digital revolution has significantly shifted how companies and businesses transact, making e-payments increasingly prevalent. Here, we explore the advantages and disadvantages of adopting e-payments. Advantages of E-Payments — Convenience: E-payments provide an easy and quick alternative to traditional cash or check transactions. With just a few clicks on a computer or smartphone, transactions can be completed anytime, anywhere. — Security: E-payments offer a higher level of security than conventional payment methods. Transactions are encrypted and processed securely, minimizing the risk of fraud and theft. — Speed: E-payments are processed swiftly, often within seconds, making them ideal for time-sensitive transactions. — Reduced Costs: E-payments can be more cost-effective than traditional methods. They eliminate the need for paper checks and postage expenses and can lower the fees related to wire transfers. — Accessibility: E-payments are available to people who may not have access to traditional banking systems, including those in remote or underbanked areas. Talk to our experts today! Disadvantages of E-Payments — Technical Issues: As e-payments depend on technology, they are susceptible to glitches, server outages, and other technical problems. Such issues can result in transaction delays or failures. — Security Risks: Despite the generally high security of e-payments, there is always a risk of fraud and theft. Cybercriminals can employ various methods to steal payment information, including phishing scams and malware. — Limited Consumer Protection: E-payments may not offer the same level of consumer protection as traditional methods. For instance, obtaining a refund for an erroneous payment can be challenging. — Fees: Some e-payment systems may charge transaction fees, depending on the payment method and amount. — Dependence on Internet Access: E-payments require Internet access and thus may not be available in areas where Internet connectivity is limited or unreliable. Understanding the pros and cons of e-payments can help businesses make informed decisions about whether to adopt this transaction method. When evaluating these factors, it’s crucial to consider the nature of the company, its target market, and operational needs. If you want to dive deeper into digital transactions, we’re here Hereto guide you Exploring Cybersecurity and Compliance Risks Associated with E-Payments The advent of e-payments also comes with cybersecurity and compliance risks that organizations must navigate. Threat Management Threat management is a critical aspect of any cybersecurity strategy. In the context of e-payments, threat management involves identifying potential cyber threats, assessing their potential impact, and taking measures to mitigate them. This can include everything from installing robust firewalls to conducting regular penetration tests. PCI DSS The Payment Card Industry Data Security Standard (PCI DSS) is a set of security standards designed to ensure that companies that accept, process, store, or transmit credit card information maintain a secure environment. Non-compliance can result in hefty fines and worse, a data breach can lead to reputational damage and loss of customer trust. SOC System and Organization Controls (SOC) are standards designed to help measure how well a given service organization conducts and regulates its information. For e-payments, SOC 2 compliance is particularly relevant as it focuses on a business’s non-financial reporting controls relating to a system’s security, availability, processing integrity, confidentiality, and privacy. ISO 27001 ISO 27001 is an international standard for managing information security. It provides a framework for establishing, implementing, maintaining, and continually improving an information security management system. This is crucial for e-payment systems where sensitive financial information is constantly processed and stored. It’s important to note that these are just some steps a company can take to manage cybersecurity and compliance risks associated with e-payments. These risks are evolving, so staying vigilant and proactive is vital to maintaining a secure e-payment environment. Navigating the E-Payment Revolution: A Balancing Act of Innovation and Security E-payments are evolving at a rapid pace, bringing a host of opportunities and challenges. On one hand, integrating e-payment systems into an increasing number of services has made transactions more convenient and efficient than ever before. On the other hand, this growing reliance on digital payments has also amplified their cybersecurity risks. Being proactive in addressing potential threats enhances a company’s standing among stakeholders and bolsters its overall integrity. It shows that the organization is not just riding the wave of digital transformation but is also mindful of the inherent risks and is taking the necessary steps to mitigate them. By partnering with TrustNet, businesses can confidently navigate the rapidly evolving digital landscape, knowing that their e-payment systems are efficient, convenient, secure, and compliant. Embrace the future of cybersecurity and upgrade your defenses today. Contact us now for a free consultation.
Predicting the Future: TrustNet’s Cybersecurity Predictions for 2024

As we advance deeper into the digital age, predicting the future of cybersecurity becomes not just a speculative exercise but a necessity. This is precisely what TrustNet aims to do with its Cybersecurity Predictions for 2024. In this article, we will explore TrustNet’s predictions regarding the critical role of SOC 2 in the cybersecurity landscape. As organizations increasingly rely on cloud services and third-party vendors, SOC 2 compliance becomes an essential benchmark for security and privacy. Prepare to dive into a future where cybersecurity isn’t just about protection but also about anticipation and strategic planning. What is SOC 2? SOC 2, established by the American Institute of Certified Public Accountants (AICPA), is a compliance framework that sets standards for managing customer data. Compliance is evaluated based on five Trust Services Criteria: security, availability, processing integrity, confidentiality, and privacy. Achieving SOC 2 compliance signifies that a company has robust data protection measures in place and adheres to them consistently and effectively. It’s not just about ticking boxes; it’s about setting up and maintaining stringent data protection standards that foster confidence with customers and stakeholders. Initially, SOC 2 audits focused primarily on physical and technical controls. However, with the rise of cloud services and third-party vendors, it became apparent that more comprehensive oversight and robust data management controls were needed. This shift led to the evolution of SOC 2 into a more encompassing framework. It no longer focuses solely on security but also considers a system’s availability, processing integrity, confidentiality, and privacy. This holistic approach makes SOC 2 an indispensable asset for businesses in today’s digital landscape. For more on our SOC 2 compliance services Click Here The Five Trust Service Principles of SOC 2 SOC 2 Compliance is structured on five core “trust service principles,” namely security, availability, processing integrity, confidentiality, and privacy. Security. Information and systems are protected against unauthorized access, unauthorized disclosure of information, and damage to systems that could compromise the availability, integrity, confidentiality, and privacy of information or systems and affect the entity’s ability to achieve its objectives. Security refers to the protection of information during its collection or creation, use, processing, transmission, and storage, and systems that use electronic information to process, transmit, transfer, and store information to enable the entity to meet its objectives. Controls over security prevent or detect the breakdown and circumvention of segregation of duties, system failure, incorrect processing, theft or other unauthorized removal of information or system resources, misuse of software, and improper access to or use of, alteration, destruction, or