SOC 2 for Cloud-Native Organizations

TL;DR
SOC 2 compliance is about proving your cloud-native systems are secure, reliable, and built to scale. This guide explains how to scope your environment, assess risks, implement controls, and automate evidence collection across modern stacks. If you’re running on cloud infrastructure, SOC 2 success depends on continuously aligning your DevOps, engineering, and compliance practices.
SOC 2 compliance has evolved into a competitive requirement for SaaS and cloud-native companies looking to close enterprise deals, retain customer trust, and grow in regulated markets.
However, cloud-native systems introduce complexity: shared responsibility, dynamic scaling, API exposure, and infrastructure as code all demand a fresh, technical approach to SOC 2.
This guide is built for engineers, architects, and security leaders who don’t just want to pass the audit; they want to operationalize it. We’ll cover:
-
-
- How SOC 2 Trust Services Criteria map to cloud-native risks
- How to scope systems and data flows across dynamic infrastructure
- How to implement scalable controls using automation and DevOps workflows
- How to prepare for audits without disrupting your engineering velocity
-
If you’re building in the cloud, this guide will help you meet compliance demands while reinforcing a security-first culture that supports scale.
SOC 2 Trust Services Criteria and Cloud-Native Implications
SOC 2 Compliance is built around the five Trust Services Criteria, namely security, availability, processing integrity, confidentiality, and privacy.
Security. Information and systems are protected against unauthorized access, unauthorized disclosure of information, and damage to systems that could compromise the availability, integrity, confidentiality, and privacy of information or systems and affect the entity’s ability to achieve its objectives.
Security refers to the protection of
i. information during its collection or creation, use, processing, transmission, and storage and
ii. systems that use electronic information to process, transmit or transfer, and store information to enable the entity to meet its objectives. Controls over security prevent or detect the breakdown and circumvention of segregation of duties, system failure, incorrect processing, theft or other unauthorized removal of information or system resources, misuse of software, and improper access to or use of, alteration, destruction, or disclosure of information.
Availability. Information and systems are available for operation and use to meet the entity’s objectives.
Processing Integrity. System processing is complete, valid, accurate, timely, and authorized to meet the entity’s objectives.
Confidentiality. Information designated as confidential is protected to meet the entity’s objectives. Confidentiality addresses the entity’s ability to protect information designated as confidential from its collection or creation through its final disposition and removal from the entity’s control in accordance with management’s objectives.
Privacy. Personal information is collected, used, retained, disclosed, and disposed of to meet the entity’s objectives.
The Five Criteria and What They Mean in the Cloud
1. Security (Mandatory)
Protect systems against unauthorized access and abuse.
-
- In cloud-native systems, this means securing APIs, enforcing least privilege IAM, and hardening workloads against common threats like privilege escalation and exposed secrets.
- Misconfigured buckets, permissive roles, and public endpoints often become attack vectors.
2. Availability
Keep your systems and data accessible as promised.
-
- Distributed infrastructure complicates availability. You need resilient architecture, autoscaling, and observability tools that detect degradation fast.
- Cloud regions and services fail, your uptime can’t.
3. Processing Integrity
Ensure systems process data completely, accurately, and in a timely manner.
-
- Microservices, event-driven pipelines, and serverless functions require strict validation, retry logic, and consistent monitoring.
- Missed messages or partial transactions can break guarantees.
4. Confidentiality
Restrict and protect access to sensitive data.
-
- Encrypt data at rest and in transit using managed key services (e.g., KMS).
- Use fine-grained access controls and segment environments to reduce blast radius.
5. Privacy
Collect, use, retain, and disclose personal data in line with your privacy policy.
-
- Map where personal data flows, including third-party services and internal analytics tools.
- Implement data minimization, purpose limitation, and deletion workflows aligned with privacy laws (e.g., GDPR, CCPA).
Why These Criteria Hit Different in the Cloud
Cloud-native environments change fast. Containers spin up and down. Code ships hourly. Third-party tools touch every layer. That velocity demands:
-
- Transparency: You need real-time visibility across every layer, from infrastructure to SaaS tools.
- Operational maturity: Incident response, deployment, and configuration management must be codified and auditable.
- Change control: Automate CI/CD while enforcing approvals, peer reviews, and rollback mechanisms.
SOC 2 is about building a system that proves you can run a secure, reliable infrastructure at scale. And in the cloud, that starts with aligning your architecture to the Trust Services Criteria.
