Managed Security
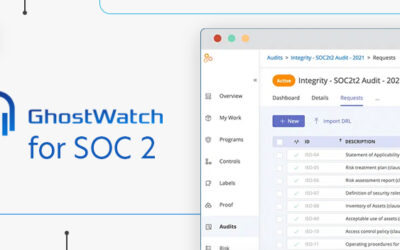
Expert articlesHow GhostWatch Elevates SOC 2 Compliance
Blog GhostWatch by TrustNet is a global leader in security and compliance management. We are excited to delve into the benefits of...
2024’s Cyber Guardians: The Forefront Companies Shaping Cybersecurity Solutions
Blog Security solutions that are proactive and adaptable are more important than ever as cyber criminals grow more skilled. On the...
CSIRT Cyber Security: How to Build an Incident Response Team
Blog Network systems and data security are crucial for businesses of any size. While deploying firewalls and other protective measures is...
Managed Security Unveiled: The Ultimate Providers Powering Cyber Defense
Blog Cyber threats loom larger and more sophisticated, and robust cybersecurity measures are more critical than ever. Managed security...
Retail’s Digital Shield: Proven Strategies for Superior Cyber Security
Blog Digital transformation is revolutionizing the retail industry. However, the specter of cyber threats looms larger than ever. With the...
Cyber Security Threat Vectors: A Comprehensive Guide on Attack Pathways and Prevention Measures
Blog Cyber security threat vectors are the pathways or methods through which malicious actors gain unauthorized access to systems,...
Cyber Security Posture in 2024: All You Need to Know
Blog Cyber security posture refers to an organization's overall defensive stance against cyber threats, encompassing its policies,...
Blue Team vs. Red Team Cybersecurity: A Comparative Study of Defensive and Offensive Strategies
Blog Blue Team and Red Team operations represent the dual facets of cybersecurity practices aimed at fortifying an organization's...
Navigating the Complex World of Cyber Security Audit and Compliance
Blog As organizations increasingly rely on digital technologies to conduct their operations, safeguarding sensitive information and...
Compliance Without Complications: GhostWatch’s Managed Compliance Solutions
Blog Compliance in cybersecurity presents a myriad of challenges for businesses. The landscape constantly evolves, with new threats and...
Your Compliance, Our Commitment: Introducing GhostWatch Managed Compliance
Blog In today’s ever-changing technology landscape, companies face dynamic laws and regulations that they must adhere to, often with...
GhostWatch Managed Security: Vigilance Redefined
Blog With the world become more linked, there is an exponential increase in the demand for strong security measures to defend against more...
24/7 Monitoring with GhostWatch: What It Means for Your Business
Blog For businesses of all sizes, ensuring 24-hour security has become essential. In order to prevent risks from becoming serious...
New Solutions in Cybersecurity: Navigating the Surge of AI-Assisted Threats in 2024
Blog The cybersecurity landscape in 2024 is expected to be increasingly complex and multifaceted. With the advancement of technology,...
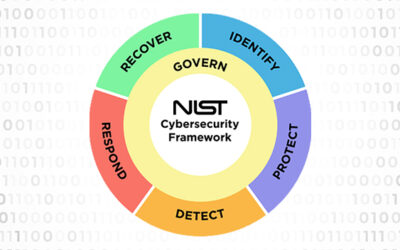
NIST CSF 2.0: What’s New
Blog Established in 2014, the National Institute of Standards and Technology Cybersecurity Framework (NIST CSF) is a vital tool in the...
The Dual Power of GhostWatch: Security and Compliance Unveiled
Blog With the rise in cyber threats and the growing sophistication of hackers and cybercriminals, businesses globally are realizing the...
5 Key Takeaways from the 2023-2024 CISA Roadmap for Artificial Intelligence
Blog The "2023–2024 CISA Roadmap for Artificial Intelligence" is a strategic guide outlining the Cybersecurity and Infrastructure Security...
Overcoming Cyber Threats: How Businesses Triumphed in 2023
Blog The cybersecurity landscape of 2023 was a battleground, constantly shifting and evolving. Businesses rallied, adapted, and overcame...
Planning for 2024: Leveraging a Managed Security Platform for Business Growth
Blog As we enter 2024, businesses are increasingly pivoting towards a digital-first approach. While offering numerous opportunities for...
Looking Back: Key Cybersecurity Lessons from 2023
Blog As we bid farewell to 2023, it's clear that the year has been a formative one in the realm of cybersecurity. The landscape has never...
Enhancing Security through Adaptive Multi-Factor Authentication: A TrustNet Perspective
Blog In the ever-evolving landscape of cybersecurity, the need for robust authentication mechanisms has become paramount. Traditional...
