Managed Security Services
Dependable Protection 24/7
Security management has rapidly evolved into a critical business need as Cyberthreats have become more sophisticated and hackers more determined.
TrustNet’s Managed Security Platform detects and investigates intrusions, identifies and prioritizes vulnerabilities, and monitors cloud and on-premise environments.
TrustNet’s Managed Security Package Includes
TrustNet’s Partner Platforms



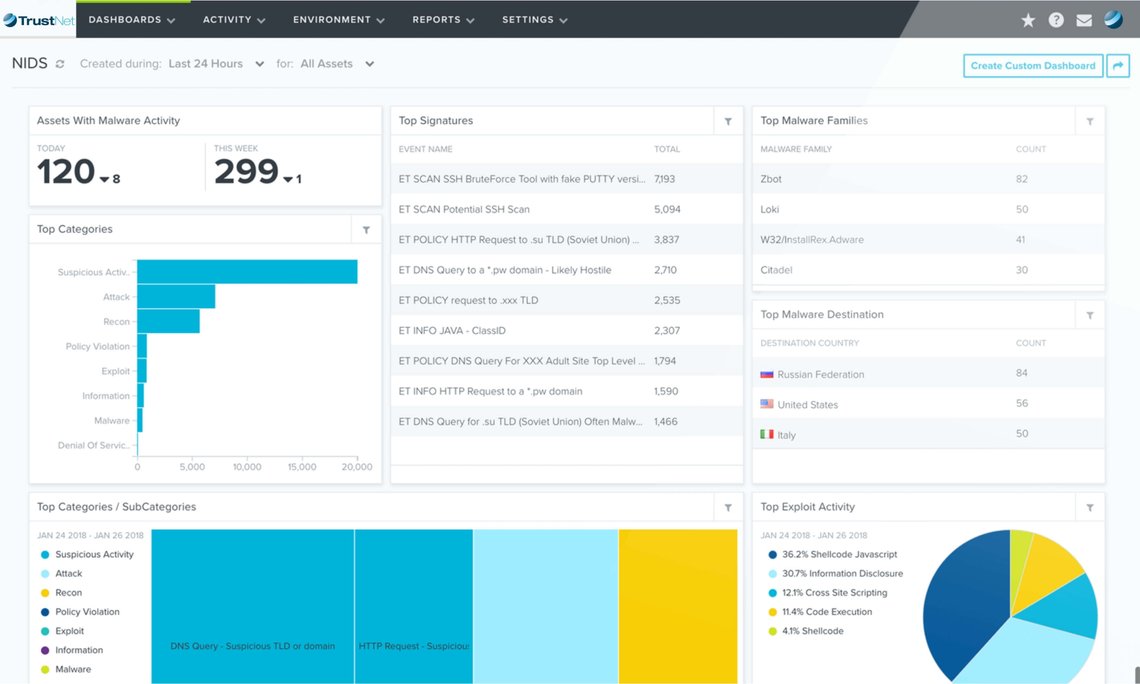
Security Monitoring
Security Monitoring with built-in essential security tools for complete security visibility that simplifies and accelerates threat detection, incident response, and compliance management.
Our all-in-one platform includes all the essential security capabilities your business needs, managed from a single pane of glass, working together to provide the most complete view of your security posture.

SECURITY EVENT MANAGEMENT
Monitoring all security events and staying on top of what’s important.

EVENT CORRELATION
Linking every asset, vulnerability, intrusion, malicious action, and remediation info for every alarm.

SECURITY INTELLIGENCE
Threat Management
Our platform coordinates threat detection, incident response and threat management with built-in security capabilities, integrated threat intelligence, and seamless workflow for rapid remediation.
Consolidating threat detection capabilities like network IDS and host IDS with granular asset information, continuous vulnerability assessment, and behavioral monitoring provides a comprehensive view for timely and effective response.

