NIST Cybersecurity Framework: A Comprehensive Guide to CSF Tiers and Implementation

Modern businesses constantly face an avalanche of cyber-attacks from increasingly sophisticated elements. At the same time, they also have to adhere to stringent compliance standards while safeguarding sensitive information. Such a situation can be handled systematically but requires a structured approach.
This whitepaper, NIST Cybersecurity Framework: A Comprehensive Guide to CSF Tiers and Implementation, offers exactly that. It’s to help businesses and practitioners understand, implement, and benefit from the NIST Cybersecurity Framework (CSF).
Overview of the NIST Cybersecurity Framework (CSF)
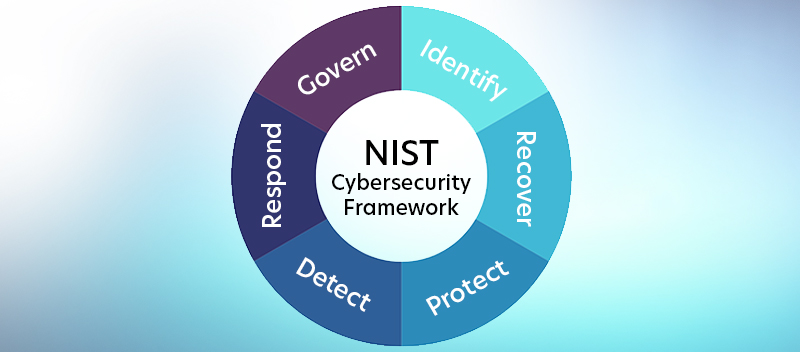
The NIST CSF is a flexible, adaptable blueprint for cybersecurity. It breaks down risk management into clear functions like Identify, Protect, Detect, Respond, Recover, and Govern. The framework’s tiered architecture assists firms in matching their security to their business aims, risk, and legal needs.
What This Guide Covers
This whitepaper dives deep into two critical areas of the NIST CSF:
— CSF Tiers
These tiers categorize an organization’s approach to cybersecurity from the most basic to the most advanced. Understanding where your organization stands — and where it wants to be, is a crucial first step.
— Implementation Strategies
Practical tips and actionable guidance are provided to help you map the framework to your organization’s unique needs, ensuring security measures are neither overbuilt nor underpowered.
Who Should Read This?
This whitepaper speaks directly to professionals tasked with shaping or executing cybersecurity strategies:
-
- Cybersecurity practitioners who handle day-to-day implementation and monitoring.
- IT managers striving to integrate systems, processes, and policies under the framework.
- C-suite executives who are in charge of managing corporate risks and making decisions regarding strategy.
Regardless of your position, this resource gives you the information and background you need to make sound decisions about enhancing your organization’s cybersecurity posture, aligning security initiatives with business objectives, and effectively managing risks.
Addressing Common Pain Points
Understanding and implementing the CSF isn’t always straightforward. Organizations often experience hurdles like:
-
- Interpreting the framework effectively. The language of standards can be dense. This guide simplifies it, focusing on what’s relevant and actionable.
- Deciding which controls to prioritize. Limited budgets and resources make it hard to address every risk at once. This whitepaper offers strategies for allocating resources intelligently.
- Meeting compliance requirements amid constant change. The guide provides insights on staying adaptable and proactive in the face of evolving regulations.
The regulatory landscape keeps shifting, and companies need a framework that evolves with them. The NIST CSF is that framework. This whitepaper will help organizations improve their security posture while aligning with regulatory and business goals. It breaks barriers, simplifies complexity, and gives you a precise roadmap.

What Is the NIST Cybersecurity Framework?
The National Institute of Standards and Technology (NIST) developed the Cybersecurity Framework (CSF) as a standard that businesses can use as a tool to assess and manage cyber risk. By providing a common language and prioritization for security efforts, it offers a structured approach to enhancing cybersecurity.
Initially released in 2014, the NIST CSF has become an industry-standard framework widely adopted across sectors. Its value is in its flexibility. By being scalable, the CSF applies to small businesses and multinational corporations, regardless of their cyber maturity.
It’s not prescriptive but adaptive, so it fits well for organizations with different operational needs and risk profiles. Helping businesses match their security efforts with business goals and legal and regulatory obligations is its main focus. To put it briefly, the CSF serves as a link between more general organizational management procedures and technological security measures.