disclosure of information. Availability. Information and systems are available for operation and use to meet the entity’s objectives. Processing Integrity. System processing is complete, valid, accurate, timely, and authorized to meet the entity’s objectives. Confidentiality. Information designated as confidential is protected to meet the entity’s objectives. Confidentiality addresses the entity’s ability to protect information designated as confidential from its collection or creation through its final disposition and removal from the entity’s control in accordance with management’s objectives. Privacy. Personal information is collected, used, retained, disclosed, and disposed of to meet the entity’s objectives. Talk to our experts today! How SOC 2 Enhances Cybersecurity SOC 2 compliance is pivotal in enhancing a company’s cybersecurity posture. Here’s how: Robust Security Measures: SOC 2 requires companies to implement stringent security controls, which include network and web application firewalls, two-factor authentication, intrusion detection, and regular vulnerability assessments. These measures significantly bolster the company’s defense against cyber threats. Enhanced Data Protection: Complying with SOC 2 requires comprehensive data management controls. This includes encryption of sensitive data, secure data transmission, and robust access control mechanisms. It ensures that customer data is well-protected at all times. Increased Trust and Confidence: Achieving SOC 2 compliance demonstrates to customers and stakeholders that the company takes data protection seriously. This can increase trust, enhance reputation, and potentially increase business opportunities. Continuous Monitoring and Improvement: SOC 2 isn’t a one-time certification but a framework for continuously monitoring and improving security controls. Regular audits ensure that companies stay vigilant and proactive in their cybersecurity efforts. Integrating SOC 2 into your cybersecurity strategy provides a structured and comprehensive approach to data security. It helps businesses stay ahead of the curve by evolving their defenses in line with emerging threats and technological advancements. In the long run, SOC 2 compliance strengthens cybersecurity and fosters a culture of security within the organization, ensuring that data protection is everyone’s responsibility. Real-world Examples of SOC 2 Compliance Impact on Cybersecurity SOC 2 compliance plays a vital role across various sectors, particularly those that handle sensitive data. Here are some real-world examples showcasing the positive impact of SOC 2 compliance on a company’s cybersecurity measures: Information Technology (IT): In the IT sector, companies such as software service providers and data centers must demonstrate SOC 2 compliance to assure clients that their data is handled securely. Achieving SOC 2 certification boosts client trust and gives the business a competitive edge in the market. Finance: Financial institutions like banks and fintech companies are entrusted with sensitive customer data, including financial transactions and personal identification information. SOC 2 compliance is crucial for such institutions to assure customers that their financial data is securely processed and stored. Healthcare: Healthcare organizations handle vulnerable patient data, making SOC 2 compliance critical. Compliance ensures that patient data is protected and confidentiality is maintained. This is essential for healthcare providers to operate and maintain patients’ trust. E-commerce: E-commerce companies manage a significant volume of client data, encompassing transaction details and personal information. Adherence to SOC 2 standards guarantees secure storage and handling of this customer data, critical in fostering customer confidence and facilitating seamless business procedures. Education: Educational institutions and EdTech companies deal with sensitive student data. SOC 2 certification demonstrates to schools and universities that student data is handled with integrity and confidentiality. This is crucial for maintaining institutional partnerships and securing the trust of students. By integrating SOC 2 into their cybersecurity strategy, businesses from different sectors can assure their stakeholders
NIST CSF 2.0: What’s New
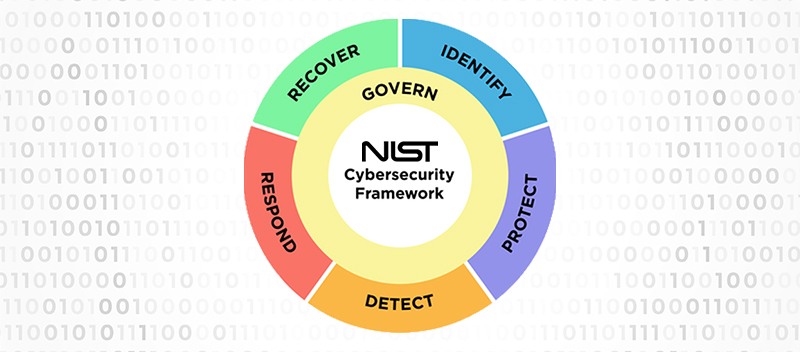
Established in 2014, the National Institute of Standards and Technology Cybersecurity Framework (NIST CSF) is a vital tool in the field of cybersecurity. The framework’s effectiveness in addressing these risks is well recognized, with many organizations affirming the efficacy of the previous version, NIST CSF 1.1. However, with the ever-evolving nature of cybersecurity threats, there is a consensus that updates are necessary to tackle current and future challenges. This has led to the development of the NIST CSF 2.0, aiming to enhance the framework while preserving its original goals and objectives. With this updated version, NIST strives to streamline the framework’s application, making it even more accessible and effective for organizations. NIST CSF 2.0 signals a significant step forward in cybersecurity management, promising to equip businesses with the necessary tools to navigate the increasingly complex cyber landscape. Understanding NIST CSF 2.0 NIST CSF 2.0 comes as a response to the significant changes in the cybersecurity landscape over the past decade. These shifts include: The evolution of cyber threats, such as the surge of multi-extortion ransomware and the growing prevalence of attacks utilizing advanced technologies like artificial intelligence (AI), machine learning, and automation. Advances in cybersecurity capabilities, including zero-trust capabilities, automation to combat cyberattacks, and secure software development. Changes in the workforce, notably the global shortage of cybersecurity professionals. Technological advancements, like the evolution of cloud services and deployment models with associated security risks and the progression of AI, machine learning, quantum computing, and encryption. Increased availability of resources to aid organizations in managing their cybersecurity risk. Despite these extensive updates, CSF 2.0 retains the original framework’s essential elements. It remains voluntary for the private sector, maintains a risk-based approach to cybersecurity, focusing on desired outcomes rather than specific controls, and retains the structure of the CSF, consisting of three main components: Core: The core of CSF organizes desired cybersecurity outcomes around five functions: identify, protect, detect, respond, and recover. CSF 2.0 introduces a sixth function: govern. These functions are the pillars of effective cybersecurity7. Tiers: The tiers of CSF describe how an organization manages its cybersecurity risk. Organizations select the tier that aligns with their goals, reduces cyber risk to an acceptable level, and is feasible to implement. Progressing from tier 1 to tier 4 signifies increasing sophistication in cyber risk management processes. Profiles: CSF profiles assist organizations in establishing a roadmap for reducing cybersecurity risk. They depict an organization’s current and target cybersecurity posture, guiding organizations in their progression from one stage to another. In essence, NIST CSF 2.0 is not a departure from its predecessor but rather an evolution, considering the changing cyber landscape and equipping organizations with the tools they need to navigate these changes effectively. Learn more about our cybersecurity and compliance services Here Key Features of NIST CSF 2.0 NIST CSF 2.0 introduces several new features and improvements that reflect the changes in the cybersecurity landscape. Here are the key features: Expanded Scope: CSF 2.0 broadens its reach beyond critical infrastructure organizations, for which the original framework was designed, to include organizations of all sizes and sectors, including small businesses. This change acknowledges the widespread adoption of the CSF beyond critical infrastructure organizations and aligns with Congress’s directive for NIST to consider the needs of small businesses within the framework. Governance: Recognizing