ADVANCED ENDPOINT THREAT DETECTION

INTRUSION DETECTION

THREAT ANALYSIS

RANSOMWARE DETECTION

ADVANCED ENDPOINT THREAT PREVENTION
ADVANCED REMEDIATION MANAGEMENT


Threat Intelligence
Connected to a global community of threat researchers and security professionals.
contributors
countries
daily threat indicators
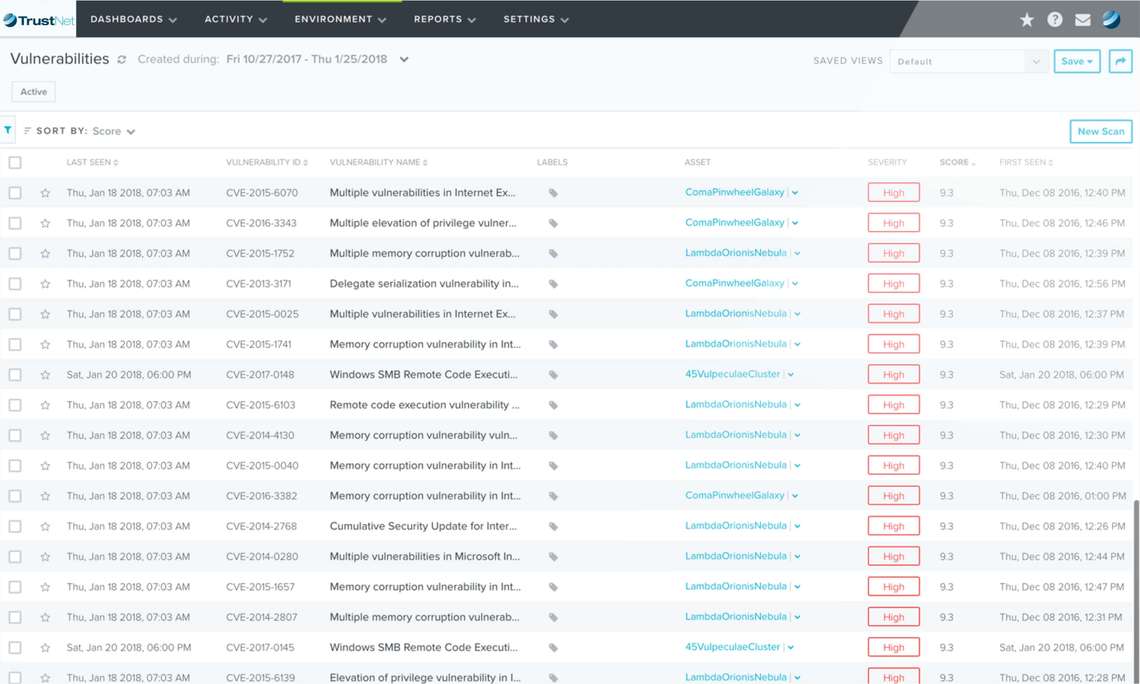
Vulnerability Management
Quickly absorb our proprietary threat intelligence into a fully managed process to help detect unknown exploits in your network, devices, servers, web applications, databases, or other assets — both on-premise and in the cloud.

VULNERABILITY ASSESSMENT AND REMEDIATION

VULNERABILITY SCANNING
Stay ahead of attackers with these advanced features:
Network Security
An all-in-one platform and managed security service for complete network security monitoring and intrusion detection.

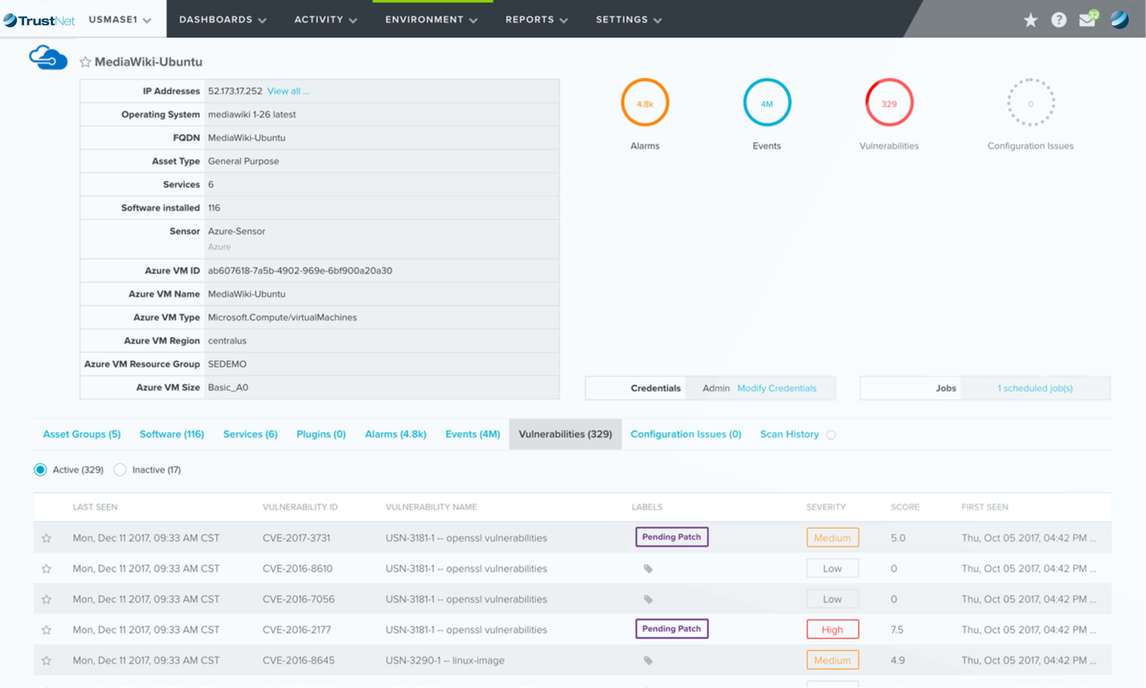
ASSET DISCOVERY AND INVENTORY
Built-in asset discovery tools:

