Vendor Risk Management
We saw immediate results from iTrust’s real-time vendor risk monitoring.”
– iTrust user
Businesses lack visibility into third-party cybersecurity and compliance risks
#1
56%
of all businesses experienced a third-party data breach
83%
of organizations admit they don’t manage third-party risks effectively
+4000
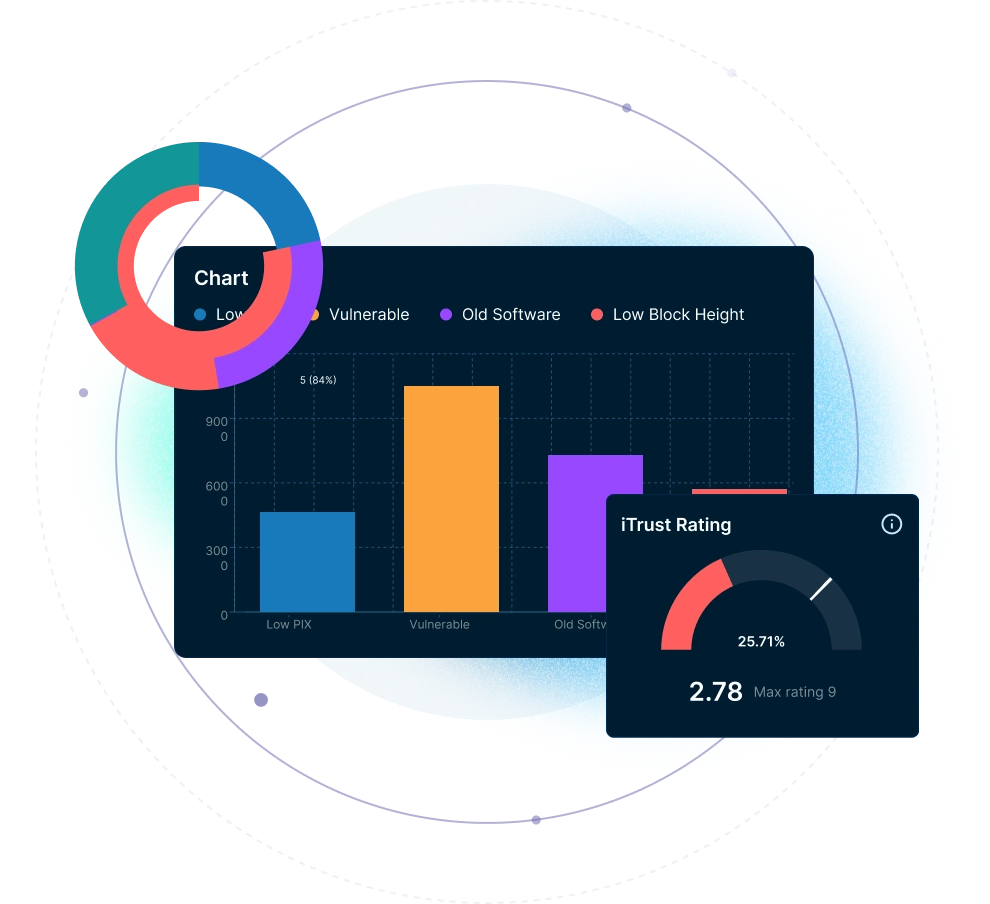
Cloud Platform for Automated and Continuous Cybersecurity Risk Ratings
“Customers point to iTrust’s real-time monitoring as one of its top strengths”
Forrester New Wave Report

Real-Time Monitor
Manage Remediation
Validate Compliance
iTrust Solutions
“A team of experienced security analysts and consultants that can keep development on the right trajectory”
Independent Technical Testing
Vulnerability Scanning
Dark Web Analysis
Aggregated Web Data
Real-Time Monitoring
Continuously and efficiently assess its security posture
Proprietary Data Points
Insider Risk Assessment
Assess cybersecurity risks
Compliance Status
Track compliance status and expiration dates
Compliance Surveys
Collect detailed compliance data
Crowdsource Reputation Ratings
Monitor crowdsourced reputation ratings from industry peers and partners
Network Security
Analyse vulnerabilities on exposed network services
DNS Resilience
Access DNS Configs and Anti-Spoofing defenses
Web Application Security
Analyse web-app vulnerabilities through scanning, intercepting proxies and web crawlers
Hacker Threat Analysis
Monitor underground hacker sites and the dark web
Breach Metrics
Identify known breaches and remediation responses
Patching Cadence
Measure patch management and response rates over time
Business Value
Scope includes:
360° visibility of vendors’ cybersecurity risks
12+ metric scores of various parameters
Comprehensive risk rating score
Vendor’s compliance up-to-date status
Monitoring and alerting of potential threats