Ready to Make SOC 2 Work for Your Cloud Stack?
At TrustNet, our AICPA-accredited auditors can guide you from risk assessment through to SOC 2 certification
Scoping for Cloud: Systems, Data Flows, and Shared Responsibility
Before you implement controls or gather evidence, you need a clear SOC 2 audit scope. Scoping defines which systems, data, and processes fall under audit, and in cloud-native environments, that surface can expand fast.
— Define What’s in Scope
Your scope should include every system that stores, processes, or transmits customer data. In a modern cloud-native stack, this typically covers:
-
- Compute: EC2 instances, containers, serverless functions (e.g., AWS Lambda, Google Cloud Run)
- Storage: Object stores (e.g., S3, GCS), block storage (e.g., EBS, Persistent Disks), and distributed databases (e.g., DynamoDB, Spanner)
- APIs: Public and internal endpoints that expose functionality or data
- CI/CD Pipelines: Source control, build tools, runners, and deployment workflows
- Third-Party Services: Authentication providers, observability platforms, email services, payment processors
Anything that touches customer data or system availability is in scope, even if it’s abstracted through cloud services.
— Map Data Flows with Architecture Diagrams
You need to visualize how data moves through your systems. Auditors will ask:
-
- Where does customer data enter the system?
- Which components process or store?
- How does it flow between services and environments?
- What controls protect it at each step?
Use architecture diagrams and system maps to show these flows clearly. Label trust boundaries, encryption points, and external integrations.
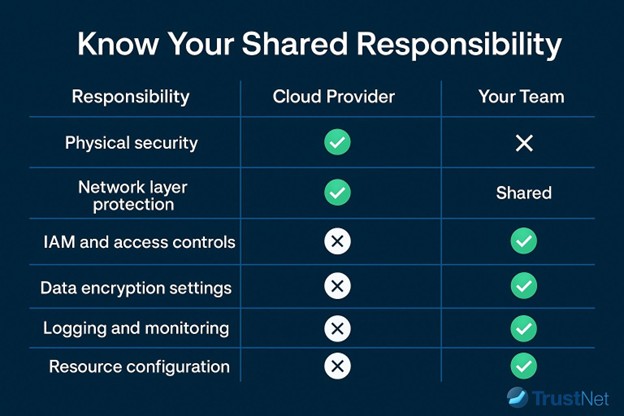
— Know Your Shared Responsibility
Cloud providers secure the infrastructure, but you’re responsible for how you use it. Here’s a simplified breakdown:
— Consider Hybrid and Multi-Cloud Complexities
Multi-cloud and hybrid deployments expand your risk surface. You must:
-
- Standardize logging and alerting across providers
- Unify identity and access controls
- Track data flows across environments
- Document every interdependency clearly
If you miss a system, it won’t just cause audit friction; it might expose a security gap you never meant to create.
Cloud-Specific Risk Assessment and Gap Analysis
Cloud-native systems introduce unique security risks, and SOC 2 expects you to identify and mitigate them before your audit begins. You need a risk assessment process that keeps up with dynamic environments, not static checklists.
Key Risks in Cloud Environments
Start by identifying common high-impact vulnerabilities:
-
- Misconfigurations: Public S3 buckets, permissive security groups, unencrypted storage
- Excessive IAM permissions: Over-provisioned roles, stale credentials, lack of least privilege
- Lack of centralized logging: Missing CloudTrail, Kubernetes audit logs, or API logs
- Insecure APIs: Unauthenticated endpoints, weak rate limiting, inconsistent input validation
These aren’t theoretical. According to recent reports, privilege misuse and configuration errors are critical risk factors across modern infrastructure.
Use GhostWatch for Automated Gap Detection
Manual risk assessments fall short in fast-moving environments. GhostWatch by TrustNet helps you stay audit-ready with built-in compliance intelligence:
-
- Assigns a dedicated compliance manager for hands-on support and expert guidance
- Runs a comprehensive readiness assessment to identify gaps across your stack
- Generates a remediation roadmap tailored to your infrastructure and risk profile
- Provides customized policies and procedures aligned with SOC 2 trust criteria
- Facilitates the full SOC 2 audit process, including pre-certification and auditor engagement
- Delivers executive-level reporting and year-round compliance monitoring
- Operates through a streamlined platform that organizes, automates, and tracks every task
GhostWatch turns your assessment from a one-off audit prep exercise into a continuous, managed compliance process. Learn more here.
