Blog Types of Threats and Vulnerabilities in Cyber Security
Types of Threats and Vulnerabilities in Cyber Security

As the recent epidemic of data breaches illustrates, no system is immune to attacks. Any company that manages, transmits, stores, or handles data must institute and enforce mechanisms to monitor
It’s essential to distinguish between cyber threats and vulnerabilities before identifying specific risks to modern data systems.
Cyber threats are security incidents or circumstances that can negatively affect your network or other data management systems. Examples of common security threats include phishing attacks leading to malware infection, a staff member’s failure to follow data protection protocols causing a data breach, or even natural disasters that disrupt your company’s data headquarters.
Examples of common security threats include phishing attacks that result in installing malware that infects your data, a staff member’s failure to follow data protection protocols that causes a data breach, or even nature’s forces that take down your company’s data headquarters, disrupting access.
Vulnerabilities are the gaps or weaknesses in a system that make threats possible and tempt threat actors to exploit them. Types of vulnerabilities in network security include, but aren’t
When threat probability is multiplied by the potential loss that may result, cybersecurity experts refer to this as a risk.
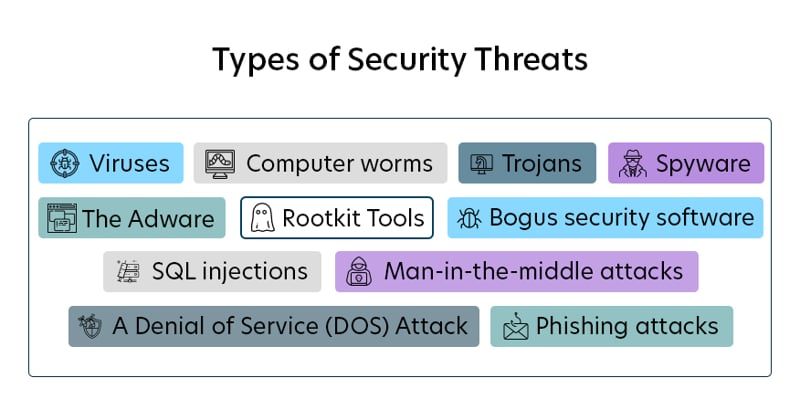
Types of Security Threats
In the same way that bacteria and illnesses can invade one’s body, various threats can harm hardware and software systems. Some of the major ones include the following:
-
- Viruses are designed to be easily transmitted from one computer or system to another. Often sent as email attachments, viruses corrupt and co-opt data, interfere with your security settings, generate spam, and may even delete content.
- Computer worms are similar; they spread from one computer to the next by sending themselves to all of the user’s contacts and subsequently to all contacts’ contacts.
- Trojans are malicious pieces of software that insert themselves into a legitimate program. Often, people voluntarily let trojans into their systems in email messages from a person or an advertiser they trust. Your system becomes vulnerable to malware when the accompanying attachment is open.
- Bogus security software that tricks users into believing that their system has been infected with a virus. The accompanying security software the threat actor provides to fix the problem causes it.
- Adware tracks your browsing habits and causes particular advertisements to pop up. Although this is common and often something you may even agree to, adware is sometimes imposed upon you without your consent.
- Spyware is an intrusion that may steal sensitive data such as passwords and credit card numbers from your internal systems.
- A Denial of Service (DOS) attack occurs when hackers deluge a website with traffic, making it impossible to access its content. A distributed denial of service (DDOS) attack is more forceful and aggressive since it is initiated from several servers simultaneously. As a result, it is harder to mount defenses against it.
- Phishing attacks are social engineering infiltrations whose goal is to obtain sensitive data, such as passwords and credit card numbers, incorrectly. The hacker downloads and installs malware via emails or links from trusted companies and financial institutions.
- SQL injections are network threats that involve using malicious code to infiltrate cyber vulnerabilities in data systems. As a result, data can be stolen, changed, or destroyed.
- Man-in-the-middle attacks entail a scenario where the communication of two private entities is intercepted and manipulated by a third party. While it is limited to listening, the attacker can also manipulate or alter the information, creating false information and even security risks.
- Rootkits are tools that allow remote and illegitimate access to computer systems. They can also abuse system resources by introducing malicious software and compromising passwords or other data.
For more on our Penetration Testing services, Click Here
Understanding Network Vulnerabilities
Protecting your network systems has become essential in today’s modern business landscape. A simple mistake can cause the most severe disruptions.
Key Vulnerabilities to Watch Out For:
-
- Outdated Applications: Failing to update, test, and patch applications can expose your network to risks like code injection and cross-site scripting.
- Security Gaps: Insecure direct object references and similar vulnerabilities open your systems to potential breaches.
Why It Matters
If these vulnerabilities are not addressed quickly enough, you compromise not only your data but also the integrity of your entire business. Customer trust and business operations will also be at risk without appropriate security precautions.
Make these steps a top priority to protect your network from possible attacks and guarantee a safe online environment.
Take the first step towards building a cyber-resilient organization by prioritizing regular penetration testing with TrustNet.
Contact our Experts today.