the drastic changes in the cyber landscape over the past decade, CSF 2.0 elevates the importance of governance. It identifies cyber risk as a significant source of enterprise risk that requires the attention of senior leadership, on par with legal, financial, and other sources of enterprise risk. Supply Chain Risk Management (SCRM): CSF 2.0 acknowledges the cybersecurity risks associated with external parties or supply chains. Standard supply chain cyber risks include malware attacks, ransomware attacks, data breaches, and cybersecurity breaches. Zero-Trust Architectures (ZTA): CSF 2.0 embraces the zero-trust security model, an alternative to the traditional perimeter security model. The zero-trust model takes a “never trust, always verify” approach to security, a key element in establishing cybersecurity for the federal government. Cloud Security: CSF 2.0 recognizes the shift in cloud security from organizations managing their cloud infrastructure to third-party companies taking legal and operational responsibility for managing the cloud. Expanded Implementation Guidance: To assist organizations in achieving the cybersecurity outcomes outlined in the framework, CSF 2.0 provides expanded “implementation examples” and “informative references.” The enhancements introduced in NIST CSF 2.0 are a testament to its evolution with the changing cybersecurity landscape. Impact of NIST CSF 2.0 on Cybersecurity The NIST CSF 2.0 has introduced significant changes to the cybersecurity landscape. Its expanded scope and emphasis on governance empower organizations to improve their cybersecurity posture and reduce the risk of cyberattacks. The updated framework provides structure, standardization, and consistency in addressing cyber risks, aiding enterprises to increase compliance and manage their cyber risk effectively. Furthermore, the inclusion of Zero-Trust Architectures (ZTA) principles and focus on cloud security exhibit a proactive approach towards managing cybersecurity, enabling organizations to anticipate and mitigate threats. In real-world applications, NIST CSF 2.0 will impact Managed Service Providers (MSPs) and Managed Security Service Providers (MSSPs). They may leverage the framework’s strategies to manage cybersecurity posture better and reduce risks. Additionally, its influence extends to sectors like healthcare, where understanding and implementing the new features of NIST CSF 2.0 can significantly enhance security measures. Also, the Third Party Risk Management (TPRM) programs benefit from determining priorities and risk tolerances and assessing cybersecurity risks and impacts. In essence, NIST CSF 2.0 is instrumental in driving a more resilient and secure digital ecosystem. Implementing NIST CSF 2.0 Implementing the updates in NIST CSF 2.0 can significantly enhance an organization’s cybersecurity posture. The first step involves understanding the CSF, its components, and its principles. Organizations must thoroughly assess their cybersecurity posture, identify gaps, and develop a measurable plan for implementing the CSF. NIST aims to tackle a persistent issue that impedes the implementation of the CSF. The organization’s goal for the final 2.0 draft is to incorporate examples of implementation guidance that provide practical,
Launching a Safer Future: Meet GhostWatch and iTrust from TrustNet

TrustNet is a cybersecurity and compliance industry leader renowned for innovative and robust solutions. We are dedicated to safeguarding digital ecosystems against the evolving threats of today. With an ever-increasing reliance on technology, TrustNet is committed to developing advanced tools that ensure secure and uninterrupted digital experiences. The need for advanced cybersecurity solutions has never been more critical. With the rise of sophisticated cyber threats like ransomware, phishing scams, and data breaches, businesses and individuals are at risk. TrustNet aims to address these challenges head-on with our cutting-edge technologies, GhostWatch and iTrust, which promise to revolutionize how we perceive and handle cybersecurity and compliance. Introducing GhostWatch: An Overview of Features and Benefits GhostWatch is a premier provider of Managed Security Services, earning the trust of companies globally. Equipped with a sophisticated suite of tools, capabilities, and skilled cybersecurity experts, GhostWatch safeguards your systems against hackers, cyber offenders, and other harmful entities. In essence, GhostWatch is a comprehensive managed security solution, overseeing and securing your complete technology infrastructure from end to end. Also, GhostWatch provides Managed Compliance Services to handle the full spectrum of the compliance process, providing real-time insights at an affordable price. With hundreds of compliance assessments under our belt, GhostWatch boasts extensive experience in successfully steering, managing and upholding compliance for our clientele. Features and Benefits GhostWatch provides an array of advanced features that benefit your cybersecurity stance. Managed Security Services: — Security Monitoring: GhostWatch delivers 24/7 security monitoring to ensure constant vigilance over your digital assets. The system’s round-the-clock surveillance and essential security tools provide complete security visibility, ensuring no threat goes unnoticed. — Advanced Threat Management: With GhostWatch, your organization’s risk is minimized through its comprehensive threat management. It amalgamates threat detection, incident response, and threat management, integrated with built-in security tools and real-time threat intelligence. — Vulnerability Management: Proprietary threat intelligence identifies unknown exploits, updating in real-time to keep pace with evolving threats. GhostWatch offers quick installation, both cloud-based and on-premises, allowing for on-demand or scheduled reporting and scanning. In case of security breaches, an immediate incident response plan is prioritized. — Network Security: GhostWatch is a comprehensive network security solution integrating omnichannel management, threat protection, and unified communication into one powerful platform. — Threat Intelligence: Connected to a global community of threat researchers and security professionals, GhostWatch provides an extensive, up-to-date view of the threat landscape, sourced from over 100,000 contributors across 140 countries and 19 million daily threat indicators. — Cloud and Multi-Cloud Support: GhostWatch extends its robust security capabilities to public cloud environments, detecting and combating cyber attacks. It supports Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform installations, extending beyond just on-premises servers. — Log Management: GhostWatch’s advanced log management platform automatically correlates log data from multiple sources using integrated Security Information and Event Management (SIEM) capabilities. It regularly correlates events with real-time threat intelligence and provides frequent automatic updates, ensuring you’re always ahead of potential threats. Managed Compliance Services: — Project Management: GhostWatch assigns a dedicated compliance manager for the entirety of the project. This includes individualized consultation with experts and comprehensive responses to all your queries. — Readiness Assessment: Our experts at GhostWatch conduct an in-depth analysis and provide guidance. We carry out a gap assessment, offer a remediation roadmap, evaluate your existing controls and develop new ones. — Audit: GhostWatch facilitates pre-certification of your compliance and oversee your independent audit. — Policies and Procedures: GhostWatch sets boundaries, guidelines, and best practices, and craft customized compliance policies and procedures. — Reporting: GhostWatch ensures transparency through executive reporting and maintain compliance monitoring all year round. — Platform: GhostWatch enhances your compliance management by utilizing an intuitive, user-friendly platform to organize, standardize, and automate our tasks. Learn more about GhostWatch Here Unveiling iTrust: A Detailed Look at Its Unique Features and Benefits iTrust, by TrustNet, is a top-tier provider of cybersecurity risk