Managed Security
Expert articlesData Breach: Prevent Unauthorized Access & Data Exfiltration
A data breach occurs when unauthorized individuals gain access to sensitive or confidential information. This may include personal identifiers, such...
Cybersecurity Awareness: Training to Prevent Human Error
TL;DR Human error caused 95% of breaches in 2024. Cybersecurity awareness training teaches employees to recognize threats, reduce risky behaviors,...
The Role of Managed Detection and Response (MDR) in Modern Cybersecurity
TL;DR Cyber threats are becoming faster, more targeted, and sophisticated, outpacing traditional security tools. Managed Detection and Response...
TrustNet’s Comprehensive Cybersecurity Solutions: A Deep Dive
TL;DR TrustNet offers comprehensive, end-to-end cybersecurity solutions designed for modern businesses facing complex threats and compliance...
Comparative Guide: TrustNet vs Other Cybersecurity Providers
TL;DR TrustNet delivers enterprise-grade cybersecurity through a unified approach that blends managed security, automated compliance, and advanced...
Cybersecurity Trends to Watch: Insights from RSAC 2025
RSAC 2025 highlighted the key cybersecurity trends for 2025: AI’s critical role in both defense and attack, the rise of identity management and Zero...
How TrustNet Automates Compliance & Security for Enterprises: Reduce Risk & Cost
TrustNet helps enterprises reduce risks and costs with automated compliance and security solutions. Our GhostWatch platform streamlines compliance...
RSA 2025: Industry Trends Business Leaders Are Watching Out For
The RSA Conference 2025, set for April 28 to May 1 in San Francisco, is poised to tackle the pressing challenges shaping the future of...
Social Engineering Tactics & Prevention
Social engineering is one of the most cunning forms of cybersecurity manipulation. Instead of targeting systems or software vulnerabilities, it...
Trust as a Competitive Advantage: How TrustNet’s TaaS Model Strengthens Compliance & Security
TL;DR Modern businesses face mounting cybersecurity threats, complex regulations, and the constant risk of data breaches, which can compromise...
Strategies to Enhance Your Security Against AI-Driven Cyber Threats
As we progress into Q2 of 2025, Artificial Intelligence (AI) continues to reshape industries, driving innovation and efficiency. However, this rapid...
Trust as a Competitive Advantage: How TrustNet’s TaaS Model Strengthens Compliance & Security
TL;DR Modern businesses face mounting cybersecurity threats, complex regulations, and the constant risk of data breaches, which can compromise...
Building Continuous Security Monitoring: A Framework for IT and Security Leaders
TL;DR Continuous Security Monitoring (CSM) is essential for detecting threats, enhancing compliance, and safeguarding critical systems in...
Managed Security: Enhancing Your Cybersecurity Posture
Cyberattacks are becoming increasingly sophisticated, leaving businesses with constantly evolving threats to their sensitive data. For IT managers,...
Incident Response: Mitigating Cybersecurity Breaches
Incident response is all about being ready for the unexpected. Security breaches can happen to any organization, and having a solid plan makes all...
2025 Cybersecurity Blueprint: Advanced Monitoring, Rapid Response, and Threat Mitigation
Advanced security monitoring, rapid incident response, and addressing emerging threats are key to defending against today’s dynamic landscape....
The Top 5 Cybersecurity Threats to Watch Out for in 2025 (Emerging Threats & Solutions)
As technology advances, so do cybercriminals' tactics, resulting in increasingly complex vulnerabilities. The cybersecurity threats in 2025 are not...
SIEM Explained: Cybersecurity Monitoring & Threat Detection
SIEM, or Security Incident and Event Management, isn’t just another technical jargon; it’s a crucial tool for modern cybersecurity. At its simplest,...
Continuous Compliance Monitoring: The Foundation of Strong Security Systems
Today, organizations are under immense pressure to maintain compliance. The challenges of maintaining ongoing compliance increase as regulations...
Understanding Cyber Threat Intelligence (CTI)
Cyber Threat Intelligence (CTI) is a critical component of modern cybersecurity practices. At its core, CTI transforms raw data into actionable...
Digital Forensics & Incident Response Explained
Digital Forensics and Incident Response (DFIR) is a crucial area in cybersecurity. It involves detecting, investigating, and responding to cyber...
Cybersecurity Use Cases for AI and Machine Learning
In 2024, machine learning (ML) and artificial intelligence (AI) achieved significant advances that altered how several industries see productivity...
Exploring the Innovative Features of iTrust AI Assistant
iTrust is at the frontier of assessment and control of cyber threats. Businesses are provided with accurate cyber risk ratings using modern and...
