

Compliance Without Complications: GhostWatch’s Managed Compliance Solutions
Blog Compliance Without Complications: GhostWatch’s Managed Compliance Solutions Compliance Without Complications: GhostWatch’s Managed Compliance Solutions The broad spectrum of compliance regulations is becoming more complicated in the fast-paced business sector....
The Dual Power of GhostWatch: Security and Compliance Unveiled
Blog The Dual Power of GhostWatch: Security and Compliance Unveiled The Dual Power of GhostWatch: Security and Compliance Unveiled Lately, there’s been a noticeable uptick in cyber threats, and the cunning of hackers and cybercriminals is growing by the day....
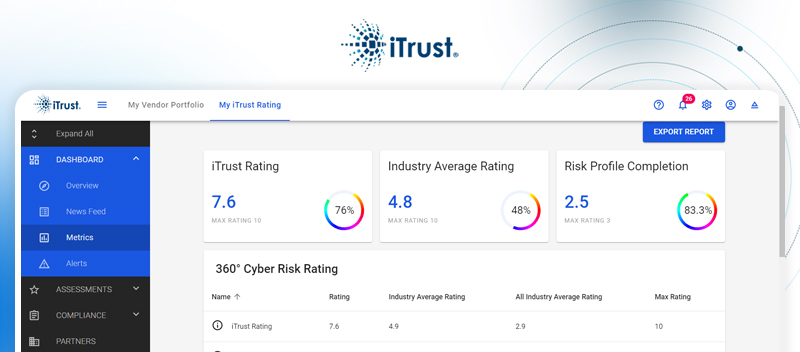
Launching a Safer Future: Meet GhostWatch and iTrust – New Solutions from TrustNet
Blog Launching a Safer Future: Meet GhostWatch and iTrust – New Solutions from TrustNet Launching a Safer Future: Meet GhostWatch and iTrust – New Solutions from TrustNet At TrustNet, we lead the way in compliance and cybersecurity and are renowned for our potent and...
PCI DSS Audit Demystified: Securing Your Business Payment Ecosystem
Blog PCI DSS Audit Demystified: Securing Your Business Payment Ecosystem PCI DSS Audit Demystified: Securing Your Business Payment Ecosystem The Payment Card Industry Data Security Standard (PCI DSS) is a benchmark for businesses to safeguard their payment ecosystems...
From Risk to Resilience: The Critical Benefits of Regular Penetration Testing
Blog From Risk to Resilience: The Critical Benefits of Regular Penetration Testing From Risk to Resilience: The Critical Benefits of Regular Penetration Testing The threat of cyber-attacks looms more prominent than ever, posing significant risks to organizations...
SOC 1 and SOC 2 Audit Explained: The Essential Guide for Startups Steering Towards Compliance
Blog SOC 1 and SOC 2 Audit Explained: The Essential Guide for Startups Steering Towards Compliance SOC 1 and SOC 2 Audit Explained: The Essential Guide for Startups Steering Towards Compliance Startups in the SaaS, finance, and service provider domains find...
CSIRT Cyber Security: How to Build an Incident Response Team
Blog CSIRT Cyber Security: How to Build an Incident Response Team CSIRT Cyber Security: How to Build an Incident Response Team Network systems and data security are crucial for businesses of any size. While deploying firewalls and other protective measures is a...
Banking on Security: Vulnerability Assessment and Penetration Testing for Financial Institutions
Blog Banking on Security: Vulnerability Assessment and Penetration Testing for Financial Institutions Banking on Security: Vulnerability Assessment and Penetration Testing for Financial Institutions Financial institutions are at the forefront of sophisticated attacks...
Keeping Up with Evolving Threats: A Guide for Modern Retailers
Blog Keeping Up with Evolving Threats: A Guide for Modern Retailers Keeping Up with Evolving Threats: A Guide for Modern Retailers Amidst the digital transformation in the market today, mid to large-sized retail chains face increasing cyber threats targeting both...
Unlocking Compliance: A Startup’s Guide to Deciphering a Sample SOC 2 Report
Blog Unlocking Compliance: A Startup’s Guide to Deciphering a Sample SOC 2 Report Unlocking Compliance: A Startup’s Guide to Deciphering a Sample SOC 2 Report A SOC 2 (Systems and Organization Controls 2) report is the outcome of a SOC 2 audit. It provides a detailed...