Development History and Updates
From CSF 1.0 to CSF 2.0
The original NIST CSF (version 1.0) was developed in response to Executive Order 13636, issued in 2013, which sought to improve critical infrastructure cybersecurity. Released in 2014, CSF 1.0 was crafted through collaboration with industry leaders, academia, and government stakeholders. Its debut marked a milestone in cybersecurity by offering clear guidance that was both accessible and actionable.
However, the rapidly changing threat landscape necessitated updates. Enter CSF 2.0.
The updated version, released in early 2024, incorporates advancements to address evolving cybersecurity needs. While maintaining the fundamental ideas of the framework, it stresses a more inclusive approach, expanding the focus to topics like supply chain risk management and governance. The introduction of a new functionality named Govern, intended to improve organizational monitoring and decision-making capacities, is one of the major improvements.
Why the Updates Matter
CSF 2.0 builds upon the solid foundation of its predecessor while incorporating feedback from years of real-world application. These updates ensure that the framework remains relevant, effective, and forward-looking amid an era marked by increasing digital sophistication and cyber threats.
Core Components of the NIST Cybersecurity Framework
The framework is centered on its key components, which form the cornerstones of a strong cybersecurity program. These elements consist of the Framework Profile, Implementation Tiers, and Core. Specifically, the Core is the most actionable component of the system and specifies its structure.
— The Addition of the ‘Govern’ Function
One notable enhancement in CSF 2.0 is the introduction of the Govern function. This provision underscores the increasing understanding that strong organizational governance and accountability are necessary for effective cybersecurity. Establishing governance frameworks, allocating risk ownership, and coordinating cybersecurity with internal and external regulatory mandates are the main objectives of the Govern function.
With Govern joining the existing functions of Identify, Protect, Detect, Respond, and Recover, organizations can now approach cybersecurity with a more comprehensive lens that integrates strategic leadership.
— Explanation of the CSF Core
The CSF Core is the heart of the NIST framework. It is organized into six primary functions that collectively represent the key elements of a holistic cybersecurity strategy. Beneath these functions, Categories, and Subcategories break down tasks into more specific and manageable activities, allowing organizations to tailor the framework to their specific needs.
— The CSF Core Functions
Identify
This function establishes the foundation for successful cybersecurity by assisting businesses in understanding their assets, systems, data, and threats. Key areas include asset management, risk assessment, business environment, and supply chain risk management.
Protect
Creating protections to guarantee the ongoing resilience of vital services is the main goal of the Protect function. It includes proactive steps, such as data security, awareness training, and access control.
Detect
For cybersecurity events to be promptly identified, detection skills are crucial. Continuous monitoring and detection procedures adapted to the danger environment of an organization are part of this duty.
Respond
Once an incident occurs, an effective response is crucial. The Respond function guides organizations in developing plans to address and mitigate the impact of incidents.
Recover
This function focuses on post-incident activities to restore normal operations and reduce the likelihood of future incidents. It includes recovery planning and improvements based on lessons learned.
Govern (New)
Govern emphasizes leadership’s role in cybersecurity. Categories here address the assignment of roles, establishment of cybersecurity policies, and alignment of risk management processes with business objectives. This new function is critical for ensuring operational accountability and compliance.
— Categories and Subcategories
Categories are activities that are grouped under a specific function. For instance, under the Protect function, categories include “Data Security” and “Information Protection Processes.” Subcategories then break these into specific tasks, such as implementing encryption or access controls. Together, these levels of granularity make the framework adaptable and actionable for different organizations.
— Importance of Informative References and Implementation Examples
The NIST CSF doesn’t reinvent the wheel. Rather, it uses Informative References to link its recommendations to current frameworks, standards, and best practices. The CSF guarantees that enterprises have access to tried-and-true implementation strategies by connecting its categories and subcategories to recognized standards such as ISO/IEC 27001, COBIT, or NIST SP 800-53.
— Implementation Examples
For practical application, the framework often provides examples that demonstrate how specific controls can be implemented. For example:
-
- For the Detect function, an organization might deploy intrusion detection systems or SIEM (Security Information and Event Management) tools.
- Under the Identify function, organizations may conduct comprehensive asset inventories or risk assessments to map vulnerabilities.
These examples give organizations a starting point while allowing flexibility to adapt measures based on their unique challenges and resources.
— Putting It All Together
The NIST Cybersecurity Framework is a strategy for resilience. Thanks to its capacity to adapt to evolving threats, it is a vital tool for businesses worldwide. CSF 2.0 confirms its position as the industry standard for cybersecurity management with the addition of the Govern function and usability enhancements.