Prioritize Based on Impact and Likelihood
Once you’ve identified your risks, don’t treat them equally. Classify each risk by:
- Impact: What happens if this control fails?
- Likelihood: How often does this failure mode occur in your environment?
Use this to build a remediation plan that focuses on engineering time where it matters most and shows auditors that your risk management approach is both proactive and evidence based.
Implementing SOC 2 Controls in Cloud-Native Architectures
Designing SOC 2 controls for cloud-native systems means building security into the way your platform operates, not bolting it on after the fact. You’ll need to align security practices with automation, scalability, and modern deployment models.
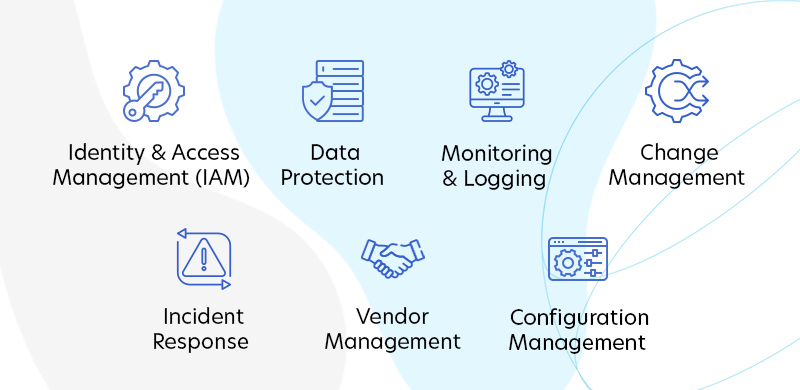
Identity & Access Management (IAM)
-
- Enforce least privilege across all accounts and services, use roles, not root.
- Require Multi-Factor Authentication (MFA) and Single Sign-On (SSO) for all users with privileged access.
- Set up automated access reviews on a quarterly basis and remove stale permissions.
Data Protection
-
- Encrypt data at rest using native cloud tools (e.g., AWS KMS, GCP CMEK).
- Encrypt data in transit with TLS 1.2+ across APIs, internal services, and third-party integrations.
- Define data retention policies and enforce secure deletion for expired or terminated datasets.
Monitoring & Logging
-
- Centralize logs with tools like AWS CloudTrail, Datadog, or SIEM.
- Enable real-time alerting for unusual authentication events, privilege escalations, and configuration changes.
- Retain logs per policy, typically 1–2 years for audit trail and incident forensics.
Change Management
-
- Automate CI/CD workflows with approval gates and peer-reviewed pull requests.
- Maintain version control for all code, infrastructure-as-code (IaC) templates, and pipeline configurations.
- Log and document every production change, including hotfixes.
Incident Response
-
- Build an incident response plan that addresses real-world cloud threats (e.g., unauthorized access and data exfiltration).
- Run tabletop exercises and automate alert escalation.
- Maintain and update playbooks for your most likely scenarios.
Vendor Management
-
- Track all third-party vendors that process or store customer data.
- Review their SOC 2, ISO 27001, or equivalent reports regularly.
- Maintain contracts and security assessments for each vendor in scope.
Configuration Management
-
- Define infrastructure as code using Terraform, Pulumi, or CloudFormation.
- Scan environments continuously for misconfigurations using tools like GhostWatch.
- Block insecure deployments at the CI/CD layer.
SOC 2 is about operationalizing these controls in a way that keeps up with your engineering velocity.
Training Teams and Building a Security-First Culture
If your engineers, DevOps, and support teams don’t understand their role in protecting systems and data, SOC 2 controls can break down fast.
Train with Purpose
- Educate teams on SOC 2 Trust Services Criteria (TSC), especially Security and Availability.
- Explain why controls exist. Don’t just push policies. Show how they prevent real-world risks.
- Use real scenarios from your cloud environment (e.g., misconfigured IAM roles, open ports, exposed credentials).
Clarify the Shared Responsibility Model
- Engineering secures the application layer by handling secure coding practices, secrets management, and application-level logging.
- DevOps manages the cloud environment by defining IAM policies, running CI/CD pipelines, and enforcing configuration standards through infrastructure as code.
- Support interacts directly with sensitive customer data, so they require access controls, authentication training, and clearly defined boundaries for data handling.
Everyone needs to understand what the cloud provider covers and what it doesn’t” to “what you are responsible for. That clarity builds accountability and keeps controls aligned with how the systems actually operate.