The Growing Threat of Phishing Attacks: Preparing for 2024
Blog As we move forward into the future, the threat of cyber attacks looms more prominent than ever. Among these, phishing attacks are a...
Peering into the Future: TrustNet’s Vision for Cybersecurity in 2024
Blog TrustNet, a leading global provider of cybersecur services span managed security, consultingity and compliance services since 2003....
The Rise of AI in Cybersecurity: Expected Developments in 2024
Blog Artificial Intelligence (AI) has become an instrumental tool in cybersecurity. As we stand at the tail end of 2023, AI has already...
Predicting the Future: Top Cybersecurity Trends for 2024
Blog Key Takeaways This article provides valuable insights for cybersecurity professionals, IT decision-makers, business executives, and...
Cybersecurity in Accounting: The Shield for Client Data
Blog As custodians of sensitive financial information, accounting firms increasingly find themselves in the crosshairs of cybercriminals....
TrustNet: Your Ally in Achieving Cybersecurity Compliance
Blog In an era where digital threats are ever-evolving, TrustNet emerges as a trusted partner committed to fortifying your cybersecurity...
How Does Open Source Data Change The Cyberdefense Game (Open Source Data Summit 2023)
Blog The Open Source Data Summit 2023 was a live virtual summit held on November 15th, 2023. This premier event united open-source...
Cybersecurity and Business Reputation: An Indivisible Duo
Blog In today’s highly digitized business landscape, the strength and effectiveness of a company's cybersecurity measures can...
Year-round Monitoring and Tracking: Key to Effective Cybersecurity
Blog Cybercrime happens round-the-clock. So should cybersecurity. Year-round monitoring and tracking enables organizations to proactively...
The Power of Global Community in Threat Research and Security Innovation
Blog Cybercrime is a global problem that requires a global response. No organization or country — however powerful — can face the...
TrustNet team attends RSA Conference 2023: Our Impression and Thoughts
TrustNet team attends RSA Conference 2023 to stay ahead of cybersecurity, receive awards, and decipher Frisco’s charms Every year since 1991, IT...
Log4j Attack Surface Remains Massive
Four months ago, the remote code execution hole exposed in the Apache Log4j logging tool still had a wide range of potential victims. Using the...
Most Email Security Approaches Fail to Block Common Threats
Blog On a scale of one to ten, where ten is the maximum effectiveness, most security teams give their email security systems a rating of...
Former Uber Chief Security Officer To Face Wire Fraud Charges because of Failed Cybersecurity
Over the past few years, the road has not been smooth for former Uber Chief Security Officer Joseph Sullivan. On December 21, 2021, three additional...
Top Managed Security Services Company 2021
Even after more than a year into the pandemic, the business world is still struggling to address the cybersecurity challenges that it has...
Virtual CISO: All You Need to Know
Security and protection from external threats have become even more important than ever. The growing number of cyberattacks indicates that even...
Cybersecurity Consulting Services
Blog What is Network Penetration Testing? Network Penetration Testing is a type of service performed by a penetration testing network. It...
SIEM Log Management and Managed SIEM Service
TrustNet Managed SIEM Detecting intrusions and other abnormal security events that impact your networks is the function of a group of integrated...
Cybersecurity Monitoring Service
TrustNet Cyber Security Monitoring Services Shielding your customers' sensitive data and the network ecosystems where it resides must be one of your...
Red vs. Blue Team Security
Blog Hackers and other cybercriminals are pulling out all the stops, mounting a stunning array of increasingly sophisticated attacks on...
Vulnerability Management Program
Today’s multi-layered information systems make it possible for companies like yours to store, manage, and transmit data like never before. However,...
Next Generation Endpoint Security
Storing, transmitting, and managing data is one of the primary support tasks that many organizations perform in today’s digital corporate landscape....
SOC for Cybersecurity
Blog Managing customer data and exchanging digital information on a global level provides your organization with both unparalleled...
Compliance vs Security
An organization must constantly be on guard against external network attacks, threats from its own staff and third-party vendors and even fatal...
Qualitative vs. Quantitative Risk Assessments in Cybersecurity
Blog Assessing the risks within your cybersecurity system is one of the key priorities to address when conducting an ISO 27001 project or...
Cyber Threat Hunting
Your company’s network is a complex environment managed by many moving parts. That makes detecting intruders a constant challenge. The truth is that...
Security Patch Management Best Practices
One indisputable fact about today’s software and firmware is that change is inevitable. When vulnerabilities or bugs are discovered or an upgrade is...