Understanding CSF Tiers
The NIST Cybersecurity Framework’s CSF Tiers are essential because they give enterprises a standardized way to assess their cybersecurity maturity and practices.
Unlike a one-size-fits-all approach, the tiers allow organizations to see where they stand in their cybersecurity posture and strategically progress to more advanced levels. This ensures that their security efforts are sustainable, scalable, and aligned with their risk appetite and business goals.
The purpose of the tiers is twofold:
-
- Assessment: They help organizations identify existing gaps in their processes and capabilities.
- Goal setting: They create a roadmap for moving from less mature practices to more integrated and proactive approaches.
Characteristics of Each Tier
The CSF describes four tiers, ranging from basic to highly sophisticated levels of cybersecurity risk management. Each tier reflects an organization’s integration of cybersecurity into its overall risk management practices.
Tier 1: Partial
Organizations at Tier 1 have limited awareness and oversight of cybersecurity risks. Their practices are often reactive, addressing issues as they arise rather than being proactive or guided by a strategic plan.
Key Characteristics:
-
- Lack of formalized processes or consistent risk management practices.
- Security practices are ad hoc and may vary widely across departments.
- Little understanding of organizational risks, resulting in minimal alignment between cybersecurity and business objectives.
Challenges at This Tier:
Organizations are often highly vulnerable to threats, as there’s no coordinated, organization-wide approach to cybersecurity.
Tier 2: Risk-Informed
At this level, organizations begin to acknowledge and manage some cybersecurity risks. While processes are more structured than in Tier 1, they are not yet fully implemented consistently across the organization.
Key Characteristics:
-
- Risk management processes exist but are not integrated into enterprise-wide efforts.
- Some collaboration between IT/security teams and decision-makers, though not systematic.
- Awareness of cybersecurity risks and threats is improving, leading to more predictable security practices.
Opportunities for Growth:
Moving from Tier 2 to Tier 3 often means enhancing communication between technical and leadership teams and formalizing risk management practices.
Tier 3: Repeatable
Tier 3 organizations have established and defined cybersecurity policies, which are consistently executed across the organization. Processes are repeatable, measurable, and adaptable to new risks.
Key Characteristics:
-
- Formalized governance ensures accountability and alignment with business goals.
- Clearly defined roles and responsibilities within the security and risk management teams.
- Increased use of cybersecurity technologies and strategies that enhance resilience.
Regular, ongoing assessments help refine existing practices.
Strengths at This Tier:
Organizations at Tier 3 are better equipped to manage cybersecurity risks systematically. Their ability to quickly adapt to changes in the threat landscape is significantly stronger than Tiers 1 or 2.
Tier 4: Adaptive
Tier 4 represents the highest level of the CSF maturity model. Organizations at this level demonstrate a fully integrated, dynamic approach to cybersecurity risk management. They not only adapt to current threats but also anticipate and prepare for future challenges.
Key Characteristics:
-
- Integration of cybersecurity into all aspects of decision-making and business operations.
- Continuous monitoring and analysis of risks, using automated systems wherever possible.
- Sophisticated threat intelligence informs real-time adjustments.
Leadership involvement is ingrained in risk assessments and solutions.
Defining Advantage:
At this tier, cybersecurity practices are embedded into the organization’s culture. Decision-making is agile, and teams operate with a full understanding of how security intertwines with business success.
Practical Guidance for Implementing the NIST CSF
Implementing the NIST Cybersecurity Framework (CSF) can seem like a daunting task, especially for organizations new to structured cybersecurity practice. Yet, with a clear, methodical approach, integrating the framework into your organization’s processes can be both manageable and highly rewarding.

Step-by-Step Implementation Process
1) Initial Assessment: Understanding Current Cybersecurity Posture
The first step in any implementation process is to assess where your organization currently stands. This involves taking stock of existing cybersecurity practices, risks, and capabilities. Start by forming a cybersecurity assessment team that includes representatives from IT, operations, and, ideally, the executive level to ensure a comprehensive picture.
- Identify critical assets, systems, and data that need protection. What are the crown jewels of your business, and how are they currently protected?
- Assess existing policies, procedures, and technologies. Do they align with best practices, and are they consistently followed?
- Review past incidents and near misses. Consider how effective your responses were and whether these events exposed any vulnerabilities.
