
Jan 30, 2024 | Blog, Managed Security
Blog GhostWatch Managed Security: Vigilance Redefined GhostWatch Managed Security: Vigilance Redefined With the world become more linked, there is an exponential increase in the demand for strong security measures to defend against more sophisticated cyber attacks....

Jan 25, 2024 | Blog, Managed Security
Blog 24/7 Monitoring with GhostWatch: What It Means for Your Business 24/7 Monitoring with GhostWatch: What It Means for Your Business For businesses of all sizes, ensuring 24-hour security has become essential. In order to prevent risks from becoming serious...

Jan 25, 2024 | Blog, Managed Security
Blog New Solutions in Cybersecurity: Navigating the Surge of AI-Assisted Threats in 2024 New Solutions in Cybersecurity: Navigating the Surge of AI-Assisted Threats in 2024 The cybersecurity landscape in 2024 is expected to be increasingly complex and multifaceted....
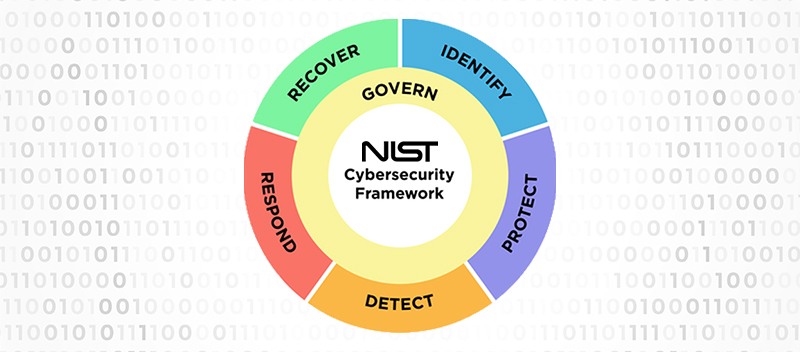
Jan 23, 2024 | Blog, Managed Security
Blog NIST CSF 2.0: What’s New NIST CSF 2.0: What’s New Established in 2014, the National Institute of Standards and Technology Cybersecurity Framework (NIST CSF) is a vital tool in the field of cybersecurity. The framework’s effectiveness in addressing these...

Jan 16, 2024 | Blog, Compliance, Information Security, Managed Security, Network Security
Blog Launching a Safer Future: Meet GhostWatch and iTrust from TrustNet Launching a Safer Future: Meet GhostWatch and iTrust from TrustNet TrustNet is a cybersecurity and compliance industry leader renowned for innovative and robust solutions. We are dedicated to...

Jan 10, 2024 | Blog, Managed Security
Blog The Dual Power of GhostWatch: Security and Compliance Unveiled The Dual Power of GhostWatch: Security and Compliance Unveiled With the rise in cyber threats and the growing sophistication of hackers and cybercriminals, businesses globally are realizing the...

Jan 10, 2024 | Blog, Compliance, Information Security, Managed Security, Network Security
Blog Coming Soon: Exciting New Solutions from TrustNet in 2024 Coming Soon: Exciting New Solutions from TrustNet in 2024 As we usher in a new year, TrustNet continues its unwavering commitment to innovation in cybersecurity. With an established track record of...

Jan 2, 2024 | Blog, Compliance, Managed Security
Blog 5 Key Takeaways from the 2023-2024 CISA Roadmap for Artificial Intelligence 5 Key Takeaways from the 2023-2024 CISA Roadmap for Artificial Intelligence The “2023–2024 CISA Roadmap for Artificial Intelligence” is a strategic guide outlining the...

Jan 2, 2024 | Blog, Compliance, Information Security, Managed Security, Network Security, Penetration Testing
Blog TrustNet’s 2023 Journey: Celebrating Our Growth and Successes in Cybersecurity TrustNet’s 2023 Journey: Celebrating Our Growth and Successes in Cybersecurity In 2023, TrustNet marked an impressive year of growth and success in the dynamic field of cybersecurity....

Dec 28, 2023 | Blog, Compliance, Managed Security
Blog Overcoming Cyber Threats: How Businesses Triumphed in 2023 Overcoming Cyber Threats: How Businesses Triumphed in 2023 The cybersecurity landscape of 2023 was a battleground, constantly shifting and evolving. Businesses rallied, adapted, and overcame challenges...

Dec 26, 2023 | Blog, Managed Security
Blog Planning for 2024: Leveraging a Managed Security Platform for Business Growth Planning for 2024: Leveraging a Managed Security Platform for Business Growth As we enter 2024, businesses are increasingly pivoting towards a digital-first approach. While offering...

Dec 20, 2023 | Blog, Compliance, Information Security, Managed Security, Network Security
Blog Educational Institutions Also Need To Pay Attention To Cybersecurity, Here’s Why Educational Institutions Also Need To Pay Attention To Cybersecurity, Here’s Why The Education Cybersecurity Summit 2023 took place in New York City on December 8, 2023. This event...

















