HIPAA Compliance: Understanding Standard Transactions and Data Storage Requirements

Protecting sensitive patient information isn’t just a priority in healthcare; it’s a legal obligation. HIPAA compliance ensures that healthcare providers, health plans, and business associates handle data with care and in line with strict regulations. Yet, while the importance of compliance is clear, understanding exactly what’s required isn’t always so simple.
Concerns about standard transactions? Are you unsure about the best way to keep electronic health records? Due to these difficulties, businesses may be at risk of data breaches or significant fines for non-compliance. Without clarity, patient trust and the stability of your operation hang in the balance.
This article will break down HIPAA’s key expectations, focusing on standard transactions and secure data storage requirements. We’ll provide practical tips for maintaining compliance, identify common missteps that could put your organization at risk, and leave you with resources to simplify your compliance process.
Understanding HIPAA Regulations
HIPAA, or the Health Insurance Portability and Accountability Act (HIPAA) of 1996, was established to protect patient health information while empowering individuals with more control over their personal data. It’s a legal framework designed to ensure that sensitive information is handled with the utmost care and security.
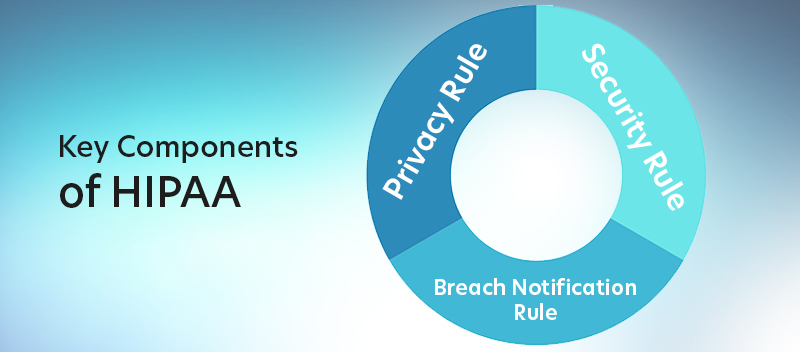
— Privacy Rule
The Privacy Rule governs the use and disclosure of Protected Health Information (PHI), which includes any information that can identify a patient and relates to their health, healthcare services, or payment for such services. This rule ensures that PHI is shared only when necessary — to enhance care, comply with legal requirements, or for other permitted purposes — while maintaining strict confidentiality. It emphasizes the “minimum necessary” standard, meaning that only the information needed for a specific purpose is used or disclosed.
Furthermore, the Privacy Rule provides patients with significant rights, such as access to their medical records and the ability to request corrections if the information is inaccurate. It applies to covered entities, including healthcare providers, health plans, and healthcare clearinghouses, ensuring a consistent approach to safeguarding patient information.
— Security Rule
The Security Rule addresses electronic Protected Health Information (ePHI), which is PHI created, stored, transmitted, or received in electronic form. Unlike general PHI, which includes all formats—written, oral, and digital—ePHI requires specific digital security measures.
To safeguard ePHI, the rule outlines three protections:
- Administrative safeguards: Policies and procedures along with training to manage data access and information security
- Physical safeguards: Controlling facility access and securing devices or workstations
- Technical safeguards: Encryption, secure passwords, and data transmission protocols
Essentially, the Security Rule ensures that ePHI is protected whether it’s stored, accessed, or sent digitally.
— Breach Notification Rule
Mistakes happen, but HIPAA mandates how organizations respond when they do. The Breach Notification Rule requires covered entities and business associates to notify affected individuals if a breach compromises their PHI.
Depending on the scope, covered entities and business associates may also need to inform the Department of Health and Human Services and, in some cases, the media. Timely reporting helps promote accountability and gives stakeholders the information they need to protect themselves.
We have highlighted three major HIPAA rules, but take note that additional rules, such as the Enforcement Rule, Omnibus Rule, Transaction and Code Set Rule, and Unique Identifiers Rule, also contribute to creating a comprehensive framework to protect patient health information.