At this stage, it’s crucial to be objective. The goal isn’t to assign blame but to establish a baseline and set the stage for improvement.
2) Gap Analysis: Identifying Areas for Improvement
Once the initial assessment is complete, the next step is to identify gaps between your current posture and the desired state, as outlined by the NIST CSF. This involves mapping your current practices against the CSF Core’s Functions, Categories, and Subcategories.
- Prioritize critical functions. Start with high-impact areas that pose the greatest risk to your business.
- Evaluate resource availability. Determine whether the current budget, tools, and personnel are sufficient to close the identified gaps.
- Consider dependencies. Some security measures may rely on others (e.g., implementing multi-factor authentication often requires access control systems).
The outcome of this process should be a list of prioritized gaps categorized by urgency and resource requirements.
3) Action Planning: Prioritizing Security Controls Based on Risk Assessment
With the gaps identified, it’s time to develop a structured action plan to address them. This step focuses on translating findings from the assessment and gap analysis into actionable tasks.
- Define clear goals. What does success look like for your organization? This could range from improving threat detection capabilities to achieving compliance with regulations.
- Rank initiatives by risk. Use a risk-based approach to prioritize actions, addressing the highest vulnerabilities first.
- Set measurable objectives. Define key performance indicators (KPIs) to track progress, such as reduction in exposed vulnerabilities or improved incident response times.
These actions should be broken into manageable phases, allowing your organization to make gradual progress without overwhelming resources.
Integration with Existing Risk Management Processes
Aligning CSF with Other Frameworks and Standards
The flexibility of the NIST CSF allows organizations to integrate it with existing frameworks and standards, such as ISO 27001, COBIT, and PCI DSS. Aligning the CSF with these standards not only reduces duplication of effort but also enhances the effectiveness of your overall risk management strategy.
For example:
Organizations already following ISO 27001 can map its Annex A controls to corresponding CSF functions and categories. This ensures consistency while taking advantage of both frameworks’ strengths.
Similarly, COBIT users can leverage its governance-focused framework to complement the CSF’s operational emphasis, creating a well-rounded cybersecurity strategy.
By aligning frameworks, organizations streamline compliance efforts, reduce redundancies, and create a unified approach that resonates across departments.
Encourage Collaboration Between Teams
Integrating CSF into existing practices requires close collaboration between different organizational units. IT and cybersecurity teams must work with risk management, legal, compliance, and leadership to ensure alignment with broader business goals.
Utilizing Resources for Effective Implementation
One of the strengths of the NIST CSF lies in the resources it offers to ease implementation. From detailed guides to templates and tools, NIST provides support for organizations at every step.
– Framework Profiles
For mapping intended and existing cybersecurity policies, the CSF Profile template is a crucial tool. Organizations may match their goals with business objectives and graphically measure changes by building a Profile.
– References to Standards
The CSF links each function, category, and subcategory to available standards and guidelines, such as NIST SP 800-53. These references provide specific, actionable steps to implement the framework’s guidance.
– Online Learning and Tools
NIST offers interactive resources, including webinars and self-assessment tools. These are useful for organizations in the early stages of implementation.
Leveraging Internal and External Expertise
While NIST’s resources provide a solid foundation, many organizations may also benefit from external support, such as:
- Engaging consultants to conduct initial assessments or gap analyses.
- Training internal teams on the CSF’s concepts and practical applications.
- Partnering with vendors who specialize in CSF-aligned tools and technologies.
Common Challenges in CSF Implementation
While the NIST CSF offers powerful guidance for managing cybersecurity risks, implementing it is not without challenges. Many organizations encounter barriers that can impede progress, ranging from internal resource limitations to external knowledge gaps.