Cybersecurity Areas Organizations Are Investing In
Many organizations have to juggle budget allocation. Expenditures on operations, marketing, and advertising are commonplace. These areas often take...
Leveraging AI in Cybersecurity with TrustNet
Thanks to Artificial Intelligence (AI), the days of passive approaches to data protection are gone. Imagine a security solution that not only...
Revolutionize Your Security: Unveiling the Power of Next-Gen Cybersecurity Monitoring
The environment of cybersecurity has drastically changed in the past year. As geopolitical and economic changes make the world more difficult and...
Elevating Managed Security Services at MSSPAlertLive 2025
MSSPAlertLive 2025, held on October 14th - 16th at the Hyatt Regency, Austin, TX, was a premier event that converged the managed security providers,...
Future-Proofing Your Business Against Cyber Threats
Imagine this: 61% of organizations are worried that AI-powered attacks could jeopardize sensitive information. It's a daunting thought in today's...
Safeguarding the Digital Economy: A Deep Dive into Fintech Cybersecurity
As the fintech industry continues its rapid growth, companies are redefining how you handle money with innovations like mobile payments and...
Elevate Cyber Defense: GhostWatch’s Cutting-Edge Risk Management Solutions
Organizations today still face a great deal of difficulty protecting their assets in the face of increasingly sophisticated cyber threats. As these...
Managed Security Services: Your Partner in Cybersecurity Defense
As cyber threats become increasingly sophisticated, defending your organization's data demands more than just basic measures — it requires a robust,...
Cybersecurity Monitoring: Your Vigilant Sentinel
Even the most sophisticated security systems are being tested by the increased complexity of cybersecurity threats. There has never been a more...
How GhostWatch Elevates SOC 2 Compliance
Blog GhostWatch by TrustNet is a global leader in security and compliance management. We are excited to delve into the benefits of...
2024’s Cyber Guardians: The Forefront Companies Shaping Cybersecurity Solutions
Blog Security solutions that are proactive and adaptable are more important than ever as cyber criminals grow more skilled. On the...
TrustNet’s Key Takeaways from RSA Conference 2024: AI, Quantum Computing, and More
Blog The RSA Conference 2024 has been a platform for cybersecurity brainstorming and discussions. Hosted at the Moscone Center in San...
Evaluating Cyber Risks: How iTrust Paves the Way for Secure Business
Blog Ratings for cyber risks have become a must-have in the current digital field. It quantifies how secure an organization is and shows...
The Dual Power of GhostWatch: Security and Compliance Unveiled
Blog Lately, there's been a noticeable uptick in cyber threats, and the cunning of hackers and cybercriminals is growing by the day. It's...
Launching a Safer Future: Meet GhostWatch and iTrust – New Solutions from TrustNet
Blog At TrustNet, we lead the way in compliance and cybersecurity and are renowned for our potent and innovative solutions. Our goal is to...
CSIRT Cyber Security: How to Build an Incident Response Team
Blog Network systems and data security are crucial for businesses of any size. While deploying firewalls and other protective measures is...
Managed Security Unveiled: The Ultimate Providers Powering Cyber Defense
Blog Cyber threats loom larger and more sophisticated, and robust cybersecurity measures are more critical than ever. Managed security...
Retail’s Digital Shield: Proven Strategies for Superior Cyber Security
Blog Digital transformation is revolutionizing the retail industry. However, the specter of cyber threats looms larger than ever. With the...
What to Expect at RSA Conference 2024
Blog Every year, business leaders, security professionals, and industry innovators eagerly anticipate the RSA Conference, a pivotal...
Cyber Security Threat Vectors: A Comprehensive Guide on Attack Pathways and Prevention Measures
Blog Cyber security threat vectors are the pathways or methods through which malicious actors gain unauthorized access to systems,...
Cyber Security Posture in 2024: All You Need to Know
Blog Cyber security posture refers to an organization's overall defensive stance against cyber threats, encompassing its policies,...
Blue Team vs. Red Team Cybersecurity: A Comparative Study of Defensive and Offensive Strategies
Blog Blue Team and Red Team operations represent the dual facets of cybersecurity practices aimed at fortifying an organization's...
Navigating the Complex World of Cyber Security Audit and Compliance
Blog As organizations increasingly rely on digital technologies to conduct their operations, safeguarding sensitive information and...
Compliance Without Complications: GhostWatch’s Managed Compliance Solutions
Blog Compliance in cybersecurity presents a myriad of challenges for businesses. The landscape constantly evolves, with new threats and...
Your Compliance, Our Commitment: Introducing GhostWatch Managed Compliance
Blog In today’s ever-changing technology landscape, companies face dynamic laws and regulations that they must adhere to, often with...