For more information on our HIPAA Compliance services, Click Here
Standard Transactions Under HIPAA
One of the main elements of HIPAA’s administrative simplification requirements is standard transactions. These interactions pertain to categories of electronic healthcare information exchanges, including eligibility queries, payments, and claims.
Every kind of transaction needs to adhere to a set format, guaranteeing accurate and efficient data transfer across systems. The goal? To create a unified approach that reduces administrative burdens while protecting sensitive patient information.
What Are Standard Transactions?
Under HIPAA, standard transactions are electronic activities commonly performed between healthcare organizations. These include:
-
- 837 – Claims and Encounter Information and Coordination of Benefits (COB): Involve submitting healthcare service claims to insurers for reimbursement and managing COB details
- 276/277 – Claims Status: Used to inquire about and respond to the status of submitted claims, enabling providers to track claim processing efficiently
- 270/271 – Eligibility Benefit Inquiry and Response: Allow organizations to verify a patient’s insurance coverage, benefits, and eligibility information
- 835 – Payment Remittance and Advice: Facilitate the exchange of payments, explanations of benefits (EOBs), and detailed claim transaction data between providers and payers
- 278 – Referral Certification and Authorization: Used to handle requests for treatment authorizations or specialist referrals, ensuring appropriate approvals are in place
- 834 – Health Plan Enrollment and Disenrollment: Manage the enrollment or disenrollment of individuals in health plans, streamlining membership updates
- 820 – Premium Payments: Enable the exchange of premium payment details between employers or other entities and health plans for accurate financial processing.
Why Are Standard Transactions Important?
Standard transactions are crucial because they simplify a complicated and sometimes disjointed system. Healthcare institutions would have difficulty correctly and safely transferring data without a defined method. Imagine the chaos of multiple systems trying to interpret information differently.
Here’s why standard transactions matter:
– Improved Efficiency
The use of these standardized formats eliminates inconsistencies, making it easier for all parties — providers, payers, and clearinghouses — to communicate seamlessly.
Standardized formats also save time by automating key processes like claims submissions and eligibility checks.
– Enhanced Security
By using HIPAA-compliant transaction standards, organizations ensure that sensitive patient data is encrypted and protected during exchanges.
– Cost Reduction
When processes are streamlined, organizations spend less on administrative overhead and paperwork.
– Interoperability
Standardization ensures that different systems can “speak the same language,” enabling smooth communication even among organizations using different platforms.
Data Storage Rules
When protecting patient information, how you store data is just as important as how you use or share it. HIPAA’s requirements for data storage are designed to ensure that PHI and ePHI remain confidential, accessible only to authorized personnel, and safeguarded against breaches. Whether you’re storing digital records or physical files, compliance with these requirements is non-negotiable.
HIPAA Requirements for Data Storage
HIPAA establishes specific guidelines to protect PHI and ePHI during storage. Here’s what you need to know:
Physical Safeguards
For physical records, HIPAA requires strict control over access to facilities and storage rooms. File cabinets and storage units containing PHI should be locked, and only authorized personnel should have access to keys or combinations.
For ePHI, physical safeguards are equally critical. Organizations must ensure workstations are positioned to prevent unauthorized viewing of sensitive information and implement policies for proper workstation use. Device and media controls, such as tracking hardware, securely disposing electronic media, and restricting access to equipment, further protect information systems and related facilities from breaches or misuse.
Technical Safeguards
To protect ePHI, HIPAA outlines several categories of technical safeguards:
- Access Controls: Ensure only authorized personnel can access ePHI. Examples include implementing strong passwords, multi-factor authentication (MFA), and role-based access controls (RBAC).
- Audit Controls: Track and monitor access to ePHI through electronic systems. Examples include maintaining audit logs to detect unauthorized activities and conducting regular reviews.
