Beginner’s Guide: SOC 2 Compliance in 2025

TL;DR
SOC 2 is a leading security and compliance framework essential for SaaS and cloud providers handling customer data. This guide breaks down everything beginners need to know in 2025, from understanding the Trust Services Criteria and audit types to preparing for certification, avoiding pitfalls, and streamlining compliance with tools like GhostWatch. Learn how to build trust, reduce risk, and get audit-ready with a step-by-step roadmap from scoping to ongoing compliance.
SOC 2 is a security and compliance framework created by the American Institute of Certified Public Accountants (AICPA). It assesses how well a service provider manages customer data based on five trust service criteria: security, availability, processing integrity, confidentiality, and privacy. For SaaS companies, cloud providers, and other tech-driven organizations, SOC 2 compliance is critical for growth and credibility.
Achieving SOC 2 certification shows your customers and partners that you follow strict security controls and can be trusted with sensitive data. It helps reduce risk, strengthen your brand, and meet the expectations of security-conscious clients.
This beginner’s guide walks you through the entire SOC 2 journey. You’ll learn:
-
-
- What SOC 2 is and why it matters
- How the SOC 2 framework is structured
- What you need to prepare for an audit
- How the audit process works
- What it takes to stay compliant over time
-
Let’s get started with the basics.
What is SOC 2? Understanding the Framework
SOC 2 was created to evaluate how service organizations manage and protect customer data based on a defined set of criteria known as the Trust Services Criteria. This framework focuses on the internal controls relevant to information security and applies to any company that stores or processes client data in the cloud.
At the core of SOC 2 are the five Trust Services Criteria (TSC), sometimes referred to as the trust service principles. These criteria define the control objectives used to evaluate a company’s systems and practices.
The Five Trust Services Criteria
Security
Information and systems are protected against unauthorized access, unauthorized disclosure of information, and damage to systems that could compromise the availability, integrity, confidentiality, and privacy of information or systems and affect the entity’s ability to achieve its objectives. Security refers to the protection of
- information during its collection or creation, use, processing, transmission, and storage, and
- systems that use electronic information to process, transmit or transfer, and store information to enable the entity to meet its objectives.
Availability
Information and systems are available for operation and use to meet the entity’s objectives.
Processing Integrity
System processing is complete, valid, accurate, timely, and authorized to meet the entity’s objectives.
Confidentiality
Information designated as confidential is protected to meet the entity’s objectives. Confidentiality addresses the entity’s ability to protect information designated as confidential from its collection or creation through its final disposition and removal from the entity’s control in accordance with management’s objectives.
Privacy
Personal information is collected, used, retained, disclosed, and disposed of to meet the entity’s objectives.
Each of these criteria contributes to a comprehensive approach to information security:
-
-
- Security is the foundation that supports the other four.
- Availability ensures data and systems remain accessible.
- Processing Integrity guarantees that data is handled correctly and without error.
- Confidentiality prevents exposure of sensitive information.
- Privacy focuses on protecting personal data and complying with evolving data protection laws.
-
Together, these criteria shape the SOC 2 framework and guide organizations in protecting what matters most, customer trust and data integrity.
Work with AICPA-Accredited SOC 2 Auditors You Can Trust
TrustNet carries the expertise to navigate your organization through the complex landscape of SOC 2 compliance
Why SOC 2 Matters: Benefits and Market Expectations
SOC 2 compliance has become a baseline requirement in today’s SaaS and cloud services market. Customers, partners, and investors increasingly demand SOC 2 reports before signing contracts, especially in regulated industries like healthcare, finance, and enterprise IT.
Achieving SOC 2 certification signals that your organization takes security and data protection seriously. It builds immediate trust with technical evaluators and procurement teams.
Key Benefits of SOC 2 Compliance
— Win more deals
Enterprise customers often require SOC 2 as part of their vendor selection process. Having a report on hand can accelerate sales cycles.
— Demonstrate trust and transparency
A SOC 2 report shows you’ve implemented rigorous controls and submitted to third-party validation.