GhostWatch Managed Security: Vigilance Redefined
Blog With the world become more linked, there is an exponential increase in the demand for strong security measures to defend against more...
24/7 Monitoring with GhostWatch: What It Means for Your Business
Blog For businesses of all sizes, ensuring 24-hour security has become essential. In order to prevent risks from becoming serious...
New Solutions in Cybersecurity: Navigating the Surge of AI-Assisted Threats in 2024
Blog The cybersecurity landscape in 2024 is expected to be increasingly complex and multifaceted. With the advancement of technology,...
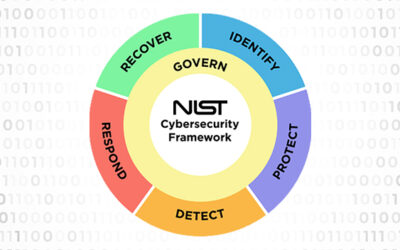
NIST CSF 2.0: What’s New
Blog Established in 2014, the National Institute of Standards and Technology Cybersecurity Framework (NIST CSF) is a vital tool in the...
Launching a Safer Future: Meet GhostWatch and iTrust from TrustNet
Blog TrustNet is a cybersecurity and compliance industry leader renowned for innovative and robust solutions. We are dedicated to...
The Dual Power of GhostWatch: Security and Compliance Unveiled
Blog With the rise in cyber threats and the growing sophistication of hackers and cybercriminals, businesses globally are realizing the...
Coming Soon: Exciting New Solutions from TrustNet in 2024
Blog As we usher in a new year, TrustNet continues its unwavering commitment to innovation in cybersecurity. With an established track...
5 Key Takeaways from the 2023-2024 CISA Roadmap for Artificial Intelligence
Blog The "2023–2024 CISA Roadmap for Artificial Intelligence" is a strategic guide outlining the Cybersecurity and Infrastructure Security...
TrustNet’s 2023 Journey: Celebrating Our Growth and Successes in Cybersecurity
Blog In 2023, TrustNet marked an impressive year of growth and success in the dynamic field of cybersecurity. This year's milestones are a...
Overcoming Cyber Threats: How Businesses Triumphed in 2023
Blog The cybersecurity landscape of 2023 was a battleground, constantly shifting and evolving. Businesses rallied, adapted, and overcame...
Planning for 2024: Leveraging a Managed Security Platform for Business Growth
Blog As we enter 2024, businesses are increasingly pivoting towards a digital-first approach. While offering numerous opportunities for...
Educational Institutions Also Need To Pay Attention To Cybersecurity, Here’s Why
Blog The Education Cybersecurity Summit 2023 took place in New York City on December 8, 2023. This event allowed technology professionals...
Looking Back: Key Cybersecurity Lessons from 2023
Blog As we bid farewell to 2023, it's clear that the year has been a formative one in the realm of cybersecurity. The landscape has never...
Enhancing Security through Adaptive Multi-Factor Authentication: A TrustNet Perspective
Blog In the ever-evolving landscape of cybersecurity, the need for robust authentication mechanisms has become paramount. Traditional...
The Growing Threat of Phishing Attacks: Preparing for 2024
Blog As we move forward into the future, the threat of cyber attacks looms more prominent than ever. Among these, phishing attacks are a...
Peering into the Future: TrustNet’s Vision for Cybersecurity in 2024
Blog TrustNet, a leading global provider of cybersecur services span managed security, consultingity and compliance services since 2003....
The Rise of AI in Cybersecurity: Expected Developments in 2024
Blog Artificial Intelligence (AI) has become an instrumental tool in cybersecurity. As we stand at the tail end of 2023, AI has already...
Predicting the Future: Top Cybersecurity Trends for 2024
Blog Key Takeaways This article provides valuable insights for cybersecurity professionals, IT decision-makers, business executives, and...
Cybersecurity in Accounting: The Shield for Client Data
Blog As custodians of sensitive financial information, accounting firms increasingly find themselves in the crosshairs of cybercriminals....
TrustNet: Your Ally in Achieving Cybersecurity Compliance
Blog In an era where digital threats are ever-evolving, TrustNet emerges as a trusted partner committed to fortifying your cybersecurity...
How Does Open Source Data Change The Cyberdefense Game (Open Source Data Summit 2023)
Blog The Open Source Data Summit 2023 was a live virtual summit held on November 15th, 2023. This premier event united open-source...
TrustNet Congratulates iWave For Their Recent Acquisition of NonprofitOS
Blog iWave, one of the industry's top-rated fundraising intelligence providers, recently announced their acquisition of Nonprofit...