rating and risk intelligence designed to assist businesses in building trustworthy associations with their vendors, partners, and suppliers. Leveraging advanced machine learning methodologies, iTrust collects and scrutinizes third-party risk metrics, providing a holistic view of vendor security and compliance. Recognized globally as one of the most sophisticated platforms for cyber risk rating and threat intelligence, iTrust is dedicated to delivering robust and actionable risk insights. Features and Benefits iTrust presents exclusive features that enable a thorough evaluation of cyber risk and compliance: — Vendor Risk Management: iTrust’s Vendor Risk Management feature offers cybersecurity risk ratings for various vendors. This aids in comprehending and managing the risks linked to each vendor partnership. — Compliance: iTrust facilitates round-the-year Compliance monitoring and tracking, aiding businesses in maintaining compliance with all relevant standards and regulations, including PCI DSS, HIPAA, SOX, SOC/SSAE16, ISO 27001, FedRAMP, FISMA, PCI PA-DSS, GLBA, and SIG. — Network Security: The Network Security feature detects vulnerabilities and sends real-time alerts, enabling immediate response and mitigation of potential threats. — Hacker Threat Analysis: The Hacker Threat Analysis feature lets you understand what hackers know about your system. This data can be crucial in identifying weaknesses and developing defense strategies. — Breach Monitoring: With the Breach Monitoring feature, you can stay informed about the latest threats and promptly implement effective response strategies by tracking breaches and remediation responses. Below are some of the key benefits of iTrust: — Benchmarking: iTrust’s benchmarking tool simplifies the process of tracking and measuring your security investments. This allows for informed decision-making about resource distribution and strategic planning. — Cyber Insurance: iTrust’s customized Cyber Insurance solution speeds up the underwriting process and helps secure business deals with low-risk, high-return clients. This enhances the insurance workflow and increases profitability. — Mergers and Acquisitions: iTrust offers services to speed up the cybersecurity due diligence process during potential mergers and acquisitions. We identify and mitigate potential cybersecurity threats before finalizing any transaction. — 360° Assessments: iTrust’s 360° Assessments provide a thorough analysis of cyber risks from every angle – including internal, external, and independent ratings. This comprehensive view ensures no threat goes unnoticed. Learn more about iTrust
The Dual Power of GhostWatch: Security and Compliance Unveiled

With the rise in cyber threats and the growing sophistication of hackers and cybercriminals, businesses globally are realizing the critical need to protect their systems and data. Not only is this vital for security, but it’s also a crucial aspect of regulatory compliance. Enter GhostWatch, a product of TrustNet. Globally recognized as a premier security and compliance management provider, GhostWatch offers a unique approach to Managed Security and Compliance services. It’s not just a tool but a comprehensive solution designed to safeguard enterprises against persistent threats posed by hackers, cybercriminals, and other harmful entities. In a world where digital risks are ever-evolving, GhostWatch stands as a beacon of security, exemplifying the future of protection in the digital age. The Dual Power of GhostWatch Security and compliance are vital in ensuring your digital assets’ integrity, safety, and legality. GhostWatch seamlessly integrates these twin pillars into a single service, offering businesses unparalleled protection. As a leading managed security provider, GhostWatch employs advanced tools and features to secure your systems from the relentless onslaught of hackers, cybercriminals, and other malicious actors. Backed by a team of expert cybersecurity analysts, GhostWatch offers real-time threat detection and response, ensuring your business remains safe and secure amidst the ever-evolving landscape of digital threats. The second aspect, Compliance, is equally significant. GhostWatch understands the complexities of regulatory compliance and the challenges it can pose for businesses. To address this, GhostWatch manages the entire compliance journey, providing real-time visibility at a reasonable cost. With experience from hundreds of compliance assessments under its belt, GhostWatch has successfully guided, managed, and maintained compliance for a multitude of clients. This wealth of experience allows GhostWatch to navigate the intricacies of compliance easily. GhostWatch’s dual power lies in its ability to provide robust security and streamlined compliance, integrated seamlessly into a single, comprehensive service. This unique approach offers businesses peace of mind, knowing their digital assets are both secure and compliant. Learn more about GhostWatch Here Revolutionizing Traditional Cybersecurity Approaches While they have served their purpose in the past, traditional cybersecurity strategies now face significant limitations in the rapidly evolving digital landscape. These conventional methods are becoming increasingly expensive, difficult to scale, and demand extensive resources. Furthermore, they often focus on protecting everything except the actual data, leaving organizations vulnerable to data breaches. These traditional strategies usually involve vulnerability assessments, penetration testing, and network monitoring. However, as cyber threats become more sophisticated, these methods need help to keep up. For instance, traditional security tools often fail against business logic attacks because they cannot recognize new or unknown signatures. They are also limited in defending against modern tactics such as email phishing, imitation websites, and threats from unsecured gaming or video-streaming platforms. To address these challenges, GhostWatch’s Managed Security and Compliance services are redefining the approach to cybersecurity. Unlike traditional methods, GhostWatch adopts a proactive approach to security, identifying potential threats before they can be exploited. This shift from reactive to proactive significantly enhances the security posture of businesses. Furthermore, GhostWatch seamlessly integrates security and compliance into a single solution. This holistic approach aligns security measures with compliance requirements, streamlining processes and reducing the risk of compliance breaches. By transforming traditional cybersecurity methods, GhostWatch’s Managed Security and Compliance services offer a comprehensive, proactive, and integrated solution well-equipped to meet the challenges of today’s digital world. Features and Benefits of GhostWatch’s Managed Security and Compliance Services GhostWatch offers a suite of advanced features designed to enhance your cybersecurity stance. Each feature provides unique benefits that cater to the needs of IT managers, CISOs, and business leaders. — Security Monitoring: GhostWatch provides 24/7 security monitoring, ensuring constant vigilance over your digital assets. This round-the-clock surveillance and essential security tools offer complete security visibility. This means no threat goes unnoticed by IT managers, allowing them to respond in real-time and keep systems secure. — Compliance Support: GhostWatch simplifies regulatory adherence, supporting various standards like SOC, PCI DSS, ISO 27001, HIPAA, and HITRUST. It enables businesses to manage, analyze, and report on all operational aspects from a single platform. This fosters compliance efficiency, making it easier for CISOs to ensure their organizations meet compliance standards. — Advanced Threat Management: Through comprehensive threat management, GhostWatch minimizes your organization’s risk. It integrates threat detection, incident response, and threat management with built-in security tools and real-time threat intelligence. This feature empowers business leaders by reducing the risk of cyber threats and ensuring business continuity. — Vulnerability Management: GhostWatch’s proprietary threat intelligence identifies unknown