- Integrity Controls: Prevent and identify unauthorized changes to ePHI. Examples include implementing checksum verification and using tools to ensure data remains accurate and unaltered.
- Person or Entity Authentication Controls: Verify the identity of individuals accessing ePHI. Examples include requiring unique usernames, biometric verification, or secure login credentials.
- Transmission Security: Protect ePHI when transmitted electronically. Examples include encryption protocols for data transmission and secure communication channels to prevent interception by unauthorized users.
Retention and Disposal
HIPAA does not mandate a retention period for medical records; this is governed by federal and state laws and the most stringent standard should be followed. Instead, HIPAA requires covered entities and business associates to retain documents and records that demonstrate HIPAA compliance. At a minimum, HIPAA-related records should be retained for at least six years from the date they were created or were last in effect, whichever is later. HIPAA-related documents include information security and privacy policies, risk assessments, authorization forms for PHI disclosure, and other compliance documents.
HIPAA also requires that when records are no longer needed, they be disposed of securely. For physical records, shredding or incineration is standard. For digital data, secure wiping methods ensure nothing can be recovered.
Failure to meet data disposal standards can lead to significant fines, loss of patient trust, and legal consequences.
Best Practices for Securing Patient Data
While meeting HIPAA’s data storage requirements is essential, adopting best practices can further strengthen your organization’s compliance and security:
– Encrypt ePHI
Whether ePHI is at rest or in transit, encryption ensures that even if data is accessed without authorization, it remains unreadable.
– Regularly Update Security Protocols
Cyber threats evolve constantly. Ensure your systems, software, and antivirus protections are regularly updated and patched to address new vulnerabilities.
– Implement Role-Based Access (RBAC)
Not everyone on staff needs access to all patient data. Use RBAC to limit PHI and ePHI access to only those who need it to perform their job responsibilities.
– Audit and Monitor Systems
Conduct regular audits to identify and fix weak spots in your data storage policies. Logging and monitoring access to ePHI can also help detect unauthorized attempts to breach your systems.
– Backup Data Securely
Regular backups ensure data is not lost due to ransomware attacks or system failures. Store backups securely and test restoration processes periodically to confirm they work when needed.
– Train Your Team
Technology alone is not enough. Your staff plays a crucial role in safeguarding data. Conduct regular training to update employees on HIPAA requirements and the latest security protocols.
By combining these best practices with a thorough understanding of HIPAA’s data storage rules, your organization can significantly reduce risks while maintaining patient confidence.
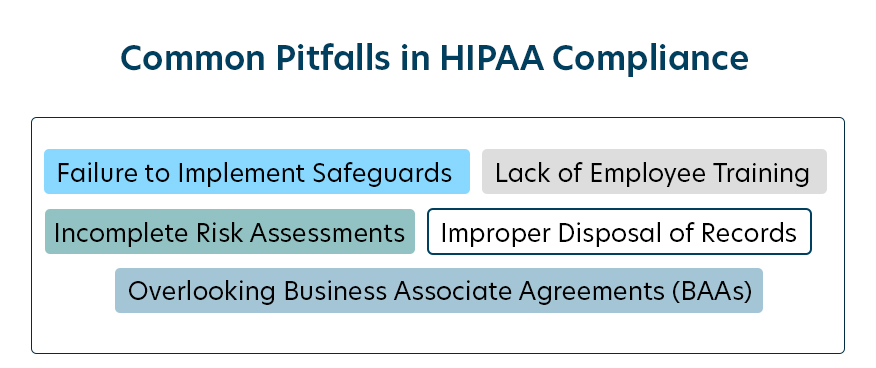
Mistakes can creep into day-to-day operations, and even small errors can have serious repercussions. By identifying these pitfalls ahead of time, you can avoid costly consequences and protect your organization’s reputation.
Identifying Common Mistakes
Many organizations struggle with the complexity of HIPAA regulations, leading to frequent mistakes such as:
Lack of Employee Training
Without proper HIPAA training, employees might mishandle PHI, fail to recognize red flags, or fall victim to phishing scams — putting patient data at risk.