— Align with industry standards
SOC 2 complements other compliance frameworks like ISO 27001 and helps you meet overlapping regulatory requirements.
— Reduce business and security risks
The process of preparing for a SOC 2 audit improves internal controls and strengthens your security posture.
SOC 2 is no longer optional; it’s expected. Getting certified gives your company a clear edge in a competitive, trust-driven market.
SOC 2 Requirements: What You Need to Know
To prepare for a SOC 2 audit, you need to establish and maintain a robust information security program. This includes documented policies, technical safeguards, and clearly defined processes.
Core SOC 2 Requirements
1. Information Security Program
Develop and maintain a formal security program that defines how your organization protects systems and data.
2. Documented Policies and Procedures
Create and enforce written policies across areas like access control, data retention, system operations, and change management.
3. Risk Assessment
Conduct and document periodic risk assessments to identify threats and determine how to mitigate them.
4. Access Management
Enforce least privilege access, role-based permissions, user provisioning and deprovisioning, and strong authentication methods.
5. Incident Response Plan
Establish a tested plan to detect, respond to, and recover from security incidents.
6. System Logging and Monitoring
Collect and monitor audit logs for key systems to detect suspicious activity and maintain accountability.
7. Vendor Risk Management
Evaluate and document third-party risks, especially for critical service providers and infrastructure partners.
8. Vulnerability and Penetration Testing
Perform regular vulnerability scans and penetration tests. Document remediation steps for any findings.
9. Annual Policy Reviews and Control Testing
Review all policies and controls at least once per year and update them to reflect changes in the environment or threat landscape.
10. Evidence Collection Is Critical
You must gather and retain evidence to prove that your controls are implemented and operating effectively. This includes screenshots, logs, policy documents, training records, and system reports. Auditors will review this documentation to determine whether your organization meets SOC 2 requirements.
SOC 2 Types: Type I vs. Type II
When pursuing SOC 2 compliance, organizations must choose between two types of audit reports: Type I and Type II. Both are conducted under the AICPA’s attestation standards but serve different purposes.
SOC 2 Type I
A Type I report evaluates the design and implementation of controls at a specific point in time. The auditor reviews whether your systems and policies are suitably designed to meet the Trust Services Criteria as of the audit date. This type is often used as a starting point for organizations building their compliance foundation.
SOC 2 Type II
A Type II report assesses not only control design but also operational effectiveness over a period of time, typically a minimum of three months, with most audits covering 6 to 12 months. The auditor tests samples and evidence to confirm that controls function consistently and reliably across that duration.
Why Type II Matters More
While both types are valid, most customers and partners expect a Type II report. It offers stronger assurance because it demonstrates that your organization not only has proper controls in place but also applies them consistently in real-world operations. For enterprise sales and long-term trust, a Type II report carries more weight and credibility.
The SOC 2 Compliance Journey: Step-by-Step Roadmap
SOC 2 compliance is a structured, multi-phase process. Each step helps build a foundation of trust, prepares your systems for audit, and ensures long-term adherence to the Trust Services Criteria. Here’s how the journey typically unfolds:
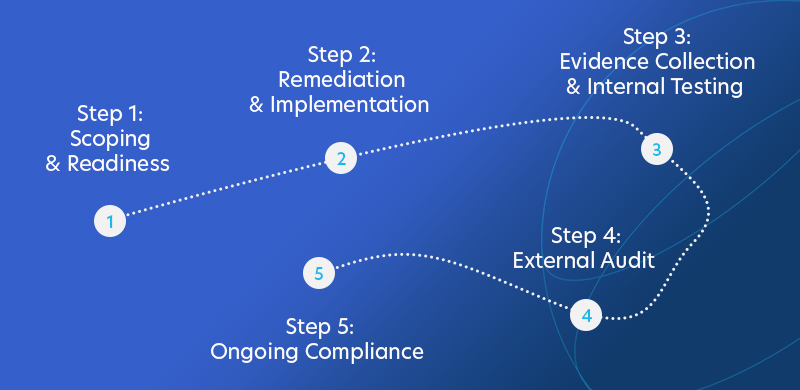
Step 1: Scoping & Readiness
-
- Define the scope of the audit, including systems, processes, and vendors that handle customer data.