exploits, updating in real-time to keep pace with evolving threats. In case of security breaches, an immediate incident response plan is prioritized. For IT managers, this means identifying vulnerabilities quickly and effectively ensuring their systems remain secure. — Network Security: GhostWatch offers a comprehensive network security solution integrating omnichannel management, threat protection, and unified communication into one powerful platform. This gives IT managers a holistic view and control over their network, enhancing overall security. — Threat Intelligence: GhostWatch connects to a global community of threat researchers and security professionals, providing an extensive, up-to-date view of the threat landscape. Sourced from over 100,000 contributors across 140 countries and 19 million daily threat indicators, this feature ensures CISOs are always aware of the latest threats. — Cloud and Multi-Cloud Support: GhostWatch extends its robust security capabilities to public cloud environments, detecting and combating cyber attacks. It supports Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform installations, extending beyond just on-premises servers. This gives business leaders confidence that their data is secure, regardless of where it’s stored. — Log Management: GhostWatch’s advanced log management platform automatically correlates log data from multiple sources using integrated Security Information and Event Management (SIEM) capabilities. It regularly correlates events with real-time threat intelligence and provides frequent automatic updates. This feature enables IT managers to stay ahead of potential threats, ensuring the ongoing security of their systems. Why Choose GhostWatch GhostWatch is a formidable shield against modern cyber threats. It offers advanced technology and deep technical expertise to safeguard critical assets and
Coming Soon: Exciting New Solutions from TrustNet in 2024

As we usher in a new year, TrustNet continues its unwavering commitment to innovation in cybersecurity. With an established track record of providing robust and reliable solutions, we are launching a series of transformative offerings in 2024 that will redefine the landscape of cyber protection. The rapidly evolving digital landscape has always driven our dedication to continuous advancement. In our increasingly interconnected world, the sophistication of cyber threats is escalating at an unprecedented rate. This necessitates staying abreast of current cybersecurity needs and forecasting future challenges. TrustNet recognizes the importance of staying one step ahead and is committed to developing solutions for tomorrow’s cyber threats. GhostWatch Platform As a leading managed security and compliance provider, GhostWatch is trusted by businesses globally to protect their systems from the ever-present threat of hackers, cybercriminals, and other malicious entities. Equipped with an advanced suite of tools and features, its strength lies in its sophisticated technology and team of expert cybersecurity analysts who work tirelessly to ensure your systems are secure and resilient against cyber threats. Unique Features and Capabilities GhostWatch is designed to secure and monitor your entire technology stack – from software and hardware to services. Here’s an overview of its unique features and capabilities: — Security Monitoring GhostWatch provides a unified security intelligence solution that includes round-the-clock monitoring. It offers vulnerability and compliance reporting with built-in essential security tools for complete security visibility, ensuring no threat goes unnoticed. — Compliance Designed to simplify regulatory adherence, GhostWatch supports compliance with various standards, including SOC, PCI DSS, ISO 27001, HIPAA, and HITRUST. It enables businesses of all sizes to manage, analyze, and report on all aspects of their operations from a single platform. — Advanced Threat Management GhostWatch provides a comprehensive approach to managing security needs and threats, helping you reduce your organization’s risk. It combines threat detection, incident response, and threat management with built-in security tools and integrated threat intelligence. — Vulnerability Management GhostWatch’s proprietary threat intelligence identifies unknown exploits in your assets. The platform updates in real time, keeping pace with the latest threats. It offers rapid installation in the cloud and on-premises, with scanning and reporting available on-demand or on a schedule. In a security breach, it prioritizes an incident response plan. — Network Security As a complete network security monitoring and intrusion detection solution, GhostWatch combines omnichannel management, threat protection, and unified communication into one powerful platform. — Threat Intelligence GhostWatch is connected to a global community of threat researchers and security professionals. With contributions from over 100,000 contributors across 140 countries and 19 million daily threat indicators, GhostWatch offers an extensive, up-to-date view of the threat landscape. — Cloud and Multi-Cloud GhostWatch offers a comprehensive and scalable security capability to detect and combat cyber attacks on your public cloud environment. Not limited to on-premises servers, GhostWatch supports public cloud installations, including Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform. — Log Management GhostWatch’s advanced security log analysis and management platform offers various capabilities, including regular correlation of events with up-to-date threat intelligence, automatic correlation of log data from multiple sources using integrated Security Information and Event Management (SIEM) capabilities, and frequent automatic updates of threat intelligence. Why Choose GhostWatch? GhostWatch is designed to tackle the ever-evolving cybersecurity landscape, offering exceptional security through advanced technology and deep technical expertise. It ensures the safeguarding your critical assets and aids in regulatory compliance, making it a potent shield against contemporary cyber threats. The professionally managed solution deploys quickly, transitioning businesses from vulnerable to secure in days rather than months. This fast deployment and all-in-one solution that includes hardware, software, and services dramatically enhances a business’s security posture. In addition to robust security and rapid implementation, GhostWatch offers an affordable solution with transparent pricing and a fixed monthly fee, making high-level cybersecurity accessible to businesses of all sizes. The 12-month term and scalable services ensure your business grows, as does your security. With 24/7 monitoring from world-class security operations centers and multi-continent operations, GhostWatch provides an always-on service. Its rapid response capability identifies threats and neutralizes them swiftly, minimizing potential damage and downtime. GhostWatch’s comprehensive and proactive approach to cybersecurity positions businesses to effectively combat cyber threats, safeguard their assets, and maintain regulatory compliance. Learn more about GhostWatch Here iTrust Service Trust is a leading cybersecurity risk rating and risk intelligence provider dedicated to helping businesses establish trusted relationships with their vendors, partners, and suppliers. By collecting and analyzing third-party risk metrics through advanced machine learning techniques, iTrust offers a comprehensive 360-degree visibility into vendor security and compliance. Hailed as one of the world’s most intelligent cyber risk rating and threat intelligence platforms, iTrust is committed to providing robust, actionable risk insights. Unique Features and Value Propositions iTrust offers unique features that provide comprehensive cyber risk and compliance assessments. — Vendor Risk Management The Vendor Risk Management feature provides cybersecurity risk ratings across a portfolio of vendors. This allows for an understanding and managing potential risks associated with each vendor relationship. — Benchmarking With the Benchmarking feature, tracking and measuring security investments becomes efficient, facilitating informed resource allocation and strategic planning decisions. — Cyber Insurance The Cyber Insurance service is designed to accelerate underwriting and close more sales with low-risk, high-yield clients, leading to a more efficient insurance process and increased profitability. — Mergers and Acquisitions iTrust offers services to accelerate cybersecurity due diligence on merger and acquisition targets, identifying and addressing potential cybersecurity risks before finalizing any transaction. — 360° Assessments The 360° Assessments provide a panoramic view of cyber risks from all angles – internal, external, and independent ratings. This comprehensive perspective ensures no threat goes unnoticed. — Compliance Year-round Compliance monitoring and tracking is available, helping ensure that companies remain in line with all relevant regulations and standards, including PCI DSS, HIPAA, SOX, SOC/SSAE16, ISO 27001, FedRAMP, FISMA, PCI PA-DSS, GLBA, and SIG. — Network Security The Network Security feature identifies vulnerabilities and sends alerts in real-time, allowing for immediate response and mitigation of potential threats.