Failure to Implement Safeguards
Some organizations neglect to establish the required physical, technical, or administrative safeguards. This might include leaving physical files unsecured, skipping encryption for electronic data, or overlooking routine audits.
Incomplete Risk Assessments
Skipping or conducting insufficient risk assessments hinders an organization’s ability to timely identify and fix vulnerabilities. HIPAA mandates annual and thorough risk evaluations.
Improper Disposal of Records
Tossing old records into a landfill or deleting files without secure methods creates opportunities for data breaches. Both physical and electronic records require proper destruction to protect sensitive information.
Overlooking Business Associate Agreements (BAAs)
Any vendor or partner with access to PHI is legally required to sign a BAA outlining privacy and security expectations. Failing to secure these agreements can quickly lead to compliance issues.
Consequences of Non-Compliance
HIPAA violations, whether intentional or accidental, can carry serious consequences. Penalties vary depending on the extent of the violation and the level of negligence. Here’s what’s at stake:
Civil Monetary Penalties
Fines range from $141 to $2,134,831 per violation. These penalties are scaled based on the severity of the offense, with higher fines applied to willful neglect or repeated non-compliance.
Criminal Penalties
For more severe violations, such as knowingly mishandling PHI, individuals or organizations may face criminal sanctions, including hefty fines and jail time.
Civil Lawsuits
State attorneys general are authorized to file lawsuits for HIPAA violations, often resulting in additional financial damages. This adds another layer of legal and financial risk, especially for organizations that fail to respond to issues promptly.
Loss of Reputation
Beyond the monetary impact, breaches of PHI can erode patient trust. Once confidence is lost, it can be much harder for an organization to recover professionally.
Corrective Action Plans
Organizations found in violation of HIPAA may be required to implement a corrective action plan. This involves creating new policies, upgrading security measures, and providing extensive HIPAA training for staff. These steps, while necessary, can be time-consuming and expensive.
HIPAA compliance isn’t optional, but with proper diligence and preparation, it doesn’t have to be overwhelming, either.
Practical Tips for Achieving Compliance
HIPAA compliance isn’t a one-time task. It’s an ongoing process that requires structure, attention to detail, and regular evaluation.
Developing a Compliance Strategy
A well-thought-out compliance strategy is the foundation for meeting HIPAA requirements. Here are some steps to guide your approach:
1. Appoint a Compliance Officer
Designate a dedicated compliance officer or team responsible for overseeing all HIPAA-related initiatives. This ensures accountability and centralizes decision-making.
2. Conduct Annual Risk Assessments
Regularly review your organization’s systems, processes, and policies to identify potential vulnerabilities. This is not only a HIPAA requirement, but also a vital step in proactively addressing risks before they become issues.
3. Create Comprehensive Policies and Procedures
Establish clear guidelines for handling PHI and ePHI. This includes rules for data access, storage, sharing, and disposal. Make sure these policies are both detailed and accessible to your team.
4. Provide Ongoing HIPAA Training
Equip employees with the skills and knowledge they need to handle PHI and ePHI securely. Regular training sessions keep everyone up to date on the latest regulations and strategies for avoiding breaches.
5. Implement Effective Safeguards
Use a layered approach to securing PHI and ePHI, including physical protections, technical defenses, and administrative controls. Examples include locking file cabinets, encrypting digital data, and limiting access through role-based permissions.
6. Consult with Experts
Partnering with industry experts like TrustNet can help you build a tailored compliance program that addresses your unique challenges. Experts can provide valuable insights, assist with risk assessments, and recommend best practices that align with regulations.
HIPAA compliance should feel like a part of your organization’s DNA, something you weave into every process rather than an afterthought.
Regular Audits and Assessments
Compliance isn’t static, and neither are the risks organizations face. That’s why self-audits play a critical role in maintaining an effective compliance program.
