
24/7 Monitoring with GhostWatch: What It Means for Your Business
Blog For businesses of all sizes, ensuring 24-hour security has become essential. In order to prevent risks from becoming serious problems, businesses must actively identify and manage them via ongoing monitoring. This goes beyond simple precautionary...

New Solutions in Cybersecurity: Navigating the Surge of AI-Assisted Threats in 2024
Blog The cybersecurity landscape in 2024 is expected to be increasingly complex and multifaceted. With the advancement of technology, cyber threats are also evolving, becoming more sophisticated and more challenging to detect. Businesses and individuals now...
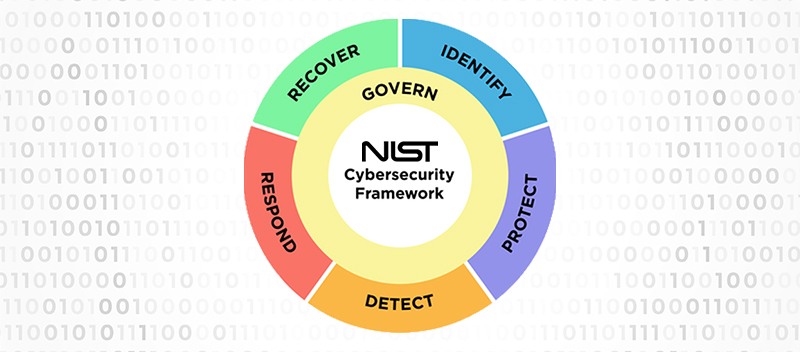
NIST CSF 2.0: What’s New
Blog Established in 2014, the National Institute of Standards and Technology Cybersecurity Framework (NIST CSF) is a vital tool in the field of cybersecurity. The framework's effectiveness in addressing these risks is well recognized, with many organizations...

Launching a Safer Future: Meet GhostWatch and iTrust from TrustNet
Blog TrustNet is a cybersecurity and compliance industry leader renowned for innovative and robust solutions. We are dedicated to safeguarding digital ecosystems against the evolving threats of today. With an ever-increasing reliance on technology, TrustNet...

The Dual Power of GhostWatch: Security and Compliance Unveiled
Blog With the rise in cyber threats and the growing sophistication of hackers and cybercriminals, businesses globally are realizing the critical need to protect their systems and data. Not only is this vital for security, but it's also a crucial aspect of...

Coming Soon: Exciting New Solutions from TrustNet in 2024
Blog As we usher in a new year, TrustNet continues its unwavering commitment to innovation in cybersecurity. With an established track record of providing robust and reliable solutions, we are launching a series of transformative offerings in 2024 that will...

TrustNet’s Comprehensive Guide to Achieving SOC 2 Compliance
Blog With the increasing prevalence of cyber threats and stringent regulatory requirements, achieving and maintaining compliance with data security standards has become a top priority for businesses worldwide. One such standard that holds immense...

5 Key Takeaways from the 2023-2024 CISA Roadmap for Artificial Intelligence
Blog The "2023–2024 CISA Roadmap for Artificial Intelligence" is a strategic guide outlining the Cybersecurity and Infrastructure Security Agency's (CISA) approach towards AI and its role in cybersecurity. The roadmap, in alignment with the...

TrustNet’s 2023 Journey: Celebrating Our Growth and Successes in Cybersecurity
Blog In 2023, TrustNet marked an impressive year of growth and success in the dynamic field of cybersecurity. This year's milestones are a testament to our unwavering commitment to excellence as we navigated complex security landscapes, innovated, and...

A Year in Review: TrustNet’s Success Stories in Cybersecurity in 2023
Blog Throughout 2023, TrustNet has stood at the forefront of cybersecurity. We continue to garner notable achievements and provide key takeaways from industry-leading events such as CyberDefenseCon 2023 and the RSA Conference 2023. We actively contributed...