TrustNet’s 2023 Journey: Celebrating Our Growth and Successes in Cybersecurity

In 2023, TrustNet marked an impressive year of growth and success in the dynamic field of cybersecurity. This year’s milestones are a testament to our unwavering commitment to excellence as we navigated complex security landscapes, innovated, and expanded our reach. We take immense pride in celebrating our achievements that have fortified our position as a leader in cybersecurity and compliance. Our steadfast dedication drove our journey to delivering top-tier cybersecurity services and solutions. TrustNet’s commitment to safeguarding our clients’ digital assets has been at the forefront of our operations. In 2023, we bolstered our offerings, incorporating cutting-edge technology and strategies, ensuring robust security for businesses across the globe. As we retrospect, we celebrate our growth and contribution to a safer, more secure digital world. Insights Shared at CyberDefenseCon 2023 In its 11th year, CyberDefenseCon once again convened the most influential leaders and innovators in information security. Held at the Ritz-Carlton Orlando, the conference provided a platform for CISOs and cybersecurity experts to discuss the evolving threat landscape as we approach the end of 2023. Topics ranged from the complexities of cloud-enabled supply chains to geopolitical tensions in Ukraine and Israel. The focus was finding innovative ways to mitigate risk and protect critical infrastructures. The conference also delved into best practices for DevSecOps and Zero-Trust implementation, navigating the shifting regulatory climate, and making prudent investments with limited security budgets. TrustNet, with its two decades of industry experience, contributed its unique perspective to these discussions. While acknowledging the complexity of the current cybersecurity environment, TrustNet emphasized the power of simple, proactive measures like maintaining full network visibility. This approach allows for rapid threat detection and response, thus preventing situations from escalating. TrustNet’s commitment to innovative, cost-effective solutions has earned it numerous accolades from the organizers of CyberDefenseCon. Given the severity of emerging threats, the company encourages businesses to adopt a risk-centric approach in the digital economy. With the proliferation of IoT devices and generative AI, the attack surface of businesses has expanded dramatically. The frequency and impact of data breaches have prompted stricter data and privacy legislation across various jurisdictions and industries. Cybersecurity is no longer just an IT problem but impacting diverse business functions. TrustNet remains committed to safeguarding digital assets and fostering a more secure digital world as we move forward to 2024. For read more about it, Click Here Analysis of Phishing Trends in Q1 and Q2 In the first half of 2023, TrustNet’s analysis revealed a significant shift in phishing tactics, leading to the detection of an alarming 562.4 million phishing emails in just Q1. The cybersecurity landscape has been increasingly dynamic, with threat actors continually adapting their strategies to exploit vulnerabilities and bypass security measures. This surge in phishing attacks underscores the evolving nature of cybersecurity threats that businesses must grapple with. The FutureCon San Diego CyberSecurity Conference, held on October 18, 2023, set an urgent tone for the evolving landscape of cybersecurity. The theme was clear: “Cybersecurity is no longer just an IT problem.” This underscored the necessity for proactive, holistic, and collective action, particularly as cyber threats become more elusive and sophisticated. Despite being armed with AI, machine learning, and automation technologies, IT teams grapple with expanding attack surfaces and increasingly complex cyber threats. The conference buzzed with discussions around Zero Trust, dynamic threat intelligence, bad actors, risk mitigation, and SecOps. These terms encapsulate the current challenges in the cybersecurity landscape, indicating the areas where concerted effort and innovation are required. TrustNet’s observations from the conference highlighted threat actors’ widespread use of advanced technologies and the consequent emerging challenges cybersecurity professionals face. TrustNet noted that winning against bad actors is achievable, and maintaining security over time can be normalized. The key lies in the willingness to adapt and innovate. Static IT security strategies no longer suffice in this dynamic threat environment. To outsmart adversaries, IT teams must comply with updated security standards and incorporate proactive measures designed and deployed by experts. For more on our cybersecurity and compliance services, Click Here Role as a Reliable Partner for PCI Compliance TrustNet, a PCI Qualified Security Assessor (QSA), has been instrumental in guiding businesses in navigating the complex landscape of Payment Card Industry Data Security Standard (PCI DSS) compliance. With the release of PCI DSS 4.0, TrustNet remains a vital resource for organizations, helping them understand and adapt to the new changes. This latest version of PCI DSS emphasizes continuous compliance and security as an ongoing process. TrustNet’s expertise is particularly beneficial here, as we provide comprehensive services that empower businesses to maintain their compliance goals and build a sustainable program, regardless of their current position in the compliance cycle. One of the significant updates in PCI DSS 4.0 is the increased focus on cloud technologies and the need for robust authentication protocols. TrustNet recognizes the importance of Identity and Access Management (IAM) in this context and aligns its services with NIST guidance on digital identities. Another highlight of PCI DSS 4.0 is its flexibility, allowing organizations to customize their authentication systems based on their risk environment. TrustNet, with our customized solutions, can guide businesses in implementing these changes effectively. Lastly, TrustNet’s commitment to helping organizations maintain secure systems extends beyond compliance. By minimizing the risk of fraud and fostering trust among businesses and customers, TrustNet plays a crucial role in the broader cybersecurity landscape. For more on our PCI DSS services, Click Here TrustNet’s Cybersecurity Triumphs in 2023 TrustNet’s contribution to the cybersecurity industry in 2023 has been marked by our exceptional service to clients and our dedication to enhancing security resilience across various business sectors. These achievements in 2023 testify to our robust strategies and effective solutions tailored to address complex security challenges. TrustNet’s thought leadership in the cybersecurity domain was also well-recognized in 2023. We shared valuable insights and learnings from the year, reinforcing our position as a trusted advisor in this field. Our expert services continue to be sought after by businesses looking to bolster their security posture and build resilient infrastructures.