Make Security a Daily Habit
- Review access regularly.
- Run security drills.
- Add security checks to every pull request and pipeline.
Preparing for the SOC 2 Audit: Evidence, Execution, and Maintenance
Preparation is everything when it comes to SOC 2.
Collect Evidence That Auditors Trust
Start gathering the artifacts your auditor will request. At a minimum, that includes:
- Security policies and standard operating procedures
- System configurations across infrastructure and applications
- Access reviews and IAM change logs
- Monitoring and alerting records
- Incident response reports and escalation logs
Make sure this evidence aligns with the Trust Services Criteria and covers the entire audit period (especially for Type II).
Choose the Right Auditor
Not all firms understand cloud-native systems. Choose an AICPA-accredited auditor with real cloud experience. Experts like TrustNet specialize in dynamic environments and know how to evaluate DevOps workflows, automated deployments, and IaC.
Don’t Stop After the Report
SOC 2 isn’t a one-time event. To stay compliant:
- Monitor your controls in real time
- Conduct quarterly internal reviews
- Plan for annual recertification
Let Automation Do the Heavy Lifting
Manual evidence collection won’t scale. Use a platform like GhostWatch by TrustNet to:
- Automate control, tracking, and evidence gathering
- Keep audit readiness always on
- Maintain visibility through clean, executive-level dashboards
Automation turns SOC 2 from a once-a-year fire drill into a sustainable, repeatable process.
Common Pitfalls and How to Avoid Them
Avoid these common mistakes to stay audit-ready and secure.
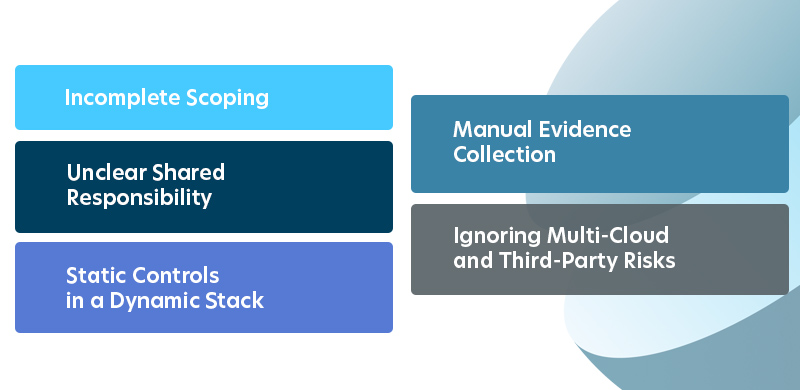
Incomplete Scoping
Teams often overlook APIs, CI/CD systems, or third-party tools that process sensitive data. Scope everything that touches customer data, not just production apps.
Fix it: Build a full architecture map. Include authentication systems, monitoring tools, and background jobs.
Unclear Shared Responsibility
Teams sometimes assume the cloud provider handles things like encryption or logging. That’s a mistake.
Fix it: Define ownership clearly between the provider and your teams, especially for IAM, logging, and configuration management.
Manual Evidence Collection
Relying on spreadsheets and screenshots is time-consuming and lacks the context auditors need.
Fix it: Automate evidence gathering using platforms like GhostWatch. Tie evidence to controls and update it continuously.
Ignoring Multi-Cloud and Third-Party Risks
Vendor sprawl and multi-cloud complexity introduce blind spots.
Fix it: Review third-party access, assess vendor controls, and unify logging across environments.
Static Controls in a Dynamic Stack
Cloud environments evolve rapidly. If your controls don’t keep up, security gaps will emerge.
Fix it: Treat compliance as an ongoing process. Schedule quarterly reviews and monitor controls in real time.
What to Do Next: Turn SOC 2 from a One-Time Sprint into a Cloud-Ready Practice
SOC 2 compliance in the cloud is all about building systems and teams that are secure by design. Cloud-native organizations face unique challenges: shared responsibility, ever-changing infrastructure, and the speed of continuous delivery. But those challenges also create an opportunity to operationalize compliance.
When you embed automation, real-time monitoring, and a security-first culture into your workflows, SOC 2 becomes sustainable, not a fire drill.
Ready to take the next step? Assess your cloud SOC 2 readiness or schedule a demo of GhostWatch by TrustNet.
Subscribe to the TrustNet Newsletter
actionable cybersecurity strategies, and TrustNet’s cutting-edge solutions.




