Jul 12, 2024 | Blog, Compliance, ISO 27001
Blog The ISO 27001 Checklist for Your Business The ISO 27001 Checklist for Your Business ISO 27001, an internationally recognized standard for information security management systems (ISMS), provides a robust framework to protect your organization’s data. This...

Jul 12, 2024 | Blog, Compliance, ISO 27001
Blog ISO 27001 Essentials – Creating a Secure Framework ISO 27001 Essentials – Creating a Secure Framework In this digital age, information security is essential for any firm. ISO 27001 provides a comprehensive framework for managing and protecting sensitive data....

Jul 1, 2024 | Blog, Compliance, SOC, SOC 2
Blog Tackling Advanced SOC 2 Compliance Issues Tackling Advanced SOC 2 Compliance Issues In today’s fast-evolving world of cybersecurity, SOC 2 compliance is no walk in the park. The more companies grow and adopt new technologies, the harder it becomes for...

Jun 27, 2024 | Blog, SOC, SOC 2
Blog Starting Your SOC 2 Journey – The Essential Guide Starting Your SOC 2 Journey – The Essential Guide In the modern business environment, compliance with SOC 2 is essential. When you receive SOC 2 certification, it allows you to create trust and demonstrate your...

Jun 20, 2024 | Blog, Case Studies, SOC, SOC 2
Blog TrustNet’s Success Stories in SOC 2 Audits TrustNet’s Success Stories in SOC 2 Audits As the leader in successfully completing SOC 2 audits, TrustNet offers businesses the know-how and direction they require to comply with regulations and improve data...

Jun 7, 2024 | Blog, Compliance, PCI DSS Compliance
Blog PCI Compliance Fee: Cost & Penalties Explained by Experts PCI Compliance Fee: Cost & Penalties Explained by Experts PCI DSS (Payment Card Industry Data Security Standard) compliance is crucial for businesses handling cardholder data to protect against...

May 22, 2024 | Blog, Managed Security, Network Security
Blog TrustNet’s Key Takeaways from RSA Conference 2024: AI, Quantum Computing, and More TrustNet’s Key Takeaways from RSA Conference 2024: AI, Quantum Computing, and More The RSA Conference 2024 has been a platform for cybersecurity brainstorming and discussions....
May 21, 2024 | Blog, Managed Security, Network Security
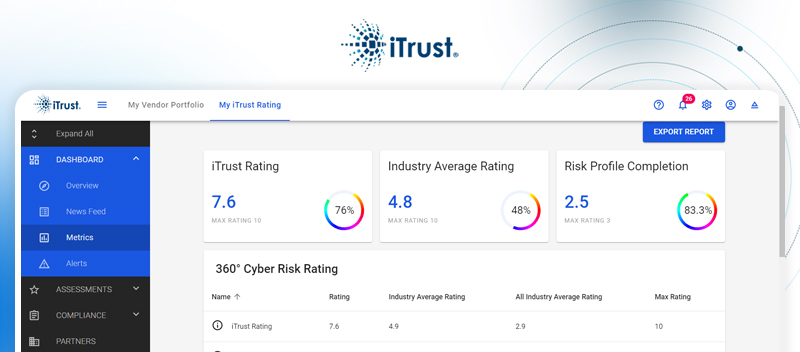
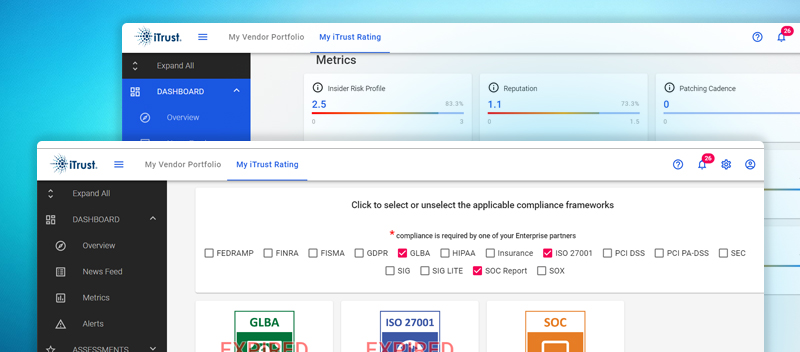
Blog Evaluating Cyber Risks: How iTrust Paves the Way for Secure Business Evaluating Cyber Risks: How iTrust Paves the Way for Secure Business Ratings for cyber risks have become a must-have in the current digital field. It quantifies how secure an organization is...

May 18, 2024 | Blog, Compliance
Blog Compliance Without Complications: GhostWatch’s Managed Compliance Solutions Compliance Without Complications: GhostWatch’s Managed Compliance Solutions The broad spectrum of compliance regulations is becoming more complicated in the fast-paced business sector....

May 18, 2024 | Blog, Compliance, Managed Security
Blog The Dual Power of GhostWatch: Security and Compliance Unveiled The Dual Power of GhostWatch: Security and Compliance Unveiled Lately, there’s been a noticeable uptick in cyber threats, and the cunning of hackers and cybercriminals is growing by the day....

May 17, 2024 | Blog, Information Security, Managed Security, Network Security
Blog Launching a Safer Future: Meet GhostWatch and iTrust – New Solutions from TrustNet Launching a Safer Future: Meet GhostWatch and iTrust – New Solutions from TrustNet At TrustNet, we lead the way in compliance and cybersecurity and are renowned for our potent and...