A Year in Review: TrustNet’s Success Stories in Cybersecurity in 2023

Throughout 2023, TrustNet has stood at the forefront of cybersecurity. We continue to garner notable achievements and provide key takeaways from industry-leading events such as CyberDefenseCon 2023 and the RSA Conference 2023. We actively contributed to critical discussions on emerging security risks, championing the necessity of proactive measures in cybersecurity. In these events, we underscored the criticality of maintaining full network visibility for swift threat detection and response. Furthermore, TrustNet acknowledged the evolving landscape of cybersecurity, including the implications of artificial intelligence on societal trust. Our unwavering commitment to continuous learning and innovation propels us forward as we enter the new year. Keep reading as we delve deeper into TrustNet’s success stories through 2023. TrustNet’s Successes at CyberDefenseCon 2023 TrustNet left a significant mark at CyberDefenseCon 2023, a gathering of the world’s top information security leaders and innovators. The event was a platform to explore smarter ways of mitigating risk in the ever-evolving threat environment. TrustNet, with our two-decade-long industry experience, emphasized the importance of being proactive in cybersecurity and having complete network visibility to detect and respond to threats promptly. TrustNet’s mantra of designing solutions based on these principles has been recognized by the same group that organizes CyberDefenseCon annually. Our numerous accolades from Cyber Defense Magazine (CDM) are a testament to our innovative and cost-effective solutions that stay one step ahead of the subsequent breach. The discussions at the conference and TrustNet’s research highlighted the future of information security: Information Security (InfoSec) leaders are evolving beyond managing firewalls and antivirus software and are now linked to diverse business functions. Given the complexity and severity of emerging threats, businesses adopting a risk-centric approach in the digital economy will likely be more resilient and prosperous. The widespread use of IoT devices and AI technologies has expanded the attack surface for organizations. Data breaches have led many jurisdictions and industries to enact stricter data and privacy legislation. Industry experts believe that cybersecurity is no longer just an IT problem. TrustNet combines human expertise, advanced technologies, and streamlined processes to simplify and reinforce compliance and security postures. Our award-winning solutions have gained the confidence of hundreds of satisfied clients, from startups to mature enterprises worldwide. Read more about it, Here TrustNet’s Achievements at the RSA Conference 2023 TrustNet also made a significant impression at the RSA Conference, a premier global cybersecurity event held annually since 1991. This gathering showcases the latest products and services in IT security, providing an opportunity for organizations and thought leaders to explore emerging threats, trends, and innovations. The conference at the Moscone Center in San Francisco attracted thousands of attendees and hundreds of companies. TrustNet was there to gain fresh insights into security and compliance and bagged two prestigious Global InfoSec Awards, reinforcing our commitment to staying at the forefront of cybersecurity. Our team engaged with ETHOS (Emerging Threat Open Sharing), a collaborative platform designed as an alarm system for critical infrastructure increasingly targeted by threat actors. We also participated in discussions about Artificial Intelligence (AI) and its societal impact. While AI’s potential to assist with day-to-day tasks was acknowledged, concerns about its sensitivity to complex verbal instructions and resulting “trust issues” made some organizations hesitant to embrace it fully. The conference also highlighted the intersection of technology with other fields, featuring guests from journalism, education, marketing, policy-making, law, and even the arts. TrustNet’s participation in the RSA Conference 2023 was a resounding success. We returned with fresh insights to apply across our business, from product innovation to market strategy. We were particularly proud of our affiliated brand, GhostWatch, earning two coveted awards: Next Gen Managed Compliance and Next Gen Managed Security Service Provider by Cyber Defense Magazine (CDM). Read more about it, Here TrustNet’s Role in Helping Companies Understand and Avoid PCI DSS Fines TrustNet, a PCI Qualified Security Assessor (QSA), plays a vital role in helping companies understand and avoid fines associated with the Payment Card Industry Data Security Standard (PCI DSS) compliance. Our comprehensive range of services empowers businesses to achieve their compliance goals and build a sustainable program, regardless of where they are in the compliance cycle. PCI Gap Assessment One of our essential services is the PCI Gap Assessment. This includes thoroughly reviewing policies and procedures, conducting interviews, and reviewing network diagrams, configurations, and data flow documentation. Our team identifies where cardholder data is stored, creates data flow analysis and mapping of cardholder data, assesses network segmentation, reviews architectural design and documents, and confirms the scope for future PCI DSS onsite validation. This process provides businesses with a clear understanding of their current state and what steps they need to take to achieve and maintain PCI DSS compliance. PCI DSS Compliance Review SAQ Another vital service we provide is the PCI DSS Compliance Review SAQ. Companies that attest to their own Self-Assessment Questionnaire (SAQ) can utilize this service for compliance reviews and guidance. We review policies and procedures, conduct interviews, review network diagrams, configurations, and data flow documentation, validate where cardholder data is stored, create data flow analysis and map cardholder data, validate network segmentation, and assist in completing the SAQ. Furthermore, we offer PCI Penetration Testing to identify weaknesses, improve security, and reduce potential attack surfaces, fortifying a company’s defense against potential cyber threats. PCI DSS Report on Compliance (ROC) Finally, TrustNet provides PCI DSS Report on Compliance (ROC) guidance for businesses ready to undergo annual PCI audits. The deliverable includes an official Report on Compliance confirming that you meet the Payment Card Industry requirements, the Attestation of Compliance (AOC), and recommendations for improvements. In addition, we offer PCI Remediation Assistance, providing consulting and remediation services in all aspects of PCI DSS compliance. This may include developing specific implementation plans, consulting on various remediation needs, managing remediation tasks and timelines, and offering expert advice from our Qualified Security Assessors (QSA). For more on our PCI DSS services, Click Here Celebrating TrustNet’s Cybersecurity Achievements in 2023 Throughout 2023, TrustNet solidified its standing as a top-tier IT security and compliance service