- Choose which TSC applies to your business.
- Conduct a gap analysis to identify missing controls or documentation.
Step 2: Remediation & Implementation
-
- Close control gaps by implementing technical and administrative safeguards.
- Deploy key measures like encryption, multi-factor authentication (MFA), and access controls.
- Draft and formalize security and compliance policies.
- Train employees on procedures and run tabletop exercises to test your incident response plan.
Step 3: Evidence Collection & Internal Testing
-
- Document all control activities, such as change logs, access reviews, and policy acknowledgments.
- Perform self-assessments to evaluate control effectiveness.
- Remediate any issues found before the external audit.
Step 4: External Audit
-
- Engage an AICPA-accredited firm like TrustNet to conduct the audit.
- Participate in auditor walkthroughs and provide supporting evidence.
- Review and finalize the SOC 2 audit report.
Step 5: Ongoing Compliance
-
- Monitor controls continuously and track system changes.
- Review and update policies regularly.
- Conduct internal audits and prepare for annual recertification if pursuing Type II.
SOC 2 Audit Timeline, Cost, and Tools
SOC 2 compliance involves careful planning, a defined audit window, and a commitment to operational rigor. Understanding the typical timeline and cost helps organizations allocate resources more effectively and avoid delays.
Timeline Estimates
SOC 2 Type I
Typically completed in 2 to 3 months. It evaluates the design and implementation of controls at a specific point in time.
SOC 2 Type II
Requires 6 to 12 months. It assesses whether controls operate effectively over an extended period, based on evidence collected throughout the audit window.
Cost Range
The cost of a SOC 2 audit generally falls between $20,000 and $80,000, depending on:
-
- Scope of Trust Services Criteria
- Type of audit (Type I or II)
- Complexity of systems and vendor ecosystem
- Internal readiness
- Choice of auditor and supporting technology
- Unexpected costs often arise from remediation, documentation efforts, or repeated audit cycles when processes lack structure.
Simplify Compliance with GhostWatch
GhostWatch by TrustNet is a Managed Security and Compliance platform that removes friction from the SOC 2 process. Designed for organizations seeking a smarter path to certification, GhostWatch addresses the most common pain points:
24/7 Monitoring
GhostWatch continuously scans systems for vulnerabilities, notifies teams of risks in real time, and supports rapid remediation. This proactive oversight eliminates blind spots and keeps controls active around the clock.
Automated Evidence Collection
Instead of manual tracking, GhostWatch captures logs, policy changes, and system activities automatically. This speeds up audit prep, reduces human error, and ensures documentation is always up to date.
Custom Compliance Frameworks
GhostWatch adapts to your organization’s unique systems and workflows. It builds tailored control frameworks that align with your risk profile, avoiding unnecessary complexity and making compliance achievable without disruption.
Real-Time Reporting and Dashboards
Teams access intuitive dashboards with compliance scores, task assignments, and audit-readiness indicators. Reports offer actionable insights, helping teams stay ahead of issues and reduce audit findings.
Proactive Security
GhostWatch doesn’t just help you meet SOC 2 requirements, it improves your security posture. It detects threats, offers remediation recommendations, and prevents issues before they impact your audit timeline.
Results You Can Expect
GhostWatch clients report saving 80+ hours per audit through automation and streamlined control mapping. With more than 100 frameworks supported (including SOC 2, ISO 27001, and NIST CSF), GhostWatch helps you scale security and compliance across your organization without duplicated work.
Best Practices for SOC 2 Success
SOC 2 compliance is more than a one-time project. It requires ongoing attention, cross-functional alignment, and a proactive mindset. The following best practices will help your organization build a stronger security posture and ensure audit success.