Cybersecurity and Business Reputation: An Indivisible Duo
Blog In today’s highly digitized business landscape, the strength and effectiveness of a company's cybersecurity measures can...
TrustNet Congratulates Logistics Plus for Global Trade Recognition
Logistics Plus, Inc., a global leader in transportation, logistics, and supply chain solutions, has been named one of America’s top third-party logistics providers by Global Trade magazine.
Year-round Monitoring and Tracking: Key to Effective Cybersecurity
Blog Cybercrime happens round-the-clock. So should cybersecurity. Year-round monitoring and tracking enables organizations to proactively...
The Power of Global Community in Threat Research and Security Innovation
Blog Cybercrime is a global problem that requires a global response. No organization or country — however powerful — can face the...
TrustNet team attends RSA Conference 2023: Our Impression and Thoughts
TrustNet team attends RSA Conference 2023 to stay ahead of cybersecurity, receive awards, and decipher Frisco’s charms Every year since 1991, IT...
Log4j Attack Surface Remains Massive
Four months ago, the remote code execution hole exposed in the Apache Log4j logging tool still had a wide range of potential victims. Using the...
Most Email Security Approaches Fail to Block Common Threats
Blog On a scale of one to ten, where ten is the maximum effectiveness, most security teams give their email security systems a rating of...
Former Uber Chief Security Officer To Face Wire Fraud Charges because of Failed Cybersecurity
Over the past few years, the road has not been smooth for former Uber Chief Security Officer Joseph Sullivan. On December 21, 2021, three additional...
Top Managed Security Services Company 2021
Even after more than a year into the pandemic, the business world is still struggling to address the cybersecurity challenges that it has...
Virtual CISO: All You Need to Know
Security and protection from external threats have become even more important than ever. The growing number of cyberattacks indicates that even...
Cybersecurity Consulting Services
Blog What is Network Penetration Testing? Network Penetration Testing is a type of service performed by a penetration testing network. It...
SIEM Log Management and Managed SIEM Service
TrustNet Managed SIEM Detecting intrusions and other abnormal security events that impact your networks is the function of a group of integrated...
Cybersecurity Monitoring Service
TrustNet Cyber Security Monitoring Services Shielding your customers' sensitive data and the network ecosystems where it resides must be one of your...
Red vs. Blue Team Security
Blog Hackers and other cybercriminals are pulling out all the stops, mounting a stunning array of increasingly sophisticated attacks on...
Vulnerability Management Program
Today’s multi-layered information systems make it possible for companies like yours to store, manage, and transmit data like never before. However,...
Next Generation Endpoint Security
Storing, transmitting, and managing data is one of the primary support tasks that many organizations perform in today’s digital corporate landscape....
SOC for Cybersecurity
Blog Managing customer data and exchanging digital information on a global level provides your organization with both unparalleled...
Compliance vs Security
An organization must constantly be on guard against external network attacks, threats from its own staff and third-party vendors and even fatal...
Qualitative vs. Quantitative Risk Assessments in Cybersecurity
Blog Assessing the risks within your cybersecurity system is one of the key priorities to address when conducting an ISO 27001 project or...
Cyber Threat Hunting
Your company’s network is a complex environment managed by many moving parts. That makes detecting intruders a constant challenge. The truth is that...
Security Patch Management Best Practices
One indisputable fact about today’s software and firmware is that change is inevitable. When vulnerabilities or bugs are discovered or an upgrade is...
Data Security Strategy
When you are on the front lines charged with the critical duty of ensuring that your company’s information and systems are as protected as possible...
Information Security Audit Checklist
Blog Having a robust cybersecurity infrastructure isn't just a luxury—it's a necessity. Because cyber risks are ever-changing, it takes...
FFIEC Cybersecurity Assessment Tool
The Federal Financial Institutions Examination Council (FFIEC) is a governmental body made up of five banking regulators. Its objective is to...
Red Flags Rule Compliance Tips
Identity theft takes a massive toll on millions of Americans each year. It also has a devastating financial effect on the merchants and credit...
Massachusetts Data Security Laws
Regardless of where you do business in the United States, you already know that the security of your stored and transmitted private data is of...
Artificial Intelligence in Cyber security
Blog Without artificial intelligence (AI), we would not have speech recognition technology such as Siri, search engines like Google or...
AWS Penetration Testing
Blog Amazon Web Services (AWS) platform supports a wide variety of business activities that include data storage, web application...
Information Security Program
Any management or human resource professional knows that standards and practices can never be truly implemented and enforced unless and until they...
Security Maturity Model
There are two complementary objectives of any cybersecurity operation. Tools both automated and human must be in place to monitor network systems,...