Overcoming Cyber Threats: How Businesses Triumphed in 2023

The cybersecurity landscape of 2023 was a battleground, constantly shifting and evolving. Businesses rallied, adapted, and overcame challenges with remarkable resilience amid increasing threats. Their triumphs were not a result of luck but a testament to strategic planning, innovation, and learning from past trends. As we reflect on these events, it becomes evident that understanding the past is crucial for future cybersecurity strategies. This helps not only identify potential threats but also formulate effective defenses. By examining the triumphs of businesses in 2023, we can gain valuable insights to enhance our own cybersecurity strategies, ensuring a safer digital future for all. Top Cybersecurity Threats of 2023 In 2023, the cybersecurity landscape was dominated by a series of threats that severely impacted organizations and individuals. Ransomware attacks continued to be a prevalent menace. In 2023, ransomware continues to pose a significant threat to organizations globally, with 90,945 detections since January. The average ransom has nearly doubled from the previous year, reaching $1.54 million, according to reports from Sophos. Despite this, 97% of organizations have successfully recovered their encrypted data. Astra reports a 13% increase in ransomware attacks over the past five years, with incidents costing an average of $1.85 million each. Statista notes that companies typically face 22 days of downtime following an attack. Phishing attacks also remain common, leveraging social engineering techniques to trick users into revealing sensitive information. Statistics indicate that approximately 1.2% of all emails dispatched globally are malicious, equating to an alarming 3.4 billion phishing emails being sent daily. AI-driven attacks represent a new frontier in cybersecurity threats. As AI technology advances, it’s being used to develop more sophisticated, hard-to-detect threats. These include AI-powered malware that can learn and adapt to evade detection and AI-driven social engineering attacks that use machine learning algorithms to mimic human behavior and trick users into falling for scams. Deepfakes, another emerging threat, use AI to create fake but convincing images or videos. This technology can be used maliciously, such as creating fake news or impersonating individuals for fraud. In addition, social engineering remains a significant threat. These attacks exploit human psychology to trick users into making security mistakes, such as clicking on malicious links or revealing sensitive information. The rise of remote work due to the COVID-19 pandemic has given cybercriminals new opportunities to conduct these attacks. The severity and impact of these threats cannot be understated. They can cause significant financial damage, disrupt operations, and compromise sensitive data. As such, businesses and individuals must take steps to protect themselves, including investing in robust cybersecurity solutions and promoting security awareness among users. Real-life Examples of Triumphs Businesses globally faced an escalating threat from cybercriminals. However, as illustrated in the following case studies, many companies successfully navigated these challenges by implementing robust cybersecurity measures. Optima Tax Relief, a tax resolution firm, partnered with TrustNet to bolster its IT security infrastructure. Following a thorough audit and risk assessment, TrustNet deployed a proprietary cybersecurity platform providing round-the-clock protection and comprehensive visibility over compliance and security risks. This partnership significantly improved Optima Tax’s overall security posture, allowing them to fulfill their promise of a safe and secure site where customers could trust their sensitive data. Calendly, a renowned CRM and meeting scheduling company, adopted NIST Risk Assessment, HIPAA, SOC 2, and ISO 27001 standards to enhance their cybersecurity measures and safeguard their customers’ sensitive data. This implementation increased customer confidence and improved Calendly’s compliance with industry regulations, attracting new customers and business partners. These real-life examples underscore the importance of proactive cybersecurity strategies in overcoming the growing threat of cybercrime. For more on our cybersecurity and compliance services, Click Here Key Lessons Learned The successes of businesses in 2023 have yielded valuable lessons and insights that can guide the enhancement of cybersecurity strategies. The following are some key takeaways: Proactive Measures: Optima Tax Relief’s partnership with TrustNet demonstrated the effectiveness of proactive measures. They improved their IT security infrastructure by conducting an initial security audit and implementing a zero-trust posture. This highlights the importance of actively seeking out potential vulnerabilities and addressing them before they can be exploited. Comprehensive Employee Training: Cybersecurity isn’t just about technology; it’s also about people. Employees need to be trained to recognize and respond to cybersecurity threats. This includes identifying phishing emails and knowing what to do if they suspect a security breach. Staying Informed and Proactive: Calendly’s implementation of various industry-standard cybersecurity measures like NIST Risk Assessment, HIPAA, SOC 2, and ISO 27001 underscores the importance of keeping up with the latest developments in cybersecurity and proactively adopting these measures to protect customer data. Partnerships and Collaboration: Optima Tax Relief and Calendly benefited from partnering with experts like TrustNet to bolster their cybersecurity. These partnerships provide valuable insights and resources that can help businesses better protect themselves from cyber threats. These lessons underscore the multifaceted nature of cybersecurity. It’s not just about having the right technology but also the right strategies, training, partnerships, and mindset. Charting the Path to Future Business Success The year 2023 has been a testament to various businesses’ resilience, innovation, and strategic prowess. These triumphs offer rich insights and lessons that can help organizations strengthen their cybersecurity strategies and effectively manage future threats. As we look forward to 2024, these lessons from 2023 provide a valuable roadmap. By applying these insights and partnering with cybersecurity experts like TrustNet, businesses can confidently bolster their cybersecurity strategies and navigate the complex digital landscape. Ensure a secure digital environment for your business with TrustNet. Talk to an Expert today for more information.