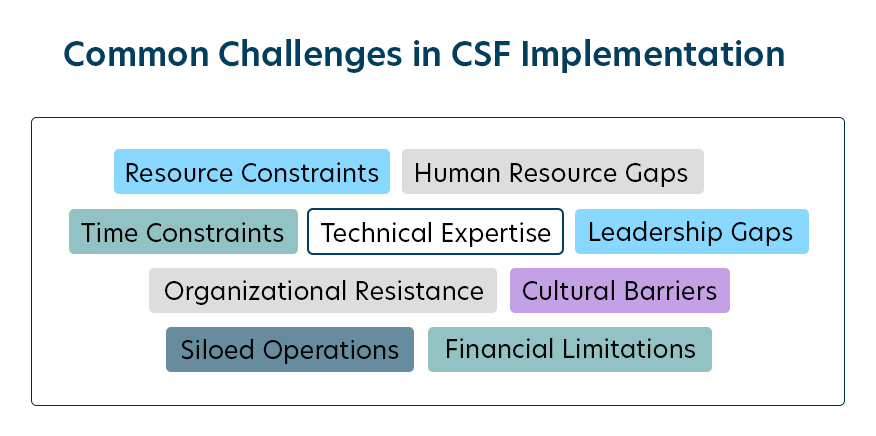
1) Resource Constraints
One of the most common challenges organizations face is inadequate resources. Both small businesses and larger enterprises can struggle to allocate the necessary time, budget, and personnel for CSF implementation.
2) Financial Limitations
Smaller organizations often find themselves constrained by limited budgets, making it difficult to invest in new technologies or hire specialized personnel.
3) Human Resource Gaps
Even larger companies may lack enough skilled staff to focus entirely on cybersecurity initiatives. Existing IT teams are often spread thin across multiple responsibilities.
4) Time Constraints
With cybersecurity being only one aspect of operational risk management, organizations may struggle to dedicate sufficient time to implementation activities amid competing priorities.
5) Technical Expertise
Many companies may lack in-house experts who understand how to translate the CSF’s guidance into operational practices. For instance, mapping categories to existing processes or creating Framework Profiles often requires specialized skills.
6) Leadership Gaps
A lack of cybersecurity awareness at the leadership level can hinder progress. Without executive buy-in, it becomes challenging to secure the necessary investment or align cybersecurity activities with strategic objectives.
7) Organizational Resistance
Resistance to change is another significant challenge, especially in organizations with deeply ingrained processes or siloed operations.
8) Cultural Barriers
Employees may view the CSF as an unnecessary burden or a threat to their established ways of working. This is particularly common in industries where cybersecurity has not historically been a priority.
9) Siloed Operations
When departments operate independently with little cross-functional collaboration, integrating the CSF across the organization becomes a daunting task.
Strategies to Overcome These Challenges
– Training and Education for Staff
Building a knowledgeable, empowered workforce is one of the most effective ways to overcome implementation barriers. Training ensures that employees at all levels understand the CSF and their role in its success.
– Start with Leadership
When leaders grasp the value of cybersecurity and how it aligns with business objectives, they are more likely to allocate resources and champion the initiative. Training should focus on the strategic aspects, such as risk management, compliance benefits, and how the CSF integrates with overall business planning.
– Empower IT and Cybersecurity Teams
Technical teams need detailed training on how to interpret and operationalize the CSF’s Functions, Categories, and Subcategories. NIST offers numerous resources which can be incorporated into professional development programs.
– Expand Awareness Organization-Wide
Cybersecurity is not solely an IT responsibility. Every employee plays a role in maintaining security. Providing general awareness training about common threats (e.g., phishing scams), basic security protocols, and the organization’s cybersecurity goals fosters a sense of shared responsibility.
Effective training improves not only technical capability but also organizational alignment. It ensures that everyone understands their contribution to the bigger picture.
Conclusion
The NIST CSF has been thoroughly discussed in this whitepaper, offering insights into its structure, application, and key benefits. Here’s a quick summary of the critical points discussed:
Six Core Functions of the NIST CSF
The CSF is built around six essential functions, which together provide a holistic approach to cybersecurity risk management:
-
- Identify: Understand and manage risks to systems, assets, data, and capabilities through awareness of organizational priorities.
- Protect: Develop safeguards to ensure continued service delivery, including access controls, awareness training, and protective technologies.
- Detect: Implement timely identification of cybersecurity events by utilizing continuous monitoring and anomaly detection tools.
- Respond: Plan and execute necessary actions to contain and mitigate the impact of cybersecurity incidents, ensuring minimal disruption.
- Recover: Focus on resilience by restoring services and data after incidents while incorporating lessons learned back into planning.
- Govern (Introduced in CSF 2.0): Elevate governance by aligning cybersecurity leadership with organizational priorities, ensuring oversight at the executive level.
CSF Tiers as a Maturity Model
The four maturity tiers — Partial, Risk-Informed, Repeatable, and Adaptive — provide organizations with a clear way to assess and improve their maturity in managing cybersecurity risks.
These tiers help bridge technical activities with business objectives, enabling executives to back decisions with measurable risk insights.