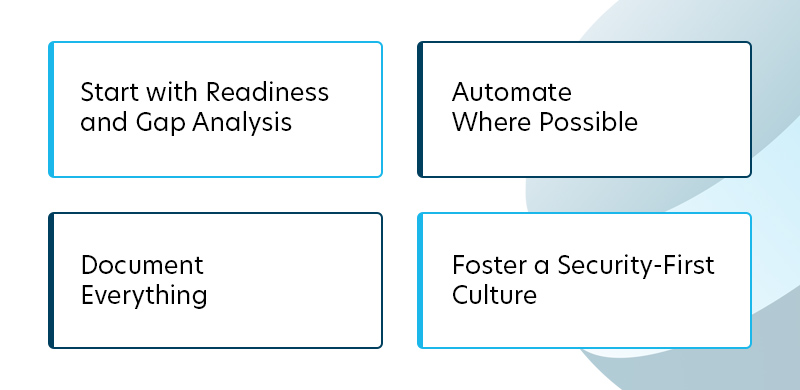
Start with Readiness and Gap Analysis
-
- Perform a formal readiness assessment to understand your current state.
- Identify missing controls, documentation, or technical safeguards.
- Prioritize remediation based on audit scope and business risk.
Document Everything
-
- Maintain up-to-date policies and procedures across all in-scope systems.
- Collect and organize supporting evidence, access logs, approvals, training records, and incident response tests.
- Ensure documentation reflects actual day-to-day practices.
Automate Where Possible
-
- Use compliance automation tools like GhostWatch to monitor and control health in real time.
- Automate evidence collection, alerts, and reporting to reduce manual effort.
- Track exceptions and remediation workflows through a centralized system.
Foster a Security-First Culture
-
- Train employees on security policies and SOC 2 responsibilities.
- Conduct regular reviews and testing of controls.
- Emphasize continuous improvement, not checkbox compliance.
By following these best practices, your organization can reduce audit fatigue, minimize risk, and build lasting trust with customers and partners.
SOC 2 Beginner FAQs
— What is SOC 2, and who needs it?
SOC 2 is a security and privacy compliance framework developed by the AICPA. It applies to service organizations, especially SaaS, cloud, and tech providers, that store or process customer data.
— What are the five Trust Services Criteria?
The SOC 2 framework is built on five Trust Services Criteria: Security, Availability, Processing Integrity, Confidentiality, and Privacy. These criteria define the control objectives that auditors evaluate during a SOC 2 audit.
— How long does SOC 2 compliance take?
The timeline depends on your audit type and readiness. A SOC 2 Type I audit typically takes 2–3 months, as it assesses control design at a specific point in time. A SOC 2 Type II audit usually takes 6–12 months, since it evaluates the operating effectiveness of those controls over a defined period.
— What is the difference between Type I and Type II?
Type I evaluates control design at a point in time. Type II tests whether controls operate effectively over a longer period, usually 3–12 months.
— What are common SOC 2 audit pitfalls?
Missing documentation, lack of evidence, unclear access controls, and untested incident response plans are common reasons companies fail audits.
— How do I choose a SOC 2 auditor?
Look for an AICPA-accredited audit firm like TrustNet that has direct industry experience, a collaborative approach, and clear guidance on readiness and reporting.
— Can I automate SOC 2 compliance?
Yes. Platforms like GhostWatch automate evidence collection, control monitoring, and compliance reporting, saving time and reducing audit risk.
What to Do Next: Your Path to SOC 2 Compliance
SOC 2 compliance is a powerful trust signal that helps your business stand out, close more deals, and protect what matters most. Whether you’re a growing SaaS company or an established cloud provider, getting certified shows your commitment to security and transparency.
Request a free consultation with TrustNet experts today. Get a clear roadmap, actionable insights, and hands-on support from an AICPA-accredited team that’s helped hundreds of companies succeed.
Subscribe to the TrustNet Newsletter
actionable cybersecurity strategies, and TrustNet’s cutting-edge solutions.




