SOC 2 Continuous Monitoring: Tools and Techniques

TL;DR
This guide shows how to move beyond point-in-time SOC 2 audits and implement continuous monitoring using GhostWatch. You’ll learn how to automate control validation, centralize evidence, configure risk-based alerts, and integrate compliance into your cloud and DevOps workflows. See how TrustNet helps teams streamline audit readiness, avoid common pitfalls, and scale compliance with confidence.
SOC 2 compliance used to mean scrambling for screenshots, chasing evidence, and preparing for an annual audit. But in today’s fast-moving cloud environments, that playbook is broken.
Infrastructure changes daily. New threats surface hourly. Point-in-time audits can’t keep up.
If your team is still stuck in manual mode, you risk non-compliance and expose your business to avoidable risk and operational drag. The future of SOC 2 isn’t a checklist. It’s a system of automated, always-on monitoring that gives your team real-time visibility and readiness.
That’s exactly what this guide delivers:
A tactical roadmap for implementing continuous SOC 2 monitoring, powered by the right frameworks, the right tools, and the right partner.
Key Components of SOC 2 Continuous Monitoring
SOC 2 continuous monitoring is a proactive, automated approach that demonstrates your controls are working every day, not just once a year. With the right architecture, your team can detect risks early, validate controls continuously, and stay audit-ready without the last-minute scramble.
Here’s what that looks like in action:
— Real-Time Control Validation
Don’t wait for annual check-ins. Use automated checks to confirm that key controls, like MFA enforcement, encryption-at-rest, and incident response workflows, are working as expected. Monitor these controls in real time across all systems.
— Evidence Aggregation
Replace scattered evidence and siloed screenshots with a single source of truth. GhostWatch centralizes logs, configs, policy attestations, and system states into one unified platform, so your compliance data stays complete, current, and accessible.
— Risk-Based Alerting
Not all alerts deserve your time. Prioritize the ones that matter most, like unauthorized access attempts, misconfigurations in production, or disabled security controls. Flag what’s urgent, ignore what’s noise.
— Audit Trails
Every change, every control state, and every exception is tracked and versioned. GhostWatch automatically maintains immutable logs and audit trails, so your auditors see exactly what happened and when, with full context.
These components form the backbone of a sustainable SOC 2 automation strategy, and they’re all built to scale as your environment grows.
Explore how teams like yours are automating evidence collection, tightening control validation, and staying audit-ready.
Book a strategy session with a TrustNet expert to learn how GhostWatch can support your compliance goals
SOC 2 Continuous Monitoring Methodologies
Building a strong SOC 2 monitoring framework requires a system that actively tracks control performance, maps it to Trust Services Criteria (TSCs), and delivers real-time insights your team can act on.
Here’s how to make that happen:
1. Define Monitoring Metrics
Start by mapping each TSC to measurable, verifiable metrics. For example:
-
- Security: MFA enforcement across identity and access management (IAM) systems
- Availability: Uptime SLAs and failover readiness
- Confidentiality: Encryption key rotation schedules
Clear metrics make it easier to validate controls continuously and flag gaps early.
2. Integrate Tooling for Full Visibility
Connect your cloud infrastructure, identity providers, CI/CD pipelines, and SIEM platforms. GhostWatch supports deep integrations and crosswalks across these systems, delivering end-to-end telemetry aligned to your SOC 2 framework.
3. Automate Evidence Collection
Don’t chase screenshots or Slack messages. GhostWatch uses APIs and scheduled tasks to pull real-time data from AWS, Azure, Okta, GitHub, and more. You get current, complete evidence, without interrupting workflows.
4. Configure Alerts That Matter
Set thresholds for deviations that impact your compliance posture. GhostWatch lets you define what triggers an alert and where notifications go, so your team responds fast without drowning in noise.
5. Run Periodic Reviews with Dashboards
Use GhostWatch’s visual dashboards to conduct quarterly control reviews, track progress, and prep for annual audits. These insights make auditor conversations easier and more transparent.
This methodology keeps your monitoring program actionable, automated, and always aligned to SOC 2 expectations.
Essential Tools for SOC 2 Continuous Monitoring
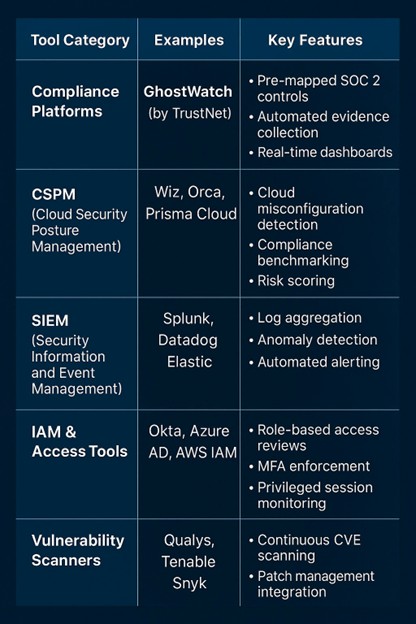
TrustNet’s Differentiator: TrustNet leverages GhostWatch’s advanced automation, control orchestration, and trust management features to help clients streamline compliance, reduce manual work, and maintain a single source of truth for evidence and certifications.