Data Security Strategy
When you are on the front lines charged with the critical duty of ensuring that your company’s information and systems are as protected as possible...
Information Security Audit Checklist
Blog Having a robust cybersecurity infrastructure isn't just a luxury—it's a necessity. Because cyber risks are ever-changing, it takes...
FFIEC Cybersecurity Assessment Tool
The Federal Financial Institutions Examination Council (FFIEC) is a governmental body made up of five banking regulators. Its objective is to...
Red Flags Rule Compliance Tips
Identity theft takes a massive toll on millions of Americans each year. It also has a devastating financial effect on the merchants and credit...
Massachusetts Data Security Laws
Regardless of where you do business in the United States, you already know that the security of your stored and transmitted private data is of...
Artificial Intelligence in Cyber security
Blog Without artificial intelligence (AI), we would not have speech recognition technology such as Siri, search engines like Google or...
AWS Penetration Testing
Blog Amazon Web Services (AWS) platform supports a wide variety of business activities that include data storage, web application...
Information Security Program
Any management or human resource professional knows that standards and practices can never be truly implemented and enforced unless and until they...
Security Maturity Model
There are two complementary objectives of any cybersecurity operation. Tools both automated and human must be in place to monitor network systems,...
Azure Penetration Testing
Blog Are you worried about the safety of your data in the cloud? Azure penetration testing is vital to securing apps on this giant...
Data Center Security Best Practices
Organizations use physical data centers to house their data and critical applications. Modern data centers employ a virtualized infrastructure that...
Benefits of Information Security
Protecting the privacy, confidentiality, availability and integrity of your sensitive data is critical. While it is all too easy to let your...
What is an MSSP
Blog One of the most daunting challenges facing today’s businesses is protecting the security of the data they possess. For many,...
IT Cost Reduction Strategies
Few modern businesses would be able to function without information technology. While eliminating it is neither practical nor desirable, there are...
System Hardening Best Practices
Blog Threat actors are constantly using increasingly sophisticated tools and techniques to take advantage of any weaknesses or loopholes...
TrustNet named Top 10 Managed Security Service Providers
“Threat intelligence is an integral facet of our offering as it provides the context, methods, indicators, and impact assessment on existing and...
Insider Threats
When you think about your company’s digital protection strategy, the first threats that come to mind might involve those stemming from external...
Cyber Incident Response Plan and Process
Putting procedures in place to monitor for and detect threats is a critical component of any organization’s security infrastructure. However, these...
TTP Cyber Security
Blog The methods and strategies that criminals use when planning and executing an attack on a company's network and the data it stores are...
Important Cyber Security Metrics to Track
Blog When it comes to protecting the safety and integrity of your physical infrastructure and the digital data your company stores, you...
Cybersecurity Risk Analysis
Blog Keeping up with cybersecurity is more crucial than ever in the modern digital environment. Businesses must take preventative measures...
Cybersecurity Strategy
In today’s business world, the innovations of bad actors are constantly evolving as they devise new ways to breach defenses, and the potential for...
Vulnerability Assessment Methodology
Blog Criminals prowl on the perimeter of your network, seeking weaknesses in your systems and networks that will make illegal entry...
Cybersecurity vs Information Security
It is easy to become lost in a sea of terms when it comes to protecting your company’s data. A particularly relevant case in point is cybersecurity...
Cost of Data Breach
No two words inspire a deeper feeling of dread in CEOs and CFOs than “data breach.” Most executives are queasily familiar with the glaring news...
Attack Vectors in Cybersecurity
Blog Think of hackers and other cyber criminals as a hoard of barbarians doing all they can to bypass even the most robust of your network...
What is a Cyber Security Posture
Blog Security is not simply a firewall or set of user authentication policies that cover small parts of your organization. In fact, you...
Man-in-the-middle Attacks
Many threats lurk right outside your network just waiting to exploit even the tiniest weakness or vulnerability. Of all of them, the man in the...
Cybersecurity Compliance Audit Best Practices
Blog No longer is a cyber attack a rare phenomenon in the world we live in. Nowadays, there is a very good chance that one will affect...
How to Build an Incident Response Team
Blog Since safeguarding the integrity of your network and other systems is of paramount importance to companies of all sizes, you have...
5 Tips to Consider when Developing a Security Awareness Training Program
How to set up your security awareness training program to better protect your company
Five Reasons to Embrace a MSSP
Today’s rapidly evolving technology landscape demands responsive security
The FUD Factor
Recently I had the opportunity to lead a panel at the Global CISO Forum in Atlanta, GA. Our panel topic was a discussion on how to avoid FUD in...