– Identify Gaps and Weaknesses
Conducting internal audits allows you to catch irregularities or deficiencies before an official review highlights them. Areas to focus on include data storage, employee access controls, and third-party agreements.
– Reinforce Best Practices
An audit isn’t just about finding flaws; it’s also about ensuring you’re sticking to what’s working. Reinforce processes that align with HIPAA guidelines and explore how to enhance them further.
– Stay Ahead of Changes
Healthcare and data security landscapes evolve all the time. Use audits as an opportunity to evaluate whether your practices align with the latest compliance requirements and technological advancements.
– Document Everything
Keep detailed records of your findings, including corrective measures. Documentation serves as evidence of your commitment to compliance and can be invaluable during external audits or investigations.
Routine self-assessments not only help you maintain compliance but also instill confidence in your team and the patients you serve. Knowing that your organization is actively closing gaps and improving processes creates a culture of accountability and trust.
Resources for Healthcare Provider
With the right tools and resources at your fingertips, you can make the HIPAA compliance process more manageable and effective.
Here are a few key resources to consider:
Official HIPAA Resources
The US Department of Health and Human Services (HHS) website offers free materials, such as guidance documents, FAQs, and summaries of HIPAA regulations. These resources are a great place to start learning about the regulatory environment.
TrustNet’s Unique Offerings
TrustNet understands that every organization’s compliance needs are different. Our customized solutions provide a clear path to meeting HIPAA standards:
–HIPAA/HITECH Policy Reviews and Development
Ensure your policies align with current regulations and best practices by leveraging our comprehensive policy review and development services.
–HIPAA/HITECH Gap Assessment
Identify areas where your compliance efforts fall short. TrustNet’s gap assessments highlight vulnerabilities and offer strategic guidance to address them.
HIPAA/HITECH Risk Assessment
Proactively uncover potential risks to patient data security with our detailed risk evaluation. We will help you understand your exposure and implement measures to reduce it.
–HIPAA/HITECH Controls Assessment
Evaluate the effectiveness of your current security controls. TrustNet provides an in-depth look at your safeguards and recommends adjustments to enhance protection.
–HIPAA/HITECH Compliance Assessment
Get a holistic view of your organization’s compliance status. Our assessments provide actionable insights for maintaining adherence to HIPAA standards.
Additional Resources
For those looking to deepen their knowledge, TrustNet offers a variety of support materials, including:
Blogs and Whitepapers
Explore in-depth articles that explain HIPAA rules, share expert analysis, and offer practical tips for compliance.
Guides for HIPAA Compliance
Access helpful guides that break down complex requirements into manageable steps, helping your team integrate compliance into everyday processes.
With the right mix of tools, templates, and expert guidance, you can confidently address HIPAA requirements while safeguarding the trust of your patients and partners.
Secure Compliance, Build Trust, and Take Action Today
HIPAA is about protecting patient health information. By knowing the rules and taking action, you can reduce risk, avoid fines, and build trust with your patients and partners.
In this guide, we’ve covered the following:
-
- Securing PHI and ePHI at every point — use, share, store
- Common pitfalls to avoid and how to address them effectively
- Practical strategies and tools that make compliance more manageable, including risk assessments, training, and expert guidance
HIPAA compliance is an ongoing process that requires dedication and the right resources. Staying committed not only helps you meet legal standards but also underscores your integrity and professionalism in delivering safe, patient-centered care.
TrustNet’s experienced team is ready to help. Whether you need a gap analysis or a full risk assessment, we’ll provide expert insights tailored to your organization’s needs.
Kickstart your efforts with a comprehensive checklist that covers the basics of HIPAA compliance. Use it to evaluate your current status and identify areas for improvement.
Take the first step and ensure you’re prepared to meet the highest standards of compliance. Contact us today.
Subscribe to the TrustNet Newsletter
actionable cybersecurity strategies, and TrustNet’s cutting-edge solutions.