BEHAVIORAL MONITORING
Behavioral monitoring capabilities provide the following core functionality:

CONTINUOUS SECURITY MONITORING

ASSET MANAGEMENT AND INVENTORY
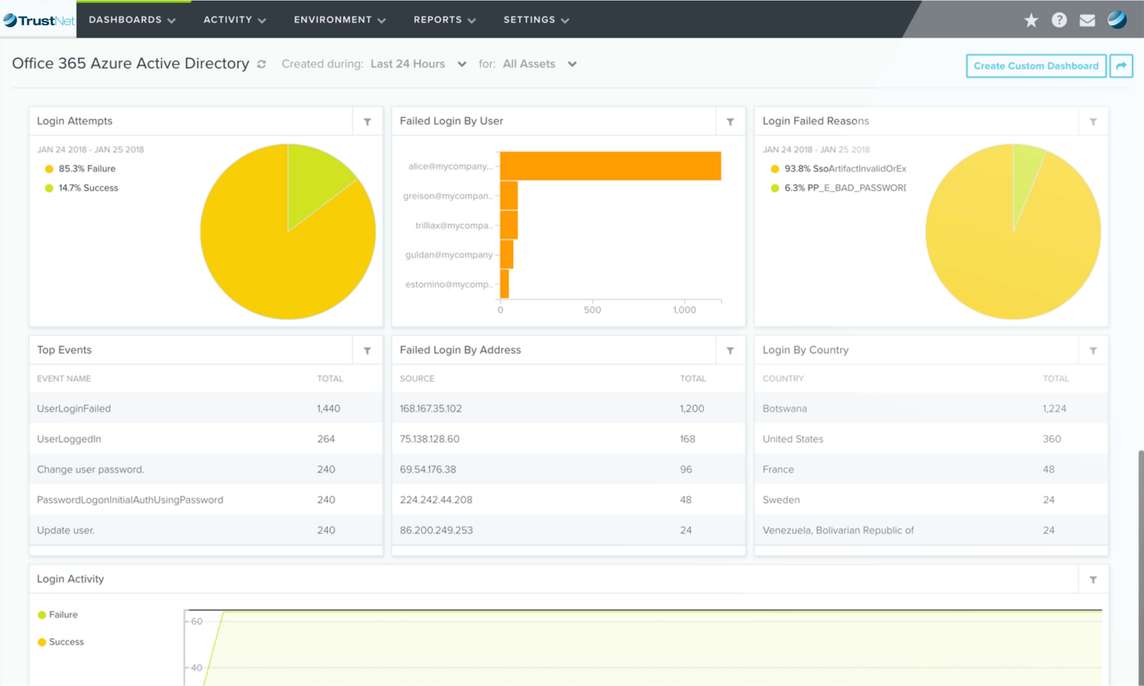
Cloud and Multi-Cloud
TrustNet supports public cloud deployments including Amazon Web Services (AWS) Microsoft Azure, and Google Cloud Platform. For organizations with assets spread across multiple cloud and on-premises environments, we deploy sensors to monitor it all.

Amazon Web Services

Microsoft Azure

Google Cloud Platform
Log Management
We provide all of the features and functionality you expect from security log analysis and management including:

Event Correlation with Regularly Updated Threat Intelligence

Log Analysis Simplified with Intuitive UI and Open Plugin Architecture

Multifunctional Security Log Management and Reporting
Compliance Management
Our platform is designed to facilitate compliance with many common regulatory compliance requirements including SOC, PCI DSS, ISO 27001, HIPAA and HITRUST.


CONTINUOUS COMPLIANCE

ASSET DISCOVERY AND MONITORING

FLEXIBLE REPORTING AND DASHBOARD
Auditor-ready report templates for PCI-DSS, SOC, ISO 27001, HIPAA and more
Our platform capabilities and services include asset discovery, vulnerability assessment, intrusion detection, service availability monitoring, log management, and file integrity monitoring (FIM), that enable us to:
Why Clients Choose TrustNet

24/7/365
Our platform delivers 24/7/365 Managed Security from our world-class security operations centers. Our always-on coverage defends your network preventing network outages, downtime, and remediation costs.

QUALITY
TrustNet’s Security Operations Team has the skills and experience to safeguard and manage your critical resources. Our deep technical expertise ensures quality, security and compliance services are delivered to your business.

RELIABLE
TrustNet’s Managed Security platform includes built-in technical redundancies in a security-hardened platform. We operate from world-class, highly secure Security Operations Centers with multiple redundant network connections and redundant cloud-based backup SOC’s.

AFFORDABLE
TrustNet’s industry-leading Managed Security services and platform are deployed in significantly less time and at less cost than a do-it-yourself approach. TrustNet Managed Security Services are delivered from on-premise and cloud services and includes all hardware, software, and services for an affordable fixed monthly fee.