Practical Strategies for Implementation
- Begin with an assessment of your current cybersecurity posture using the CSF’s framework as a reference point.
- Prioritize and address identified gaps, ensuring efforts align with business goals.
- Integrate the CSF with other existing risk management systems like ISO 27001 for continuity and efficiency.
- Tackle challenges — such as limited resources or resistance to change — through ongoing employee education and leadership advocacy.
Responding to Emerging Challenges
Here’s what the future of cybersecurity frameworks might hold:
Enhanced Functions and Framework Governance
The addition of the Govern function highlights the growing recognition of cybersecurity as a critical leadership concern. Having executives involved in security planning ensures strategies are not only responsive but forward-thinking.
Addressing New Technologies
With AI, IoT, and quantum computing creating fresh threats and opportunities, frameworks like the CSF must provide revised guidance on using these technologies securely while mitigating associated risks.
Prioritizing Resilience
The shift from prevention to resilience reflects the realistic understanding that no system can prevent every attack. Future frameworks will focus even more on incident response, recovery, and adaptability post-breach.
Global Cybersecurity Alignment
Global collaboration on unified cybersecurity standards is increasingly vital. Future updates to the CSF will likely emphasize interoperability and international cooperation.
Automation and AI-Powered Security
The incorporation of automated tools for threat detection, incident response, and compliance tracking will become a staple of cybersecurity best practices. However, managing these technologies ethically and securely will require careful guidance from frameworks like the CSF.
Moving Forward
For organizations seeking to stay ahead in today’s security environment, the NIST CSF provides a comprehensive and adaptable approach. Here’s how you can prepare for sustained cybersecurity effectiveness:
-
- Continuously evaluate and evolve your cybersecurity practices in line with the six core functions of the NIST CSF.
- Monitor technological advancements and regulatory trends, adapting your strategies to remain compliant and proactive.
- Foster collaboration between decision-makers, cybersecurity professionals, and external stakeholders to build an integrated security culture across all levels of the organization.
Final Thoughts
Cybersecurity is no longer just a defensive measure; it’s a strategic enabler of trust, innovation, and long-term business success. By understanding and leveraging the NIST CSF, your organization can build a robust foundation to withstand evolving threats.
Looking to implement the NIST Cybersecurity Framework with confidence? Start by downloading our free NIST CSF Implementation Checklist, your step-by-step guide to assessing risks and prioritizing improvements.
Need expert support? Schedule a personalized consultation with TrustNet’s cybersecurity professionals to create a tailored strategy and tackle your challenges head-on.
Appendices
Glossary of Terms
-
- Cybersecurity Framework (CSF)
A structured outline designed by NIST to help organizations manage and reduce cybersecurity risks based on industry standards and best practices. - CSF Core
The central component of the NIST CSF consists of six primary functions — Identify, Protect, Detect, Respond, Recover, and Govern. These functions collectively offer a comprehensive approach to addressing and managing cybersecurity risks. - Govern Function
A function introduced in CSF 2.0 focuses on aligning cybersecurity policies and activities with organizational objectives while ensuring leadership oversight and accountability. - CSF Tiers
The four levels (Partial, Risk-Informed, Repeatable, Adaptive) describe an organization’s maturity and consistency in implementing cybersecurity risk management practices. - Risk Management Framework (RMF)
A process designed to integrate security and privacy into the system development lifecycle, often used alongside the NIST CSF for cohesive risk management.
- Cybersecurity Framework (CSF)
Additional Resources and References
-
- NIST Cybersecurity Framework (CSF) Homepage
NIST CSF Overview and Resources - Risk Management Framework (RMF) Resources. A companion framework often used for implementing effective risk management processes. RMF Resources from NIST
- CSF 2.0. Explore updates to the framework, including the addition of the “Govern” function to further emphasize organizational oversight.
CSF 2.0 Information - Cybersecurity and Infrastructure Security Agency (CISA) Tools. Access tools and services to build organizational security and resilience.
CISA Resources
- NIST Cybersecurity Framework (CSF) Homepage
External Resources
-
- ISO/IEC 27001 – International standard for information security management systems. More on ISO/IEC 27001
- Center for Internet Security (CIS) Controls – A prioritized set of actions to protect systems and data. More on CIS Controls
Subscribe to the TrustNet Newsletter
actionable cybersecurity strategies, and TrustNet’s cutting-edge solutions.