Implementing Continuous Monitoring: Step-by-Step
Here’s how your team can roll out SOC 2 continuous monitoring using GhostWatch as the backbone.
1. Map Controls to Data Sources
Start by aligning the SOC 2 TSCs to real data sources.
Example:
-
- CC6.1: Logical Access → AWS CloudTrail logs
- CC6.6: Change Management → GitHub commit histories
- CC7.1: Incident Response → SIEM event logs
GhostWatch’s integration library connects directly to cloud platforms, identity systems, and code repositories, so your control mappings stay accurate and up to date.
2. Deploy Automation Tools
Use GhostWatch to automatically collect evidence, track control state, and orchestrate compliance workflows across frameworks. Set up scheduled tasks to keep evidence fresh without manual overhead.
3. Build Dashboards for Visibility
Create dashboards to track control health, evidence status, and readiness gaps in real time. GhostWatch makes these dashboards fully customizable, so teams and auditors get the exact views they need.
4. Enable Real-Time Alerts
GhostWatch Managed Compliance Services lets you set alerts for control and task due dates to stay ahead of compliance issues. For real-time security alerts, like unauthorized access or configuration drift, you’ll need GhostWatch Managed Security, which is a separate service from GhostWatch MCS.
5. Integrate with DevOps
Build compliance into your deployment pipelines. GhostWatch connects with CI/CD tools to enforce control checks before releases and syncs evidence automatically, keeping you always audit-ready without slowing down engineering.
This process transforms SOC 2 from a reactive effort into a continuous, automated discipline that’s built to scale.
Case Study: TrustNet & GhostWatch in Action
Open Technology Solutions (OTS), a Credit Union Service Organization and fintech innovator, needed a reliable and scalable path to SOC 2 certification. With a growing client base and heightened regulatory scrutiny, OTS sought to strengthen data security, demonstrate operational integrity, and build stakeholder trust.
To achieve this, OTS partnered with GhostWatch, TrustNet’s managed security and compliance platform.
Overcoming Challenges with GhostWatch
During their SOC 2 journey, OTS faced several roadblocks that added complexity to their compliance process:
-
- Template Limitations: Navigating multiple regulatory standards required access to a broad range of templates.
- Controls Mapping Complexity: Mapping controls across frameworks made it difficult to maintain consistency and completeness.
- Manual Evidence Workflows: Submitting and tracking evidence manually consumed time and introduced the risk of error.
GhostWatch helped OTS overcome these challenges with purpose-built features and expert guidance:
-
- Extensive Template Library: With over 80 framework templates available, OTS aligned faster with relevant industry requirements.
- Comprehensive Controls Mapping: GhostWatch enabled cross-framework mapping and reuse of proofs, helping the team close gaps efficiently.
- Centralized Compliance Management: The platform unified controls, audits, issue tracking, and proof management in one system, eliminating fragmentation.
Results and Benefits
Despite a few areas for improvement in the platform, the outcome was a success, driven by continuous GhostWatch support and collaboration across stakeholders.
OTS achieved:
-
- Improved Security Posture: Rigid controls helped safeguard sensitive financial data.
- Customer Trust: SOC 2 certification reinforced client confidence.
- Operational Efficiency: Centralized systems saved time and reduced manual tasks.
- Regulatory Alignment: OTS now meets key industry compliance standards with confidence.
GhostWatch didn’t just support certification, it enabled a scalable compliance process that strengthened OTS’s reputation and set the stage for future growth.
Common Pitfalls and Mitigations
Without the right strategy, even automated programs can fall short. Here are common pitfalls and how to avoid them:
— Over-Reliance on Automation
Automation accelerates compliance, but it doesn’t replace judgment. Run periodic manual reviews to validate control performance and catch edge cases that GhostWatch may flag.
— Tool Silos
When teams use disconnected tools, data becomes fragmented. GhostWatch solves this with pre-built integrations that pull your compliance evidence into one unified system.
— Alert Fatigue
Too many alerts create noise. GhostWatch lets you tune alerts based on risk thresholds, so your team only sees what actually matters and acts faster when it does.
— Stale Policies
Policies, attestations, and control evidence must stay current. GhostWatch automates these updates and schedules refresh cycles to keep everything audit-ready.
Avoiding these traps ensures your SOC 2 program remains efficient, scalable, and always aligned with evolving compliance demands.
What to Do Next: Automate, Monitor, and Scale SOC 2 with Confidence
SOC 2 continuous monitoring with real-time visibility and automation now defines successful compliance programs. With GhostWatch, your team gains a centralized, scalable solution to manage controls, evidence, and audit readiness without the manual grind.
TrustNet brings the expertise. GhostWatch brings the platform. Together, we help you move faster, reduce risk, and stay ahead of evolving compliance demands.
Schedule a SOC 2 continuous monitoring assessment with TrustNet or request a GhostWatch demo
Subscribe to the TrustNet Newsletter
actionable cybersecurity strategies, and TrustNet’s cutting-edge solutions.



